How Watering Hole Attacks Put Your Online Security at Risk
In the dynamic realm of cybersecurity, threats continually evolve to exploit vulnerabilities and bypass traditional defense mechanisms. One such insidious threat is the “watering hole” attack. This article explores what watering hole attacks are, how they work, and their impacts provides real-world examples, discusses mitigation strategies, and highlights the importance of proactive cybersecurity measures.
Understanding Watering Hole Attacks
In the ever-changing landscape of cybersecurity, threats to our online safety continue to evolve. One such stealthy danger is the “watering hole” attack. This form of cyber threat gets its name from the animal kingdom, where predators often lie in wait at watering holes to ambush their prey. In the digital world, malicious actors use a similar strategy, targeting websites or online resources frequented by specific individuals or organizations.
How Does Watering Hole Attacks Work?
When unsuspecting users visit these compromised websites, their devices become infected with malware. This malware can range from spyware and keyloggers to advanced forms of malicious code. Its purpose is to gather sensitive information, provide unauthorized access, or compromise the victim’s system in some way.
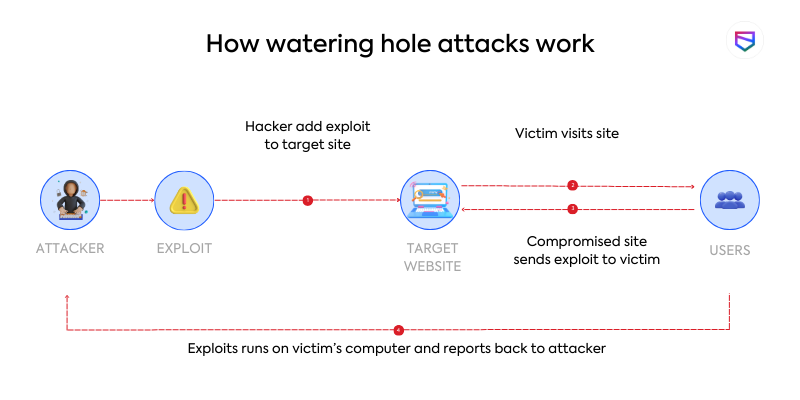
source: Tech Target
The Impact of Watering Hole Attacks
The impact of this attack can be severe. Victims may unknowingly download malware, leading to data breaches, financial losses, and reputational damage. Critical infrastructure, such as power grids and government agencies, can be vulnerable, potentially resulting in widespread disruptions. Moreover, these attacks often go undetected for extended periods, allowing attackers to harvest sensitive information stealthily.
Real-World Examples
- Department of Labor Attack (2013): In 2013, attackers compromised the U.S. Department of Labor’s website, injecting malicious code into a frequently visited page. This led to data theft, affecting employees and contractors.
- Operation Ephemeral Hydra (2014): Operation Ephemeral Hydra was a watering hole attack campaign targeting websites related to international affairs and foreign policy. Visitors to these sites, including government officials and journalists, were exposed to malware.
- Ukraine Power Grid Attacks (2015 and 2016): Watering hole attacks on energy sector websites in Ukraine caused a series of power outages, illustrating the potential impact on critical infrastructure.
- Hong Kong Democracy Activists (2019): During the 2019 Hong Kong pro-democracy protests, online platforms frequented by activists were targeted. Malicious code on these websites put the security of activists at risk.
Preventing Watering Hole Attacks Requires a Multi-faceted Approach:
- Regular Software Updates: Keeping software and plugins up-to-date helps close known vulnerabilities.
- Intrusion Detection Systems: Employing intrusion detection systems can help spot unusual network activities.
- User Education: Teach employees and users about the risks and signs of these attacks to enhance their vigilance.
- Access Controls: Implement robust access controls to limit the potential impact of a successful breach.
- Traffic Monitoring: Regularly monitor website traffic patterns for any suspicious activities that may indicate an ongoing attack.
Conclusion
Watering hole attacks underscore the ever-evolving nature of cybersecurity threats. Cybercriminals continually refine their tactics, making it crucial for individuals and organizations to stay proactive in defending their digital assets. By understanding how these attacks work, recognizing their impact, and implementing robust mitigation strategies, we can fortify our cybersecurity posture in an increasingly perilous digital world. Remember, vigilance and knowledge are our strongest allies in the fight against these stealthy cyber threats.
Recommended Reading
Understanding Advanced Persistent Threats
Security and Safety of Decentralized Finance (DeFi) Platforms
HTTP Parameter Pollution and Mass Assignment Attacks