- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
How Do Hackers Create a DDoS for a Website?
Hackers are none other than professional criminals. They can be called as a person who has unauthorized access to any secured system or network and damages it with the motive of earning money. They have started using DDoS attacks to access websites by making it very difficult for legitimate users to use the website. More than just gaining unauthorized entry into a system, these attacks are now being used as a type of extortion where the hackers threaten to shut down the websites unless they are paid off.
In 2021, there were around 857 million DDoS attacks that Akamai recorded, and this is almost 50% of the total attacks made each year. And without a doubt, these numbers are likely to increase in the future with more and more hackers stepping into this field.
While we mostly hear about crypto-jacking and ransomware attacks nowadays, there was a time when DDoS was a prevalent method. The hackers still use it to take down a website for a couple of hours, and they would have made a lot of money from the ransom they demand.
Now that you know what a DDoS attack is let us find out how these criminals carry out this attack and how they create DDoS for a website.
What is DDoS?
“Around 28,700 DDoS attacks occur every day”.
DDoS is a form of attack that involves the attacker sending multiple requests to the server which is sought to be attacked. If these requests overload the servers, it can bring down its network and disrupt legitimate users.
These days, hackers do not even need an army of computers or any powerful tool to carry out such attacks, and instead, they use the available bots or devices to send out these requests. And lately, even IoT has come into play as there are a lot of smart gadgets that attackers can exploit by sending out DDoS requests.
How is DDoS created?
The process of creating DDoS is not so complex. All the hacker needs to do is find out the vulnerabilities in the system they are targeting and then exploit them by either increasing traffic or using a botnet.
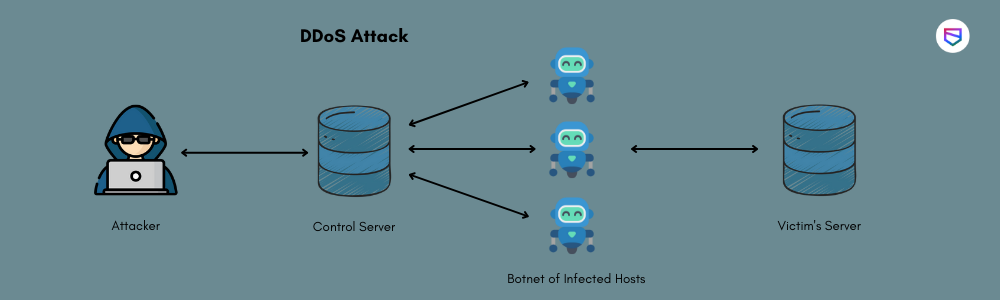
Here are some of how hackers create DDoS for a website:
Using Spambots
Hackers can use many simple bots that they find over the internet to do their bidding. The bots are nothing but programs that can be easily found on the web with minimum programming knowledge. They send out requests to the targeted site, and once their number is increased, it will cause an overload in traffic by slowing down or crashing the website.
Using IoT
Identity theft is also used by many hackers to create a botnet and use it in an attack. Through this, they can access other devices like Smart TVs, CCTV cameras, and even computers to add to their botnet. They can then easily take down any site by just controlling all of these devices simultaneously.
Using DNS Amplification Attack
It is one of the most popular ways to create DDoS for a website. Hackers use this method by finding out which DNS server their target uses and then spoofing their IP address. They can also send requests with high packet sizes (above 65,535 bytes) with this attack, making it seem like the attack is coming from a single computer even though there may be thousands of them.
How do DDoS make the website vulnerable?
There are many reasons why a website becomes vulnerable to DDoS attacks. Here are the important ones:
Small Business Website
If a website has a minimal number of visitors, then hackers will find it easier to send out requests and disrupt its services. Such websites usually lack DDoS protection due to which they become an easy target.
Vulnerable Code
It usually happens due to the lack of security in coding. Developers leave some loopholes through which hackers can enter the website and take it down by simply exploiting these vulnerabilities. Some of the most common issues that are faced are SQL injection, cross-site scripting, remote code execution, etc. These weaknesses allow the hackers to gain access to the website and even install malware, which creates a botnet for them.
