Is Blockchain a system of decentralized trust in 2023?
In 2023, blockchain is still considered a system of decentralized trust. Blockchain technology allows for the creation of secure and transparent digital ledgers that can be used to track and verify transactions without the need for a central authority or middleman. This decentralized approach to trust is one of the key features of blockchain technology and has been a driving force behind its adoption in a variety of industries, from finance and banking to healthcare and supply chain management.
Decentralization in blockchain refers to the fact that the network is not controlled by a single entity, but rather a network of nodes that work together to verify transactions and maintain the integrity of the ledger. This makes it difficult for any one party to manipulate or corrupt the system since any changes to the ledger must be approved by a consensus of the network.
Overall, the decentralized nature of blockchain technology has contributed to its growing popularity and potential for disrupting traditional business models. However, it is important to note that there are still challenges and limitations to blockchain adoption, such as scalability and regulatory issues, that will need to be addressed in order for it to reach its full potential.
Blockchain technology has the potential to revolutionize various industries and bring about significant benefits, such as increased security, transparency, and efficiency. However, there are also several challenges and limitations to blockchain adoption. Here are some of them:
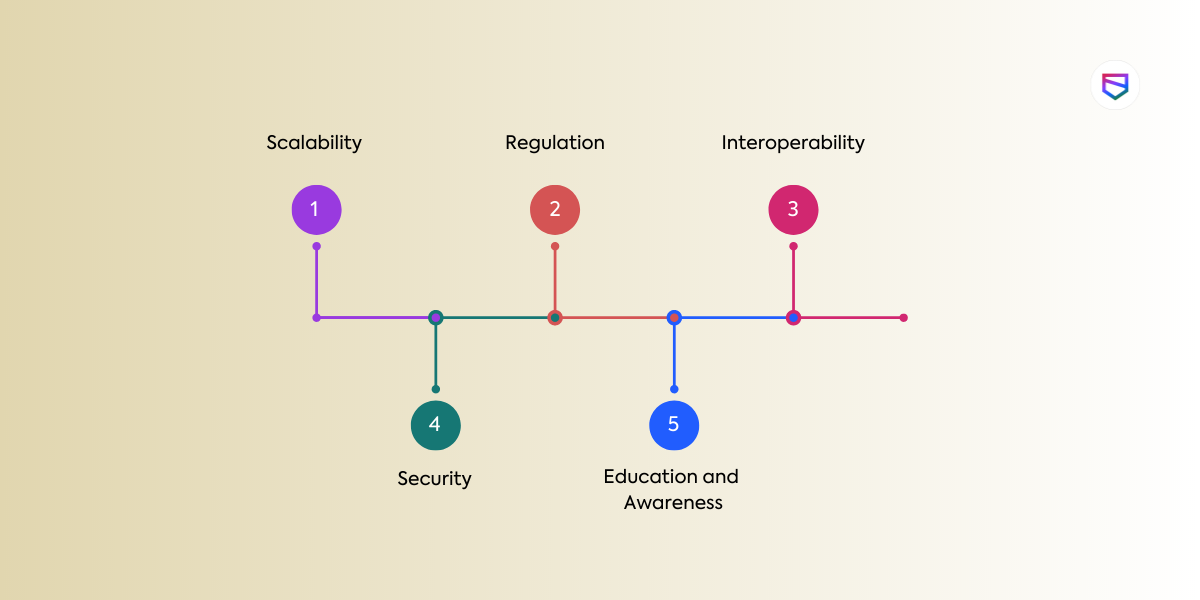
- Scalability: One of the most significant challenges facing blockchain adoption is scalability. Most blockchain systems are currently limited in their ability to process large volumes of transactions quickly. This limitation can result in slow transaction speeds and high fees, making blockchain less attractive to users and enterprises.
- Regulation: The regulatory environment surrounding blockchain is still evolving, and different countries have different approaches to blockchain regulation. Uncertainty and inconsistency in regulation can make it difficult for businesses to adopt blockchain technology.
- Interoperability: Currently, there is a lack of standardization and interoperability between different blockchain networks. This limitation can create obstacles to the adoption of blockchain technology by limiting the ability to transfer assets between different blockchain networks.
- Security: While blockchain technology is designed to be secure, there have been instances of security breaches and hacks. These incidents have raised concerns about the security of blockchain technology and its potential to be used for fraudulent activities.
- Education and awareness: Blockchain technology is still not well-understood by many people, including business leaders and policymakers. The lack of education and awareness about blockchain technology can make it challenging to adopt and implement it in various industries.
Top Blockchain Technology Statistics 2023
- With a compound annual growth rate of 56.3%, the blockchain industry will be worth $163.83 billion by 2029.
- There are over 170 million blockchain wallets worldwide (Blockchain.com users + Coinbase users)
- The global spending on blockchain solutions will reach $19 billion by 2024.
- There are over 85 million bitcoin block explorer blockchain.com wallets users worldwide as of March 2023.
- Around 336,600 Bitcoin transactions are carried out in a single day as of March 2023.
- 10% of the global population own cryptocurrencies.
- 16% of Americans have invested in cryptocurrency.
- Using blockchain, financial institutions can save up to $12 billion every year.
- Blockchain technology in the healthcare sector globally is predicted to reach $231.0 million by 2023, with a 63% growth rate over the next six years.
- Moving securities to blockchains might save $17 billion to $24 billion in global trading processing fees annually.
- From 2022 to 2030, the worldwide blockchain technology industry is predicted to grow at an 85.9 percent CAGR.
- By 2026, the worldwide blockchain market will be worth $67.4 billion.
- Banking is the sector with the highest distribution of blockchain market value.
Conclusion:
Blockchain is a revolutionary technology that enables a system of decentralized trust. It does this by creating a transparent and immutable ledger of transactions that are verified and validated by a network of nodes, rather than relying on a centralized authority or intermediary. This decentralized approach offers numerous advantages over traditional centralized systems, including greater security, transparency, and efficiency. Blockchain technology has already begun to transform industries ranging from finance to healthcare, and its potential applications are only limited by our imagination. As blockchain technology continues to evolve and mature, it has the potential to fundamentally change the way we interact with each other, conduct business, and build trust in our society.
Recommended Reading
Cyber Security Maturity Assessment for NBFCs: WeSecureApp’s Approach
Assumed Breach Assessment Case Study: Uncovering WeSecureApp’s Approach
Automation and Scalability in Red Team Assessments