- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
Choose the Right VAPT Services Provider
With the ever-evolving world of technology, businesses are prone to cyber-attacks, which can cause a huge financial loss. As stated in Forbes report, “Every minute, $2,900,000 is lost to cybercrime”. The reason being nearly 80% of senior IT employees and security leaders strongly believe that the majority of companies today lack sufficient protection against cyber-attacks and that is what has happened all around.
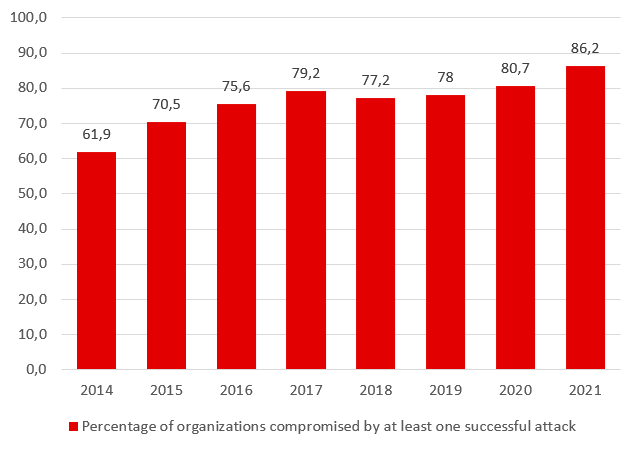
Cybercrimes are increasing every day globally where every 8 out of 10 companies have fallen into the trap of cyber fraudsters. The graph below indicates the status of the cybercrime world.
 Do you know?
Do you know?
“2020 had been a record-breaking year for data lost due to breaches plus the sheer number of cyber-attacks. Now 2021 has already been its successful predecessor with the increasing number of cybercrimes.”
So, what’s the solution? Now, it’s time to hire a (Vulnerability Assessment & Penetration Testing )VAPT Services Provider and get rid of all the cyber attacks. Any idea, what a VAPT services provider can do for your business? If not, then check out the rest of the blog.
Here, we will discuss some of the most important features and benefits of VAPT service providers so that you can make an informed decision about which one is right for your needs.
Now, let’s get started.
What is VAPT?
VAPT stands for a Vulnerability Assessment and Penetration Testing. VAPT uses computerized tools to assess an organization’s IT environment’s security state and compliance posture to find ways that attackers can exploit potential vulnerabilities (and thus mitigate). Many different types of vulnerabilities can be discovered and analyzed through VAPT, including web application security issues, server misconfiguration, operating system (OS) weaknesses, and specific business applications.
Benefits of hiring a VAPT service provider.
- Potential for Cost Savings.
By reducing unplanned downtime caused by security incidents with VAPT services, an organization can save money on IT support costs.
- Better Security for IT Staff.
With VAPT services, IT staff can focus on more strategic issues. It takes care of the day-to-day tasks to ensure that IT staff can work on more challenging projects.
- Meeting Compliance Requirements.
VAPT can help an organization meet industry regulations such as HIPAA or PCI DSS standards for payment card data protection by identifying and remediating security vulnerabilities in a manner that is consistent with these regulatory mandates.
- Improved Security Posture
VAPT services can help an organization improve its overall security by reducing the attack surface, identifying critical operational issues and vulnerabilities in real-time, focusing resources on priority projects that provide maximum benefit to the business while mitigating risk exposure.
- Security & Compliance Assessment.
It helps an organization get ahead of the many security challenges it faces by assessing vulnerabilities, reducing business risk exposure through improved efficiencies in IT operations. It includes server configuration validation and meeting industry regulatory requirements such as HIPAA or PCI DSS standards for payment card data protection.
How does WeSecureApp as a VAPT Service Provider Work? What’s their methodology?
