7+ Major Reasons to Hire a Red Team to Harden Your App Sec
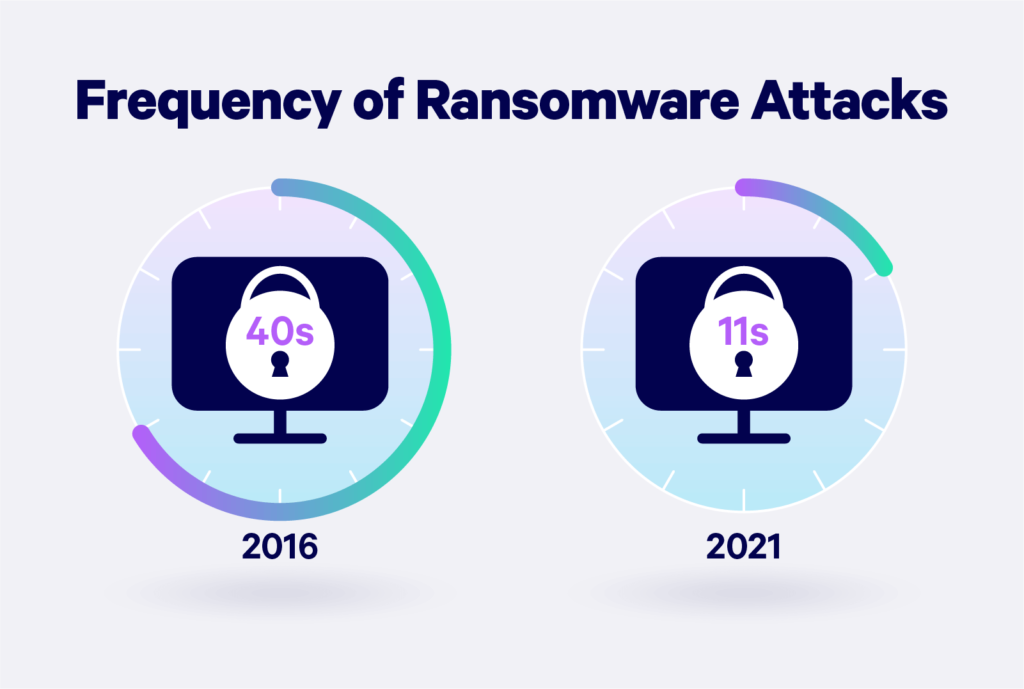
The growing cyberthreat landscape has brought a storm in the online marketplace. From the online studies and research, there were around 500 million attempted ransomware attacks that occurred in 2021. These numbers are even exceeding day by day and if businesses haven’t strategized yet then nothing can save them.
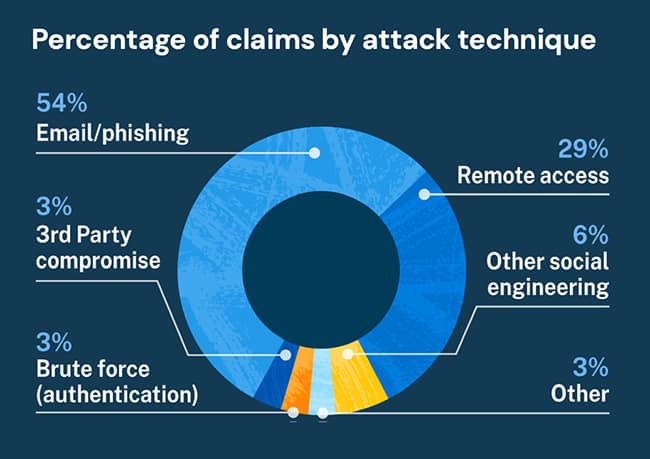
Hackers are always having their evil eyes on the websites and finances. Now, it’s become vital for businesses to have the right protocols, policies and procedures in place to keep their data secure and strengthen their infrastructure, making them resilient. With this in mind, companies have now shown their interest in hiring red teams. They identify their susceptibility to any attack by testing their systems and networks before an attacker does.
Do you have any idea about red teams? Have you ever heard about it? If, not read this blog. Here we’ll discuss the red team and the benefits of hiring them. So, let’s jump in.
What is Red Team?
A red team is a group of ethical hackers that helps the company to test its system security. This group will identify weaknesses in the company’s web applications and networks, which the same team can later remediate.
They’ll try to penetrate the systems just like the hackers do and find the loopholes. The red teaming process will help you understand your actual security posture and how well your security controls are working.
Why you should hire a red team?
