Top 8 Significant Cyber Attacks on Government Agencies
In the digital generation, cyber espionage is more vested than ever in past history, this has left governments and their associated organizations around the globe on an uncertain foothold. Government-associated organizations worldwide have been identified as one of the easiest targets within bad actors. With various economic and political inspirations, cybercriminals have been targeting government institutions in the recent past. Let us take a look at some state-sponsored cyber-attacks on countries critical infrastructure.
1. Attack on Iran’s Transport & Urbanization Ministry
In the month of July this year, Iran’s transport and urbanization ministry suffered a disruption in its cyberspace, which affected its websites and the system was down for the whole day. Just a day before the incident occurred, the state’s whole railways system fell victim to a cyberattack, it led to posing messages about random train cancellations or delays on the indicator boards at major stations all across Iran. The electronic train status tracker of the railway was at toss throughout Iran and due to this unparalleled chaos, this cyber attack resulted in hundreds of trains being delayed or canceled.
2. The Ukrainian Navy’s Website Attacked by Threat Actors
Another massive attack in the month of July this year was reported by Reuters that was experienced by the website of the Ukrainian Naval Forces. Hackers published fake reports about the International Sea Breeze-2021 military drills on the website. This report said about lasting naval exercises from 28th June to 10th July, it also said that the Sea Breeze exercises will witness the participation of 32 countries, that will include most NATO allies, Black Sea nations, and partners. These exercises will consist of 5,000 troops, 40 aircraft, 32 ships, and 18 special operations and dive teams. In a press release, Ukraine’s Defence Ministry stated that they have also experienced several unsuccessful denial-of-service (DDoS) attacks on the Defence Ministry portal.
3. Sol Oriens Fell Victim to REvil Hacker Group
Similarly in the month of May this year, one of the hacker groups – REvil is alleged to be accountable for a cyberattack launched on a small 50-person firm called Sol Oriens. The firm SOL Oriens is known for providing consultation on nuclear weapons to the US Department of Energy’s (DOE) National Nuclear Security Administration (NNSA). Sol Oriens came to the knowledge of the attack in late May 2021. In the repercussion of this incident, Sol Oriens’ experienced a leak of documents on the dark web, and this includes the invoices for NNSA contracts and descriptions of various R&D projects.

Source : CNBC
4. Data of Japanese Government Entities Breached Through Fujitsu’s Systems
In the month of May, one more Japanese tech giant named Fujitsu’s, Its cloud-based collaboration platform known as ProjectWEB was under attack, this allowed bad actors to pick files from Japan’s multiple government agencies. The major entities that suffered from this recent vulnerability exploitation included the data of the Cabinet Secretariat, Narita Airport, and the Ministry of Land, Transport, Infrastructure, and Tourism. Stolen data also comprised of Foreign Ministry documents relating to how to realize a digital government, 76,000 transport ministry email addresses including that of the transport minister Kazuyoshi Akaba.
5. DDoS Attack on Russian Defense Ministry
This year in Mid even The Russian Defense Ministry was also hit by a distributed-denial-of-service (DDoS) attack, which is supposed to have originated from outside Russia. In this attack the website of the ministry was offline for almost an hour or so, later the professionals were able to correct the incident and bring it back live and running. It was fortunate that the attack did not cause any infrastructure or system damage. One of the mysteries associated with this is that this digital incident was supposed to happen on the day when the Russian and U.S. delegations were expected to meet and discuss digital security. Getting through the defense security is not easy but bad actors have reached there too.
6. Ransomware Attack on Ireland’s Health Service Executive
In the month of May, one incident that happened with Ireland officials was the launch of a ransomware attack and keeping the data hostage of the Health Service Executive’s (HSE). In Ireland’s publicly funded health care system, HSE was forced to shut down the entire IT system via a ransomware attack. The attack was so severe that it cut off access to patient records and resulted in delayed COVID-19 testing and cancellations of medical appointments. The Conti ransomware group demanded $20 Mn as a ransom to release the data.
7. Colonial Pipeline Victimized by A Ransomware Attack
The month of May can be counted as the Black month in the history of Cyberattacks as even the Colonial Pipeline, one of the largest oil pipelines in the US, they were also hit by a ransomware attack that forced them to shut down their systems inadvertently. A 5,500 mile-long pipeline, which carries more than 100 million gallons of fuel from Houston to New York Harbour every day, was posed to stay offline for several days due to the attack. At last, the organization had to pay a ransom of $5 million to DarkSide, a Russian-speaking hacking group responsible for the attack.
8. Personal Details of UK Special Forces Soldiers Leaked on WhatsApp
Again, in mid-year, another cybersecurity incident that occurred had an Excel file leaked from inside the Ministry of Defence which was revealed being shared around on WhatsApp groups. This file has leaked data of the British Army and a spreadsheet contained the personal information of the UK Special Forces soldiers. The file consists of details of all the 1,182 British soldiers who were recently endorsed from corporal to sergeant. It also had the details of those who belonged to sensitive units such as the Special Boat Service, the Special Reconnaissance Regiment, and the Special Air Service.
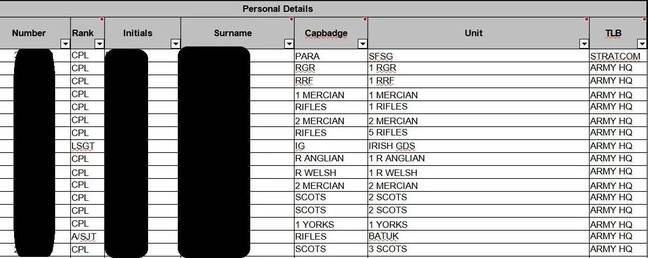
Source : The Register
Cyberattacks targeting government organizations are very disturbing and they even stop the functioning of their daily BAU. As the government agencies are self-sufficient to fight this type of cyberattack with full support from the country, the bad actors are still able to identify a bypass route to enter their system and bring it to halt. However, If we are able to develop proper cyber security awareness programs and effective cyber security tools, companies, departments, and institutions across the world can stay ahead of the threat to shield their business and reputation.