PCI DSS Preparedness
Accepting credit cards? A single data breach can cripple your business. PCI DSS compliance ensures robust security, safeguarding sensitive information and keeping your customers' trust.
Fill out the form below to speak with a WeSecureApp compliance specialist
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) was created by the Payment Card Industry Security Standards Council (PCI SSC). The Council was founded in 2006 by American Express, Discover, JCB International, MasterCard, and Visa Inc. They share equal responsibility in ownership, governance, and execution of the Council’s work. The Payment Card Industry Data Security Standard (PCI DSS) was developed to encourage and enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally. The PCI Security Standards Council is not a compliance organization. They do not require compliance, but individual payment networks may.
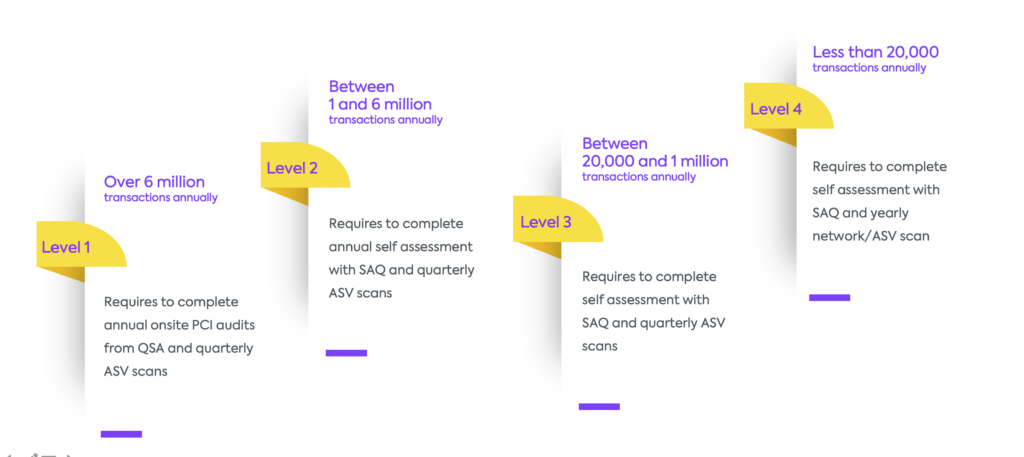
Merchant levels in PCI-DSS: Which level do you fit in?
Merchant levels determine the amount of assessment and security validation that is required for the merchant to pass PCI DSS assessment. There are several merchant levels, each with a slightly different list of requirements, and largely determined by the number of transactions processed each year. The Payment Card Industry (PCI) uses merchant levels to determine risk and ascertain the appropriate level of security for their businesses. Specifically, merchant levels determine the amount of assessment and security validation that is required for the merchant to pass the PCI DSS assessment. At an extremely high level, the PCI DSS merchant levels are as follows:
Compliance confusing? We make it simple, no more losing! Talk to us.
How you submit your compliance is dependent on your merchant level
If your organization falls with the definition of Level 1 for merchants and service providers, you are required to submit compliance documents produced by a Qualified Security Assessor (QSA). They will then produce a report on compliance detailing the 12 requirements. Lower-level organizations may only require a Self-Assessment Questionnaire (SAQ) to be completed and submitted. SAQs are validation tools designed to assist organizations in self-evaluating their compliance with PCI DSS
12 PCI DSS Requirements
-
01
Install and maintain a firewall configuration to protect cardholder data. -
02
Do not use vendor-supplied defaults for system passwords and other security parameters -
03
Protect stored cardholder data. -
04
Encrypt transmission of cardholder data across open, public networks -
04
Protect all systems against malware and regularly update anti-virus software or programs -
05
Develop and maintain secure systems and application -
07
Restrict access to cardholder data by business need to know -
08
Identify and authenticate access to system components -
09
Restrict physical access to cardholder data -
10
Track and monitor access to network resources and cardholder data -
11
Regularly test security systems and processes -
12
Maintain a policy that addresses information security for all staff

Methodology
Phase 1:
Information Gathering, Scoping and Gap Analysis
- Project planning and Kick-Off meeting.
- High-Level organization understanding.
- Identify information infrastructure and define the scope of PCI-DSS.
- Assess control gaps with respect to 12 requirements of PCI-DSS.
Phase 2:
Security Assessment
- Perform risk assessment .
- Vulnerability Assessment and Penetration Testing of the infrastructure and applications in scope LAN segmentation testing.
- Conduct firewall rule set review.
Phase 3:
Remediation of Risks and Implementation of Controls
- Consult the client for implementation of required controls identified during Gap analysis and Risk assessment.
- Conduct PCI-DSS awareness training.
- Modify or create policies according to PCI-DSS requirements.
Phase 4:
Certification Support
- Help the Client to find the correct QSA to ensure that he/she has experience in your industry and the necessary knowledge to validate the controls and should be able to articulate the key details for your environment.
- Conduct a pre-audit to validate if all the requirements are covered .
Benefits of PCI DSS Compliance
PCI Compliance means that your systems are secure, and your customers can trust you with their sensitive payment card information; trust leads to customer confidence and repeat customers.
PCI Compliance improves your reputation with acquirers and payment brands – just the partners your business needs.
PCI compliance means you are contributing to a global payment card data security solution.
PCI Compliance likely leads to improving IT infrastructure efficiency.
Meeting PCI Compliance, you’re better prepared to comply with additional regulations, such as HIPAA, SOX, and others.
Recent hacks
WannaCry: Ransomware attack(2017)
Affected more than 200,000 computers across 150 countries, with damages ranging up to billions of dollars.
Boston Children’s Hospital DDoS attack (2016)
DDoS attack led to donations page being shut down and an estimated 300,000 dollars lost in repairs.
Risk of “medjacking”
The security flaw that researchers discovered in General Electric respirators and anaesthesia machines.

Accepting payments? WeSecureApp ensures your PCI DSS compliance is airtight.
Frequently Asked Questions
Hefty fines, reputational damage, and worst of all – angry customers.
Yes, PCI DSS mandates regular vulnerability scans to identify security weaknesses. Additionally, penetration testing simulates real-world attacks to assess your system’s overall resilience.
The scope defines which systems and data fall under PCI DSS. It depends on the number of transactions you process annually. WeSecureApp can help you identify your scope and tailor a compliance plan accordingly.
Non-compliance can lead to significant financial penalties, card network sanctions, and even termination of processing privileges. WeSecureApp helps you achieve and maintain compliance to avoid these risks.
Costs vary based on your transaction volume and the complexity of your environment. WeSecureApp offers flexible solutions to optimize compliance efforts and minimize expenses.




