- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
AWS Penetration Testing | Amazon Cloud Security
Migrating your business to the Amazon Web Services (AWS) cloud can be a game-changer, offering scalability, flexibility, and cost-efficiency. But hold on a second! Just like a shiny new car needs insurance, your AWS environment needs robust security measures. Here’s where AWS penetration testing comes in—it’s like a stress test for your cloud defenses, exposing vulnerabilities before those pesky hackers do.
This article is your one-stop shop for understanding AWS penetration testing, even if you’re a complete cloud newbie. We’ll break down the what, why, and how, so you can ensure your AWS castle remains firmly in your control.
Understanding Security Assessments in the AWS Context
A security assessment encompasses any activity designed to evaluate the effectiveness and presence of security controls within your AWS resources. This includes vulnerability scanning, penetration testing, port scanning, exploitation attempts, web application assessments, and various injection, forgery, and fuzzing techniques. These assessments can be executed remotely against your AWS assets, internally between them, or locally within virtualized environments.
Freedom in Tool Selection with Responsibility
AWS grants you flexibility in choosing security assessment tools and services. Public, private, commercial, and open-source options abound to suit your specific requirements. However, this freedom comes with the crucial responsibility of ensuring these tools comply with AWS’s security guidelines.
Key AWS Security Areas for Impenetrable Pentesting
Four key areas of AWS security that pentesters should meticulously assess: Identity and Access Management (IAM), Logical Access Controls, S3 Buckets, and Database Services.
- Identity and Access Management (IAM)
IAM serves as the cornerstone of AWS security, dictating who can access what within your cloud realm. Here’s how to fortify this critical layer:
- Unrestricted Service Account Permissions: Service accounts are identities used by AWS services to interact with other services. Test for accounts with excessive permissions, as these can be exploited by attackers to gain undue access.
- Root Account Keys: The root account possesses ultimate power within your AWS environment. Ensure no permanent root account keys exist – they should only be used for initial setup and then disabled. Rely on temporary credentials for routine tasks.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring a second authentication factor beyond just a username and password. Test to ensure MFA is mandatory for all users with AWS access.
- Logical Access Controls
Logical access controls determine how users and applications interact with AWS resources. Here’s how to tighten these controls:
- Action Assignment: Ensure that actions (permissions to perform specific tasks on resources) are correctly assigned to the appropriate users and groups. Granular control is key – users should only have the minimum permissions required for their tasks.
- Safeguarding Credentials: Credentials (usernames and passwords or access keys) are the keys to the kingdom. Test for weak passwords, inactive accounts with lingering access, and shared credentials. Implement strong password policies and rotate credentials regularly.
- Limiting Access to Sensitive Resources: Certain resources, like databases containing sensitive data, require stricter access controls. Test to ensure only authorized users can access these resources, and consider implementing additional security measures like encryption at rest and in transit.
- S3 Buckets
S3 buckets are a popular storage solution within AWS. However, misconfigured buckets can expose sensitive data. Here’s how to ensure your S3 buckets are impenetrable:
- Enabling Security Features: AWS offers a variety of security features for S3 buckets, including Server-Side Encryption with S3 Key Management Service (SSE-KMS) and bucket access controls. Test to ensure these features are enabled and configured appropriately.
- Restricting User Permissions: Just like IAM users, S3 buckets have access control lists (ACLs) that dictate who can access them. Test to ensure only authorized users have the necessary permissions (GET, PUT, DELETE) to interact with your S3 buckets.
- Auditing Bucket Activity: Enable S3 bucket logging to track user activity and identify any suspicious access attempts. Look for features like object-level versioning, which allows you to revert to previous versions of objects in case of accidental modification or deletion.
- Database Services: Protecting the Crown Jewels
Databases often house your most valuable information. Here’s how to safeguard them during your AWS odyssey:
- Restricting Database Access: Database access should be granted on a least-privilege basis. Test to ensure only authorized applications and users can connect to your databases. Consider using whitelisting to further restrict access.
- Secure Coding Practices: SQL injection and other code vulnerabilities can provide attackers with a backdoor into your databases. Test your application code for vulnerabilities and enforce secure coding practices to prevent such attacks.
- Robust Backups and Recovery: Regular database backups are essential for disaster recovery. Test your backup and restore procedures to ensure you can swiftly recover your data in case of an incident. Consider deploying your databases across multiple availability zones for enhanced resilience against outages.
