Emerging Cybersecurity Challenges to Get Ready in 2022
The advancement of technology has gradually increased the volume and range of cyberattacks, requiring new strategies and initiatives to fight them. In 2021, the United States Cyber Command entrusted with engaging in cyberspace, which means that the fight against cyber-terrorism has become one of the main priorities of the US.
Until now, the most widespread and dangerous cyber threats were Over Air (OTA) attacks, which exploit wireless communication to gain access to devices and control them. However, we will see the development of new technologies that scientists worldwide are currently studying.
This article presents the top crucial challenges that will have to be resolved in 2022.
So, let’s get started.
1. Mobile Banking Malware: Common on the streets of London
At first glance, this seems to be a massive challenge for all those afraid of ATM Skimming. However, new techniques are being developed to allow criminals to steal money from bank accounts through smartphones and tablets.

Mobile banking malware is similar to its predecessor as it exploits devices’ vulnerabilities to steal banking credentials, credit card numbers, and other sensitive user data. If successful, cybercriminals can empty your bank account in half an hour. Therefore, this is one of the most dangerous challenges banks will face in 2022.
2. Cryptocurrency: a Digital Safe Haven for Cybercriminals
The cryptocurrency system is decentralized and anonymous, so it’s used by hackers and criminals as a haven to store stolen money. Hackers will no longer be required to launder their dirty money through third parties using bitcoin exchanges, as they can now simply transfer their funds directly to the cryptocurrency network.
3. The IoT Centralized Database: A Target for Cybercriminals
The Internet of Things (IoT) is growing exponentially and becoming more and more common among people worldwide who use it for their everyday activities. However, such an uncontrolled growth of IoT devices creates a potential security threat to information systems.
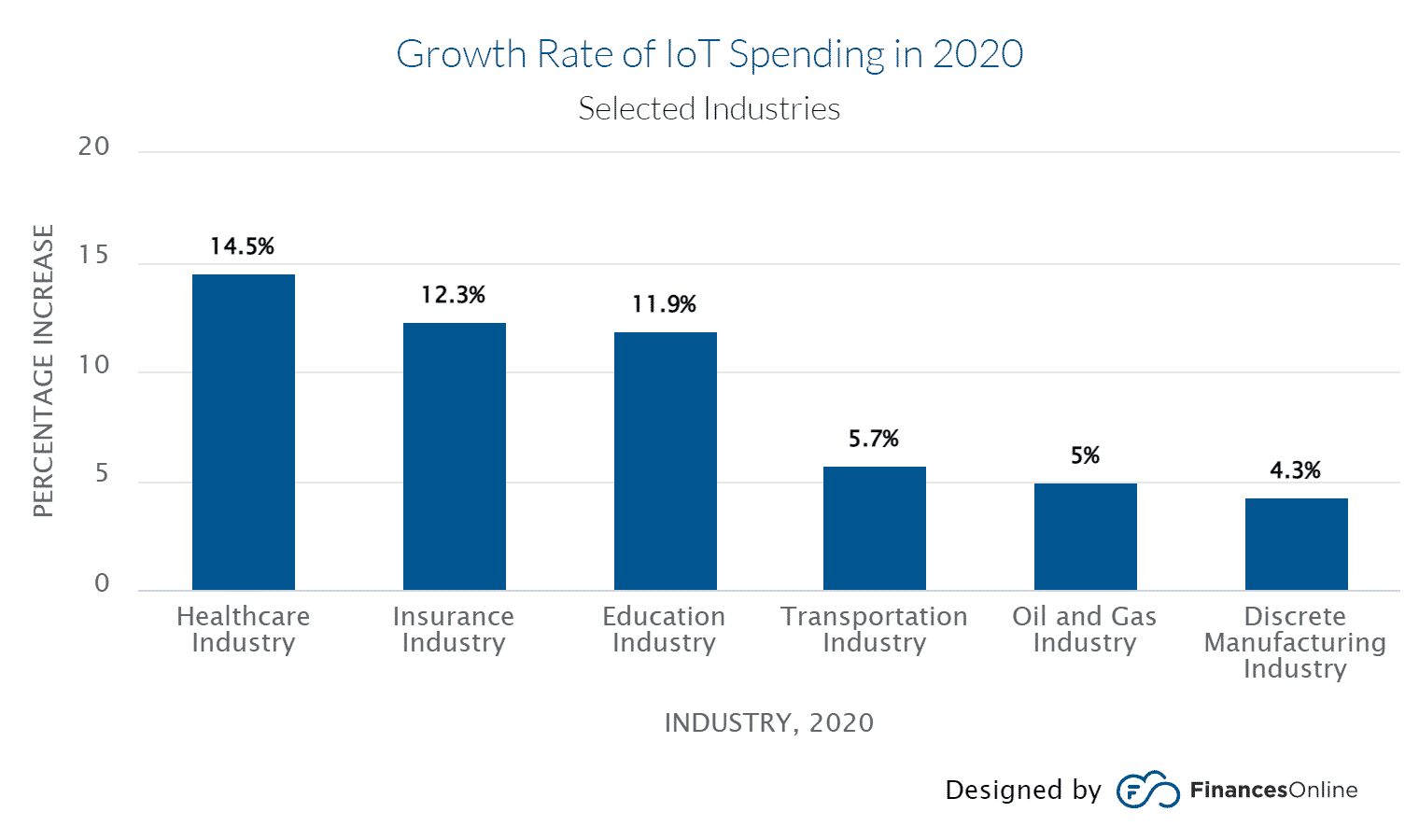
There is always a risk that the databases of embedded devices will be hacked and manipulated, leading to serious security breaches. Moreover, such incidents can affect more than one database at once.