There are certain reasons that will make your company hire a red team. This team will help you find the loopholes in your system and also it helps to make your system more secure. Here are some of the compelling reasons to hire a red team. Take a look.
1. Detection of Software Bugs
The ethical hackers will work on the mission to find out all existing bugs in your software security. They identify threats and vulnerabilities before cybercriminals can exploit them. The red team will reduce the cost of managing associated risks by finding these bugs.
For example, if you use particular software to manage your passwords, the hackers will exploit it. Thus, the red team will find loopholes and report them to you. It will give you a chance to fix these bugs before the hackers can take advantage of them.
2. Improved Cybersecurity
When you have a red team in your organization, it helps you improve your cybersecurity posture. The team will identify all the weaknesses in your security and help you patch them up. Thus, it becomes difficult for hackers to penetrate your systems.
An excellent example of this is Equifax’s attack in 2017. The company had failed to patch up a known vulnerability in one of its systems. As a result, hackers could steal the personal information of more than 143 million people. If Equifax had a red team, it could have identified and patched the vulnerability before the attack.
3. Risk Mitigation
According to Gartner, “The use of a red team in an ethical hacking program has the potential to reduce the probability and impact of future cyberattacks by identifying security vulnerabilities in IT systems before attackers can exploit them.”
Red teams are capable of assessing your system’s exposure level to different security threats. It helps the company to identify what needs to be fixed immediately and what can be done in a phased manner.
4. Identify Technical Improvements
Red teams help organizations understand their technical vulnerabilities and identify areas of improvement. The team uses assessment frameworks such as NIST, OWASP, etc., to assess application security.
Once the vulnerabilities are identified, the red team will work with the organization’s developers to fix them. It will help improve the overall security of the applications and make them less prone to cyberattacks.
For example, if your organization uses an outdated version of the software, the red team will identify it and suggest you update it. It’ll help in fixing the known vulnerabilities present in that software.
5. Assessment of Third-Party Vendors
Organizations nowadays rely on third-party vendors to run their business operations. This, however, makes them more vulnerable to cyberattacks. A hacker can easily penetrate the third-party vendor’s systems and steal the data.
Red teams help organizations in assessing the security posture of their third-party vendors. They look for vulnerabilities in the vendor’s system and check if any malware is present. It’ll help you to take necessary measures to secure your systems before a significant security breach occurs.
For example, if your organization uses a cloud-based storage solution, the red team will test it for vulnerabilities. If they find any, they’ll report it to you and suggest you take appropriate action.
6. Testing of Emergency Response Plans
It becomes difficult for organizations to test their emergency response plans, as it may hamper their day-to-day operations. However, Red teams can help you test these plans without interrupting your everyday operations.
The team will first identify the vulnerabilities which need to be tested and then test them. They’ll provide a report on whether your plan is strong enough or not. If it’s not, they’ll suggest ways of strengthening it.
For example, let’s say your organization plans to deal with a ransomware attack. The red team will test it by infecting one of its systems with ransomware. They’ll then check if the organization could effectively contain the infection and recover the data.
7. Helps in Building a Cybersecurity Culture
An organization needs to have a cybersecurity culture to be secure against cyberattacks. Red teams can help build this culture by training the employees to identify and respond to security threats.
The team will first identify the weaknesses in your security and help you patch them up. They’ll then train your employees on identifying different types of security threats before they are executed. It’ll help them secure their systems and minimize the impact of cyberattacks.
For example, suppose your organization is storing its data in the cloud. In that case, the red team will first check how securely it’s stored and then train your employees to identify and report suspicious activity.
8. Testing the Effectiveness of Disaster Recovery Plan
It becomes difficult for organizations to test their disaster recovery plans, especially when taking down an entire system. Red teams can help in trying these plans without disrupting their everyday activities.
The team will first identify what needs to be tested and then do it without interrupting your regular operations. They’ll then provide a report on the effectiveness of your plan and whether it can live up to your expectations or not.
For example- Let’s say your organization has a disaster recovery plan that involves restoring one of its systems from backup. The red team first tests if that system is recoverable, following which they send simulated alerts to the organization. They then check if the organization could respond to the warnings and recover the system successfully.
Conclusion
Red teams are a vital part of any organization’s cybersecurity strategy. They help identify the vulnerabilities in your system and suggest ways of fixing them. They also help in building a cybersecurity culture within your organization. So, if you’re not using a red team yet, it’s time to consider doing so – Talk to Our Delivery Head








