How to Teach Developers Create Secure Apps?
Developers pay great attention to the design of software products, trying to make them as convenient as possible. But what about the security of the data that users entrust to the manufacturers of these applications? How can one learn and teach to create secure applications? I would like to share my experience in tutoring developers and propose a system that allows you to train in finding and fixing vulnerabilities.
The Importance of Secure Development
If an ignorant developer writes a code, such a developer will bump into bugs and vulnerabilities sooner or later. And then an evil security man comes in and asks to eliminate those vulnerabilities.
The main idea of learning secure development is that someone will find a vulnerability anyway, and the code will eventually have to be rewritten. To avoid this, developers need to be taught how to write good code right away.
Meet John
John is a new employee. Now he is good at tree rotation, but so far, he does not understand the difference between CSRF and XSS and does not know anything about other vulnerabilities. How can you help John better understand information security?
I would like to offer a model with five levels of information assimilation. Here they are – understanding, recognition, reproduction, usage, and creation. Let us walk John through all these steps. At the end of the journey, he will learn how to build secure applications independently.
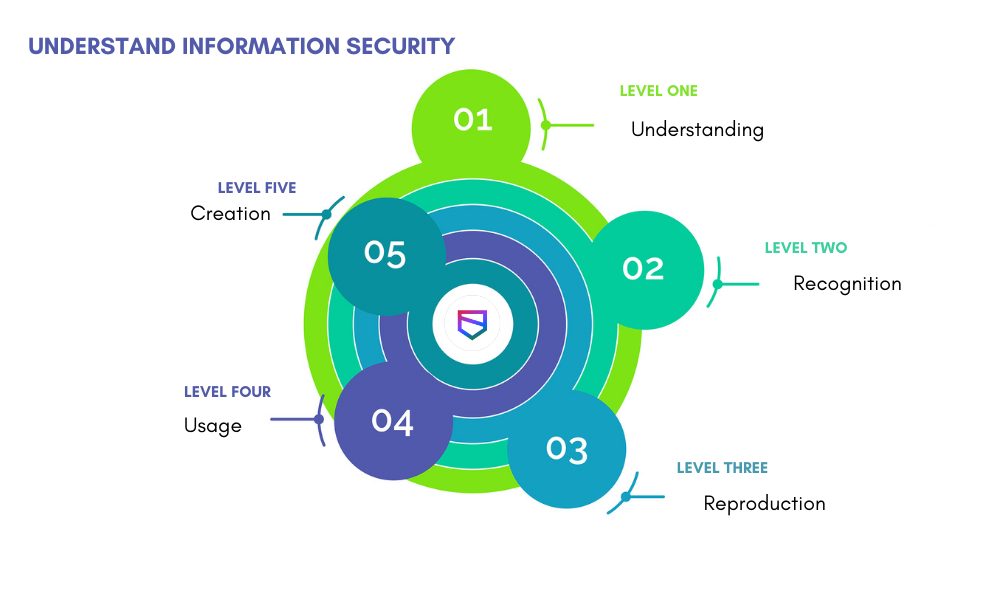
Level 1. Understanding
At this stage, John does not yet have any security skills and knowledge, but he is already figuring out that he needs them. At the same time, he receives a welcome letter from the information security department, which informs that from now on, he will live in the safe world of WeSecureApp. (your company name.) John is invited to take a series of courses on secure application development; special assignments are created for this activity. If something has not been passed, reminders will come every week.
Level 2. Recognition
At this stage, John begins to gain theoretical knowledge about what security is, who these guys from the information security service are, and what they do. Here, paper posters may help. They remind employees that security exists (even if they do not see it, it still exists). Besides, these posters are a kind of PR for the in-house information security department.
Many employees are working remotely now and rarely visit the office. So, posters at coffee points are no longer as effective as they used to be. Today, it is better to inform colleagues using the internal information security blog published about interesting vulnerabilities, cyber threats that may affect your products, and other valuable materials.
Let us go and chat
It is helpful to conduct training where you create a lively discussion between developers and security professionals. These training sessions should not focus on abstract vulnerabilities but review those information security issues that are of direct concern to your teams.
Working together, you can figure out why certain problems arise, how attackers can exploit a specific vulnerability, and what damage this can cause to a company. And of course, at these meetings, IT security professionals help the teams to eliminate these problems.
Training is a valuable tool, but unfortunately, not scalable. Most likely, your security team consists of 2 – 3 – 5 people, while there are a lot of services and development teams in the company.
Besides, new developers get hired all the time. To cover everyone, it is desirable to create manuals and guidelines on developing secure applications for all the parties involved, including testers, system administrators, managers, and other specialists. Text articles supplemented by slides and videos work the best.
Your developers do not have to reinvent the wheel. They can reuse ready-made and verified solutions. Guidelines should not always be built on vulnerabilities but focus on best development practices instead. It is good to have security guidelines for the web, Android, iOS, compiled applications, and smart devices.
Go beyond
Do not be limited to posters, an information security blog, training, and guides. Consider the secure application development practical exercises John needs to do.
Some companies create a general course for a developer that will suit everyone. In practice, it is better to create several individual courses: for Android developers, for iOS app developers, for those who develop applications using Python, C++ (or other languages you use.) It is good to have a separate course for the cloud and web developers based on OWASP Top 10 and those vulnerabilities that you most often come across in products.
Again, to visualize materials, it would be good to invite artists who draw pictures, comics, cartoons, and videos.
Level 3. Reproduction
At this level, John can apply theoretical knowledge and address typical security issues. Special solutions are available that enable employees to find and fix vulnerabilities. There are many such systems on the market, including open-source tools.
If you decide to develop your own system, your solution needs to satisfy the following requirements:
- Training in finding and fixing vulnerabilities.
- Automatic solution/answer checker.
- Adding custom tasks.
How to create assignments that are relevant to the technologies used in the company?
There are several stages here. Let us take a look at them.
- Prepare a code with vulnerabilities. A common buggy code is to be found first. Ideas for assignments are not invented on purpose; just take the tickets created, the items being audited. Out of that, take patterns that may be of interest to most employees, and codes with vulnerabilities are to be developed on their basis.
- Create functional tests.
- Create security tests. It is necessary to check if the vulnerability is really fixed correctly. There is an interesting nuance here. For most vulnerabilities, it is not difficult to write such tests, especially if you want to allow the developer to fix the error in unusual ways.
- Validate acceptable solutions. At this stage, it is better to complete the test tasks yourself and validate the performance of the test.
- Prepare a Docker image in which to run tests.
- Write the theoretical part and description of the task.
It is good to have a module that shows the progress in completing the test tasks. Based on this data, the best employees can be rewarded with virtual medals. When John solves all the tasks correctly, he will receive an award so that all colleagues know what a great guy he is.
Level 4. Usage
Having trained in such a system, John can take part in a CTF.
Level 5. Creation
At this stage, John moves to creation as he will use the acquired skills and knowledge to write reliable code and develop secure services.
What tools and approaches do you use to write a safe code and test your applications? Please share your opinion in the comments.
Build Secure Applications – Talk to Our Delivery Head

About Author
David Balaban is a computer security researcher with over 17 years of experience in malware analysis and antivirus software evaluation. David runs MacSecurity.net and Privacy-PC.com projects that present expert opinions on contemporary information security matters, including social engineering, malware, penetration testing, threat intelligence, online privacy, and white hat hacking. David has a strong malware troubleshooting background, with a recent focus on ransomware countermeasures.