- Services
- Solutions
- Compliance
- [Column]
- REGULATORY COMPLIANCE
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit for Data Localization
- [Column]
- [Column]
- [Column]
- Resources
- Company
- Company










Know DevSecOps
While organizations continue to adopt, expand, and perfect their DevOps game, malicious attacks on applications are on the rise. Enterprises are realizing that the risks of slack security remain real, immediate, and extremely costly. This puts DevOps outfits under pressure to implement stronger and smarter security measures.
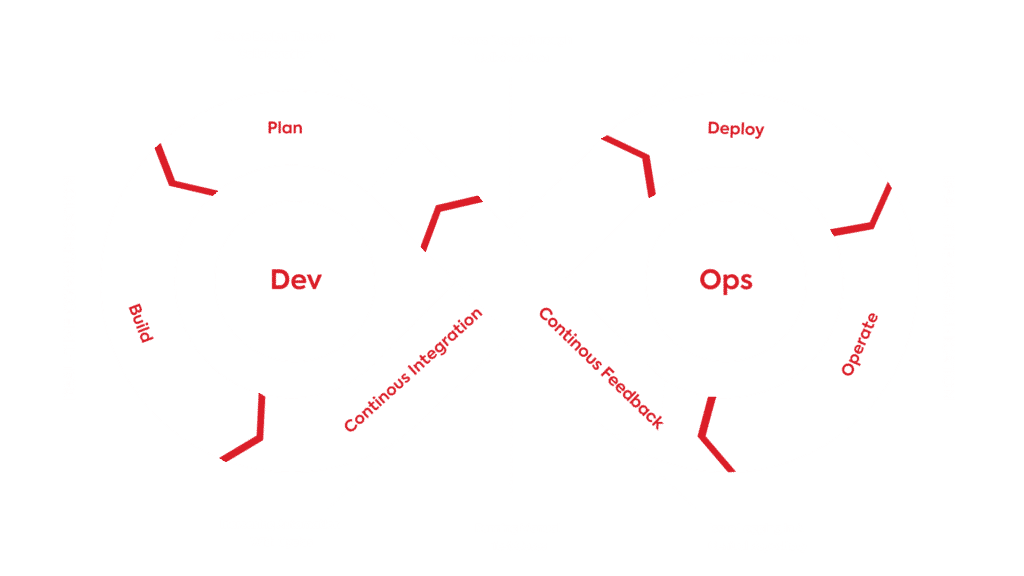
Introducing security into the existing DevOps without hampering the speed of development is called DevSecOps.
Introducing security into the existing DevOps without hampering the speed of development is called DevSecOps.
Our Research

Pay 10x more
Companies who fix bugs in production

70%
Engineers make common mistakes

100 Hours
Time spent by engineers fixing bugs in production
Managed Services
1
Application Pentesting
Perform a thorough analysis of your application to uncover OWASP and business logical vulnerabilities that are not easily discovered by scanners.
2
Web Services Pentesting
Run a pen-test on your web services to uncover authentication and authorization related issues.
3
Training on Secure Coding Practices
Custom generated training programme based on vulnerability history and tech stack for developers and engineers.
4
Triage
Validate and help engineering teams to fix vulnerabilities discovered from automated
scans.
This solution helps you achieve
Continuous application vulnerability scanning
Visibility into the application security posture
Easier collaboration between stakeholders
Continuous feedback on cloud and containers
Detect & prevent attacks, before they succeed.
Stay ahead of the rapidly evolving threat landscape and keep your data protected without having to spend a fortune.

Integrated tools
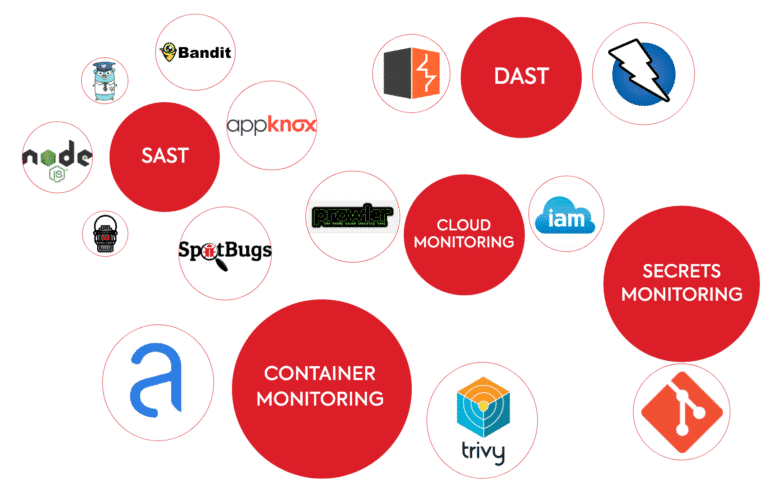
DevSecOps Solutions
We help you build security workflows!
We help you solve this very complex and challenging puzzle of understanding your current DevOps process and tools used. We use security tools and managed services by making sure to keep up with dynamic and fast-paced environments.