Weak Servers
Sometimes even if the website has a good number of visitors, but its servers cannot handle such traffic. It is usually because of underpowered servers that hackers can cause disruption in services and ultimately take down a website.
Unpatched Systems
Another way through which DDoS for a website is made possible is by exploiting vulnerabilities in the system. Sometimes, even if a developer has given enough thought to DDoS protection, there can still be some errors that may go unnoticed, and it can create a security loophole.
If a site uses outdated software, it becomes an easy target for hackers to find pathways to compromise its infrastructure.
Unprotected Content Delivery Network (CDN)
In some cases, hackers may also take down a website by controlling its CDN without even entering the servers. If there are enough loopholes in the CDN, it will render all of the protection efforts useless.
Using too Many Security Appliances
Having too many security appliances can make a website a perfect target for hackers. There can be some compatibility issues between them, making it hard to identify the real threat and take it down.
Using Expired SSL Certificates
If an SSL certificate expires, its security level goes down automatically, allowing the hackers to easily access the site without any permission and take it down. It is one of the most common mistakes developers make while developing websites, especially when SSL certification is too expensive to renew or ignore.
Using Compromised Machines
If the website uses any third-party services like cloud servers, hackers can compromise these servers and take down the website. It is because cloud servers are usually leased out to different users, and vulnerability in one of them can affect all the sites hosted there.
How to mitigate DDoS attacks?
As we now know how hackers create DDoS and make your website vulnerable, let us find out how one can stop such an attack. There are several ways to protect your site using which you can defeat a DDoS attack. Some of them are:
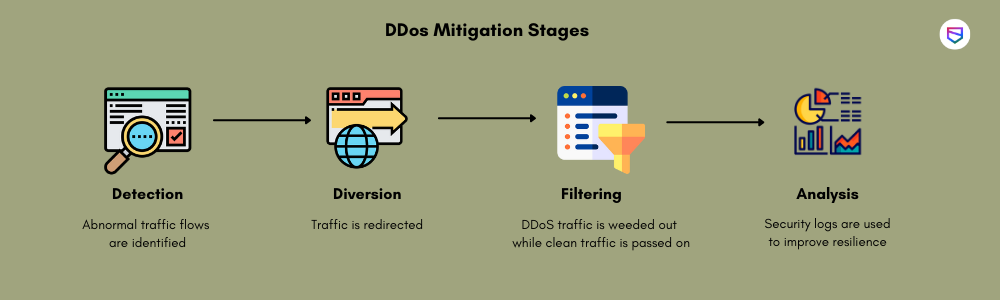
Using CDN for Traffic Management
If the attacker is sending requests from fake IP addresses, you can use a Cloud-based infrastructure to identify and block such requests. In simple terms, if anyone tries to send a request from an unknown or suspicious IP address, the request will not go through. Instead, the CDN will send it to a server where you have control. Then you can analyze all requests, and if they are legitimate, you can allow them in your network by changing the firewall settings.
Using Protective Filters for Traffic Management
You can also use traffic filtering, which creates a cycle of validating IP addresses before sending any request in your network. This way, the requests will only come from known servers, and there can be no traffic coming from bots or other sources that are not authorized to send requests.
Using DDoS Mitigation Device
There are devices available in the market that can be used to analyze traffic coming into your site to identify any DDoS attack. They help create DDoS for a website as they can identify bots and suspicious traffic.
Using the Third-party Security Service Provider
You can also use services that protect certain kinds of attacks like DDoS, phishing, etc. Such services will analyze your network and help you with identifying locations where the attackers are hiding. And then, they will help you remove them from your network and protect it against such attacks in the future.
Conclusion
All in all, developing a website is not an easy task. As you have seen here, numerous mistakes can be made while creating one for your business or organization, and all of them can put the site at risk and render it useless to serve any purpose.
Therefore, playing safe is critical to building a solid relationship with your customers and the business. If you do not want to go through such embarrassment, follow these guidelines and create a secure website for your organization or company. WeSecureApp understands all the challenges and provide the right security strategy to tackle them.
Know more about WeSecureApp – Get Quote Now








