A simple entry point can lead to Server Compromise
During a web application penetration project, our team has exploited a simple bug that can turn into remote code execution to the main server.
Recently our team escalated a straight forward template injection to a Remote Code Execution and compromised the server.
1) Starts with recon
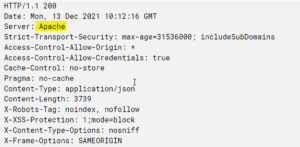
In the first stage of the project, our team identifies some information about the web application. It seems like the web application is a kind of email service providing an application that runs on an Apache server. Also, we discover that JavaScript and some libraries were used by the developers during the application development.
2) Understand the functionality
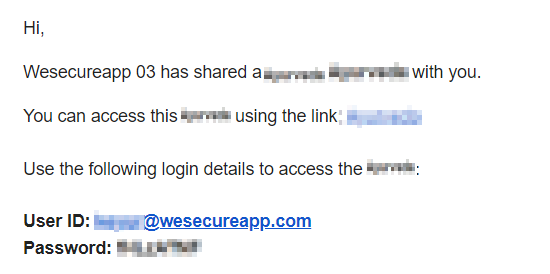
In the given application there is a function for admin users to send mail to other users. Actually, when the admin creates some predefined email templated with some fixed mail body, Admin can invite another user to use this email template for the further process. Here admin has two options for sharing that email template, either admin can make the template public and invite any user or can make the template private and invite-only selected user. Here the private template can be accessible with the help of an email id and password which were shared by the admin via mail.
3) Exploiting entry points for Server-side template injection(SSTI)
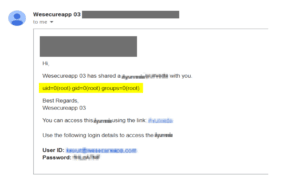
So our team starts to test the function, we have created one custom email template and shared the link with the user. While sending the link to the user via email we observed that the application uses some function named “${externalShareableInfo}” to retrieve the credentials and merge this function into the email body along with other text like shown below
![]()
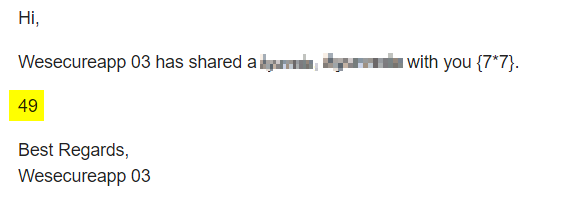
As an attacker we try to play with this given function, we replaced the function with some Mathematical calculation like “${7*7}”, and boom the calculation part was executed by the backend. So as a result we get 49 as output into the email body. This type of attack is called “Server-Side Template Injection” where an attacker can insert some script which executed by the backend
4) Further exploits SSTI to Remote code execution
Now it’s time to get some more results via SSTI. During recon, we identify that the backend server is Apache and the scripting language is Java. So our team starts to recon more about the template. After some trial and error methods, we discover that the web application is using a freemarker java template for the mailing function.
Our team has injected free maker template code into the SSTI payload. The payload was ${\”freemarker.template.utility.Execute\”?new()(\”id\”)}. As we expected we have successfully executed “id” command on the backend server the successfully get the output in the email body. Here we have exploited SSTI to RCE
This is how an attacker can exploit simple bugs into remote code execution and can execute malicious commands on the server which can lead to data breaches or other sensitive information disclosure.
Want a quick demo on web application penetration testing – Talk to Our Delivery Head

About Author
Keyur Talati
Security Analyst – WeSecureApp