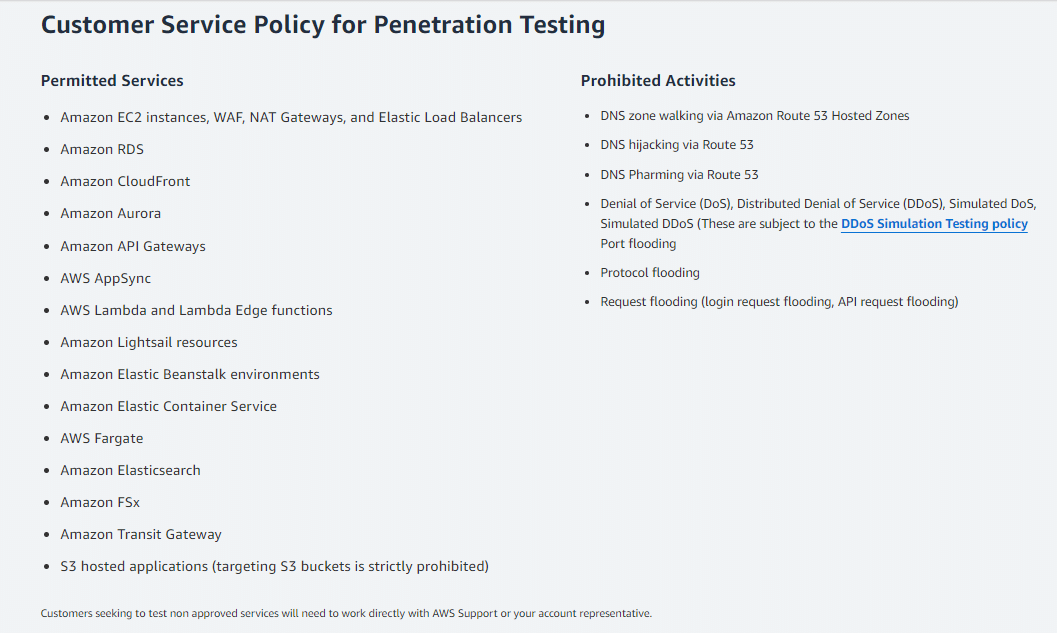
Source- https://aws.amazon.com/security/penetration-testing/
AWS Penetration Testing Methodology
AWS pentesting methodology follows a similar approach to general penetration testing, but with a focus on the specific vulnerabilities and configurations of the AWS cloud environment. Here’s a breakdown of the typical phases:
1.Preparation and Planning
- Understanding the Scope: This involves defining what systems and resources will be tested within the AWS environment.
- Authorization: Obtaining proper permissions and access credentials to conduct the testing without causing disruptions.
2. Information Gathering (Reconnaissance)
- Identifying Services: Mapping out the AWS services being used, like S3 buckets, EC2 instances, and IAM roles. Tools like AWS Security Token Service (STS) can be helpful here.
- Enumerating Resources: Finding details about the discovered services, such as configurations, access controls, and potential misconfigurations.
3. Vulnerability Assessment and Exploitation
- Identifying Weaknesses: Looking for exploitable vulnerabilities in the AWS services and configurations. This might involve using automated tools for scanning along with manual testing.
- Exploitation: Attempting to exploit the discovered vulnerabilities to gain unauthorized access or escalate privileges within the AWS environment.
4. Post-Exploitation and Maintaining Access
- Privilege Escalation: If an initial foothold is gained, the pentester will try to elevate privileges to access more critical systems and resources.
- Lateral Movement: Moving around the AWS environment to compromise other resources and establish persistence (maintaining access even after the pentest).
5. Reporting and Remediation
- Documenting Findings: Creating a detailed report listing the identified vulnerabilities, their potential impact, and recommended remediation steps.
- Remediation and Validation: Working with the AWS owner to fix the vulnerabilities and verifying that the remediation efforts are effective.
Additional Considerations for AWS Pentesting
Penetration testing (pentesting) for AWS environments requires a keen eye for detail and a nuanced understanding of the cloud platform’s security landscape. While the core principles of pentesting remain similar, AWS introduces a unique shared responsibility model and a heavy reliance on Identity and Access Management (IAM). This intro dives into these distinguishing factors, along with exploring the potent tools AWS offers to empower pentesters.
- Shared Responsibility Model:
- AWS Responsibilities: AWS is responsible for the security of the underlying cloud infrastructure. This includes physical security of data centers, network security, and the overall health of the platform.
- Customer Responsibilities: Customers are responsible for securing their own data and configurations within the AWS environment. This includes securing IAM roles, S3 buckets, EC2 instances, and other resources they use.