4. The Rise of “Chronicles” Malware: A New Type of Cyber Threat
Chronicles are the daily logs of data collected by cybercriminals while infiltrating different databases. Therefore, Chronicles serves as a trail for an investigation through which security experts can track down hackers’ identities and reveal their motives.
However, this may also open up new opportunities for criminals who use chronicles to help them find flaws in the design of various information systems. The Chronicles malware is designed to infect critical servers and databases, stopping their normal operation until cybercriminals receive a ransom or when they are paid for revealing the location of vulnerabilities.
5. Satellite Communications: A New Target for Cyber-Terrorists
Unlike traditional communication channels, satellite communications are not protected by any firewall or antivirus software, so they are especially vulnerable to cyberattacks.
In the future, the increased popularity and availability of satellite-based communication systems will attract more and more people to take advantage of them. This means that satellites will become an easy target for cybercriminals who want to send a message to the whole world with one click or hold all global communications hostage for ransom.
6. Deepfake Technology-Based Manipulations: A New Challenge for Our Experts
The future is similar to the movie “Inception,” where we will face new technologies that create fake videos and photos of people, so any person’s image can be transferred onto another body and appear in different locations.
Our society has always been able to detect these manipulations, but they won’t be able to do that in the future. This may even lead to the loss of trust among people, as they will have no way of knowing whether they are being manipulated or not.
7. The Coming Wave of Personalized AI-Powered Cyber-Attacks
Most AI cybercriminals use machine learning techniques that allow them to improve their attacks by using artificial intelligence.

Unlike regular cyber-attacks, personalized AI-powered cyberattacks can detect the victim’s individual weaknesses (e.g., dislikes, hobbies, etc.) and target them more precisely. Moreover, it will be much harder to identify these attacks because the number of different variants sent to each person will increase exponentially.
8. The Expansion of the Darknet Market: A Challenge for Online Security Experts
A darknet is an area of the Internet that cannot be accessed by search engines and where user web traffic is isolated via specific software, thus creating a “dark” network that can only be accessed with particular tools.
The number of users who access the Darknet is constantly growing, becoming more popular even among ordinary people. The darknet market offers illegal products and services to everyone globally, thus allowing cybercriminals to expand their activities without being noticed by law enforcement agencies.
9. 5G Networks: A New Challenge for Our Society
The 5G network will be a giant leap forward regarding Internet speed and bandwidth, presenting a new security challenge.
Currently, 4G networks use symmetric encryption algorithms that require the same key to encrypt and decrypt data. However, in the case of 5G networks, we will need to use asymmetric encryption algorithms, which will create a new risk because of their complexity.
10. Internet Addiction: A Challenge for Our Society
Internet addiction has many different influences on our society, but the most disturbing effects don’t do with web browsing itself. Instead, online games and social media networks are gradually becoming a source of problems for people.
However, no one knows the long-term effects of too much time spent on social media, so we can’t say that it’s an addiction problem until research data confirm that.
11. Cloud Computing: A New Threat to Security
Cloud computing is the next step in storing and accessing data, presenting many challenges.
Nowadays, most companies store their information on cloud-based servers, which means that they can access it anywhere globally with an Internet connection. However, this also leaves them more vulnerable to attacks since hackers can access their data remotely.
12. Social Engineering Threats: A Challenge for Our Security Experts
Social engineering is a technique that cybercriminals use to trick users into performing actions that harm their security.
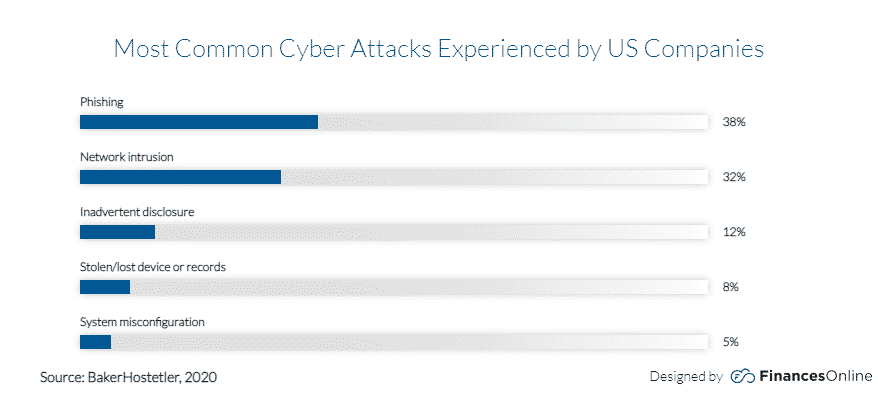
Most spam messages and phishing scams result from social engineering attacks, and we may experience an increase in these types of threats in the future. It will be one of our society’s biggest challenges, as it will be even harder to protect our identities online.
Conclusion
As you can see, the future of our society is constantly threatened by new and evolving cyber threats. Make sure to educate yourself about these issues to overcome them using proper security measures for your digital devices and networks.
New and evolving cyber threats constantly threaten the future of our society. So, educate yourself about these threats and protect your digital devices and networks. More details contact us
Try the Product:
Strobes – Vulnerability Management Platform