- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
Health Insurance Portability and Accountability Act
Non-compliance with HIPAA exposes your healthcare organization to a nightmarish scenario. Millions in fines, reputational ruin, and worst of all, compromised patient privacy. WeSecureApp helps you steer clear of this data disaster.
Fill out the form below to speak with a WeSecureApp compliance specialist
What is HIPAA?
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law that requires the creation of national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge. The US Department of Health and Human Services (HHS) issued the HIPAA Privacy Rule and HIPAA Security Rule to implement the requirements of HIPAA. The HIPAA Security Rule protects a subset of information covered by the Privacy Rule. As a result of the Health Information Technology for Economic and Clinical Health (HITECH) Act of 2009, both covered entities and business associates are now accountable to the HHS and individuals for appropriately safeguarding private patient information. Organizations must implement reasonable and appropriate controls and management policies and procedures to comply with all HIPAA administrative, physical, and technical safeguards.

HIPAA Rules
HIPAA Privacy Policy
See how your systems react to a simulated attack, revealing security gaps like outdataHealthcare data is personal to every patient. Everyone has the right to keep their personal health records private, and every covered entity should be responsible for ensuring that no unauthorized person gets access to the patient files.
ed software or unpatched vulnerabilities.
HIPAA Security Rules
HIPAA Security Rule ensures patient data privacy by requiring covered entities to secure electronic health information (ePHI) at rest and in transit. It mandates safeguards for confidentiality, integrity, and availability of ePHI through appropriate security measures.
HIPAA Breach Notification Rule
This rule requires covered entities to inform affected individuals in case of a breach of unsecured patient information. It refers to an impermissible use or disclosure that compromises the security or privacy of the patient’s data.
Patient Safety Rule
This rule aims at protecting identifiable protected health information that can be used to analyze and improve the safety of the patient.
Enforcement Rule
Sets penalties for breaking the HIPAA privacy and security rules and describes the procedures for investigations and public hearings related to data breaches that expose PHI.
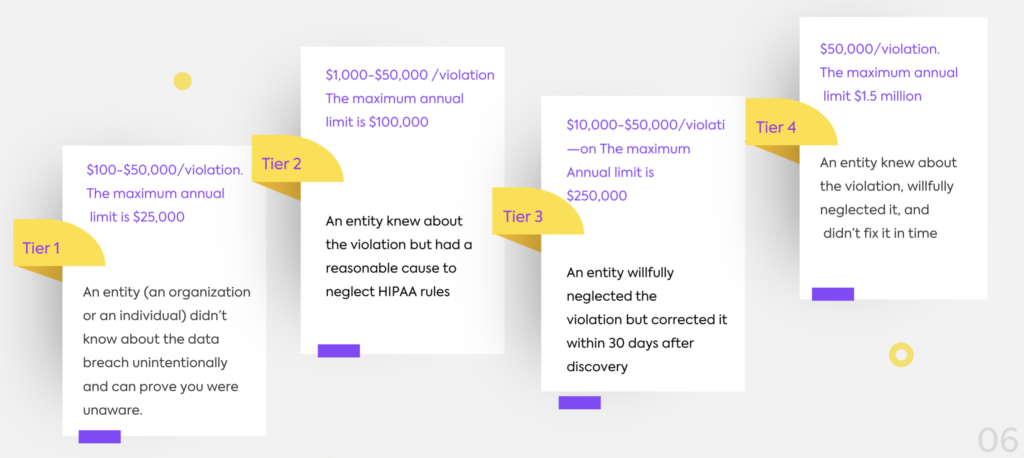
Enforcement and Penalties for NonCompliance
The Department of Health and Human Services (HHS),
How WeSecureApp Can Help?
HIPAA Assessment and Consulting
Our HIPAA compliance consulting and assessment service comprises system assessment, advisory services, and onsite assessment that fortify your HIPAA compliance program as well as protect your organization from any violation.
HIPAA Security and Privacy Services
With our effective HIPAA compliance solutions, we help healthcare organizations to take all corrective actions to protect their data. Our experts assist in privacy protection and help enhance data security. WeSecureApp offers training, advisory services, cloud security assessment, risk analysis, and ensure that your systems are strong against any data breach.
WeSecureApp HIPAA Implementation Methodology
Stage 1
Pre-Readiness Assessment and Documentation
- Conduct a readiness assessment to find out what tasks are to be performed.
- Identify the e-PHI involved and data flow through data flow diagram.
- Create an internal Data Protection Policy and other top-level policies as needed for e-PHI. Create awareness among employees about key HIPAA requirements.
- If required, would help the organization appoint a Data Protection officer and understand the organization chart.
stage 2
Conduct Risk Analysis and Management.
Conduct risk management activity to check all the risks pertaining to e-PHI data.
stage 3
Process Design and Control implementation
- In this phase, the team will help in creating or identifying a process that offers complete data protection and helps in detecting data breaches at every point of the application cycle.
- Analyze what data is being transferred outside of the company, and when.
- Implement the necessary organizational and technical controls to protect the e-PHI of data subjects.
stage 4
Internal Audit (Mock OCR Audit)
- Perform post-compliance audits internal to an organization to ensure it is fully compliant.
- Any findings are presented to the management and final solutions are provided that are meant to fill the gap.
Deliverables

Avoid Million Dollar Fines. Get Expert Help with HIPAA Compliance.
Frequently Asked Questions
HIPAA applies to “covered entities” like healthcare providers, health plans, and healthcare clearinghouses. It also extends to “business associates” who handle PHI on behalf of covered entities.
While HIPAA doesn’t mandate specific encryption algorithms, it does require covered entities to implement “addressable” safeguards to protect electronic PHI. This often includes encryption at rest and in transit.
Yes. HIPAA introduces the concept of Business Associates (BAs). You must have a signed Business Associate Agreement (BAA) with any vendor who accesses PHI on your behalf. This agreement outlines their obligations to protect patient data.
We offer a range of services, including risk assessments, security awareness training, and implementation of HIPAA-compliant security controls. We can also assist with developing and maintaining HIPAA policies and procedures.
HIPAA safeguards any data that links a patient to their medical condition. This includes names, addresses, Social Security numbers, diagnoses, and treatment details.