WeSecureApp typically follows a methodology that is broken down into five areas which are listed below:
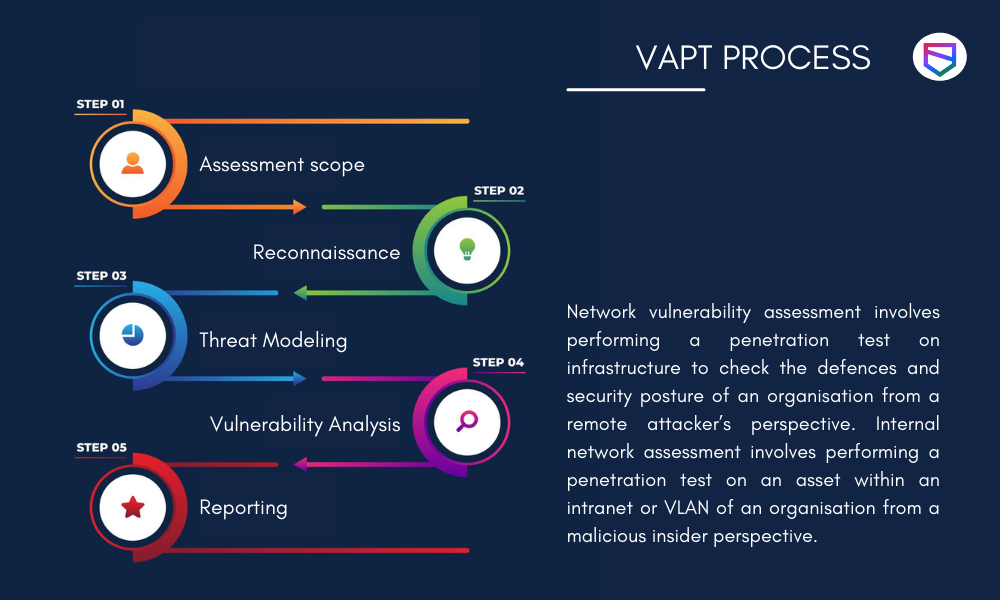
- Reconnaissance
This is the first phase of VAPT, in which an attacker uses tools to identify live hosts on a network.
The goal during this stage is to map out what devices are running and discover all active IP addresses that can be reached from outside the organization’s perimeter. It also includes mapping internal networks, finding sensitive data being transmitted over public networks, and finding servers that have vulnerabilities that can be exploited.
- Build Test Cases
The second phase of VAPT is where the actual security testing takes place. Test cases are created that highlight is known vulnerabilities and how they can be exploited by attackers to gain unauthorized access into an organization’s IT environment.
Here, the goal is to find gaps in existing defenses or poorly configured systems so that they can be remediated before an actual security incident takes place.
- Deploy Scanners
The third phase of VAPT is where scanners are used to run the test cases and identify vulnerabilities. It allows for a more thorough analysis than simply identifying vulnerabilities through manual testing or other means.
Once all identified weaknesses have been confirmed, an organization’s security team can prioritize which issues need to be addressed first based on their impact level in mitigating the organization’s overall risk exposure.
- Manual Penetration Testing
The fourth phase of VAPT is where penetration testing occurs, which includes manual exploitation activities that are used to validate the identified vulnerabilities are real and can be exploited by attackers. This stage also further validates how an attacker could use these weaknesses to access critical systems and data.
As part of this phase, additional test cases are created so that security teams can continue to prioritize the issues identified in earlier stages based on their impact level within an organization’s overall risk exposure.
- Report Generation
The final stage of VAPT is where a report containing all findings from previous steps is generated for distribution to senior management. It includes a summary of findings and recommendations that will help the organization prioritize addressing identified vulnerabilities.
Final Thoughts
As you can see, there are many benefits to choosing VAPT services. It is worth it for businesses of any size to take the time and evaluate all their options carefully before making a decision about this important purchase. If you have questions or need help please contact us today. We look forward to hearing from you soon.
About WeSecureApp
WeSecureApp is a leading provider of VAPT services, helping organizations identify their security posture to make informed decisions about their technology deployments. Contact us today for more information on our VAPT services or to schedule your free security assessment – Talk to Our Delivery Head