- Focus of Pentesting: During an AWS pentest, the focus should be on identifying vulnerabilities in the customer’s configuration and practices. This might include:
- Weak IAM policies with excessive permissions.
- Misconfigured S3 buckets with public access.
- Unsecured EC2 instances with open ports or weak credentials.
- Focus on IAM:
- IAM Core Concepts: IAM is the foundation for access control in AWS. It allows you to define users, groups, roles, and policies to manage who has access to what resources and what actions they can perform.
- Pentesting IAM: A thorough AWS pentest should include a deep dive into IAM configurations. Here’s what to look for:
- Overly Permissive Policies: Are IAM policies granting more access than necessary? This can lead to privilege escalation if an attacker gains access to a lower-privileged account.
- Unused or Inactive Users and Roles: Are there any unused or inactive accounts or roles that could be exploited by attackers?
- Multi-Factor Authentication (MFA): Is MFA enabled for all critical accounts to add an extra layer of security?
- Utilizing AWS Tools:
AWS offers a variety of tools and services that can be leveraged during a pentest to improve efficiency and effectiveness. Here are some key examples:
- AWS Security Hub: This centralizes security findings from various AWS services and partner security products. It can help pentesters identify potential vulnerabilities across the entire AWS environment.
- Amazon Inspector: This automated service helps identify security vulnerabilities in Amazon EC2 instances. It can be used to scan instances for common misconfigurations and software vulnerabilities.
- AWS Config: This service continuously records and delivers the historical configurations of your AWS resources. Pentesters can use it to identify changes made to configurations and detect potential security drifts.
- AWS CloudTrail: This service records AWS API calls and related events. Pentesters can use CloudTrail to track activity within the AWS environment and identify suspicious behavior.
WeSecureApp AWS Penetration Testing
Don’t navigate AWS penetration testing alone. Partner with WeSecureApp for a security assessment that goes beyond the surface. The team of AWS security veterans brings unparalleled expertise and a proven track record to the table. They leverage an offensive security mindset to uncover even the most cleverly hidden vulnerabilities, acting like attackers to expose weaknesses before real threats emerge. WeSecureApp doesn’t just deliver a report and leave you hanging. We collaborate with you to develop a clear remediation plan, prioritizing critical fixes and ensuring your AWS environment is effectively patched. All of this is delivered with a focus on ROI, maximizing the value of your investment in security.
Ready to see how WeSecureApp can fortify your AWS cloud defenses? Schedule a free consultation today to discuss your specific needs and explore how their expert penetration testing services can safeguard your valuable data and resources. You’ll gain valuable insights into your current security posture and discover how WeSecureApp can help you achieve a more robust and secure AWS environment. Visit their website or contact them directly to book your free consultation – it’s the first step towards a more secure cloud future.
FAQs on AWS Penetration Testing
Q: Will a penetration test disrupt my AWS environment?
A: Well-planned penetration testing should have minimal impact on your AWS environment. However, it’s always a good idea to discuss this with your pen testing partner beforehand.
Q: How much does AWS penetration testing cost?
A: The cost of penetration testing can vary depending on the size and complexity of your AWS environment, as well as the scope of the testing.
Q: Can I do my own AWS penetration testing?
A: It’s certainly possible, but it requires a deep understanding of AWS security and penetration testing methodologies. Unless you have a seasoned security professional on your team, it’s generally recommended to engage a qualified pen testing company.
Q: Do I need permission from AWS to conduct a pen test?
A: Thankfully, no! AWS https://aws.amazon.com/security/penetration-testing/ allows customers to conduct security assessments without prior approval for a list of approved services. However, there are some restrictions, so be sure to check the AWS Security Testing Terms and Conditions.
Q: How much does a pen test cost?
A: The cost of a pen test can vary depending on the size and complexity of your AWS environment, as well as the scope of the test. However, there are options to fit most budgets.
Q: Can I do the pen test myself?
A: While it’s technically possible, it’s not recommended for beginners. Pen testing requires specialized skills and knowledge. Consider hiring a reputable security firm with experience in AWS penetration testing (https://aws.amazon.com/security/penetration-testing/).
Q: What happens after the pen test?
A: Once the pen test is complete, you’ll receive a report outlining the vulnerabilities found. It’s crucial to prioritize these findings and fix the most critical ones first. Here’s where your chosen security firm can be invaluable – they can help you develop a remediation plan and ensure your AWS environment is secure.
Recommended Reading
Cloud Pentesting 101: What to Expect from a Cloud Penetration Test?
The Only API Penetration Testing Checklist You Need
Penetration Testing Across Industries: Requirements and Assessment Scope