- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
Security Deep Dive into OTT Platforms

For the past few years globally, all industries have been pushing for going digital, but not all have embraced it the way we were expecting, but one industry that pushed it more than the others is the entertainment and telecommunication industry. They embraced going digital and came with a new application/platform services for their consumer base and this is OTT.
OTT (Over-the-top) is an application or service that is provided via the internet that bypasses the traditional distribution form. OTT is generally used for referencing video-on-demand platforms (Netflix, Amazon, Hotstar, Disney+, ALTBalaji etc.) but also can refer to audio streaming (Spotify, Apple Music), messaging services (WhatsApp, Telegram) or internet-based voice calling solutions (Zoom, Skype).
With high-speed internet, it’s become easier for the larger population to connect and aggregate content at the comfort of their homes. It’s estimated that OTT platforms can reach up to US$ 64.5 billion in revenue by 2021 and with over 100 million user base, but what about the security for the OTT platforms?
Security challenges:
With revenue streams going up and the consumer base increasing on a daily basis more and more content owner companies are pushing towards OTT platforms and to keep up with current hunger they are coming up with newer technologies and new content on a daily basis. When there is a surge in the industry like this there always will come security challenges and some of these challenges are:
- Piracy — many thought the content pirating is a thing of the past but it is rearing its head again and is more powerful and advanced by finding newer ways like screen and audio recording and distributing the content illegally. Despite the efforts made by the industry to standardize digital content and improve security, device fragmentation poses a significant challenge in tackling piracy.
- DDOS the servers — in this kind of attack an attacker would use multiple systems to flood the bandwidth or resources of the servers belonging to the app/platform and essentially overloading it so that the servers are brought down, this disrupts their service offering for the users and can cause huge financial repercussions.
- Reverse engineering — a hacker would often disassemble the app/platform code, analyze it, insert some kind of malware/change it and compile the infected app as a pseudo entity and can access free content without spending a penny. They, in turn, could release the modified app to the larger public compromising them and gaining sensitive information.
- VPN access to gain content — some of the platforms often offer different content based on user geolocation one way the users tackle this is by using VPN to mask their geolocation thus allowing them to access more content for free.
- PII data proliferation — since these service providers usually tend to collect a lot of personal information from the users, they are more liable to security breaches through attacks like SQL injections and DNS attacks.
Solutions:
There are many passive or active ways to protect content and innumerable tools that can be used as well. Here we will talk about a few of those solutions:
- Tokens: This mechanism can be used to validate the consistency and integrity of the incoming requests. How it would work is the application server would be validating the token that is received with the incoming client request to ensure it’s the original request, i.e preventing URL sharing, tampering and other changes.
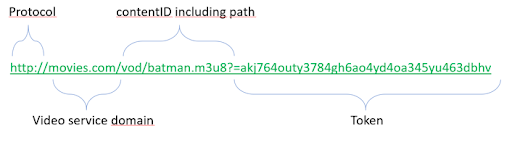
- Entitlement: This could be a scenario where multiple clients share the same public IP that is behind a NAT gateway. Like in a company or university network. The usual way to control this is by enforcing them to log in through a web portal, thus allowing them to control the number of sessions signed in parallel, which devices are used and more.
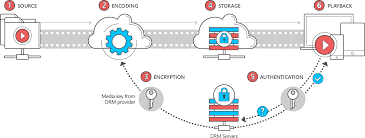
- DRM- Digital Rights Management:
- is the current licensing system that is being used to allow the content owner to control how and by whom the content is being consumed.
- is not ENCRYPTION but is a complete system for managing content access.it includes distribution of encryption and decryption keys, licensing servers and others like policy control and offline playback control. There are many commercial DRM available in the market (Apple Fairplay, Adobe Primetime DRM, Google Widevine etc.) content owners can choose to use multiple DRM’s based on their needs and can even have custom solutions. Things to keep in mind while choosing one is:
- Provide users with a transparent experience over managed or OTT networks.
- Independent of platforms or devices and be able to deliver anywhere.
- If a security breach was to occur, your DRM provider should be able to react quickly to locate the source of the problem and use any means to fix it.
-
Watermarking: is a content security technique to ensure that there is security when content is played on screen. Content owners can insert invisible user-specific information from real-time to video content, allowing them to track the distributor from illegally distributed content.
Conclusion:
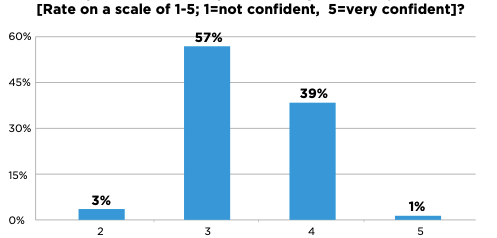
As there is an increase in cyber-attacks more and more media organizations need to take security measures to protect their entire online business, not just video streaming. We have talked about a few of the solutions above but there are many more ways your security can be breached. In a recent survey conducted by Akamai, it was seen that only 1% of organizations are confident about their security posture.
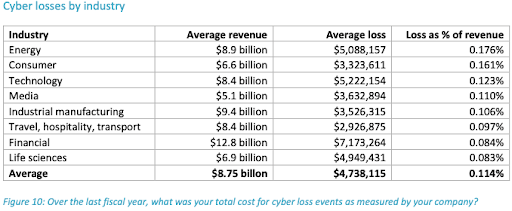
What most companies underestimate is the amount of money that goes in tackling security threats and these numbers are rising exponentially. How do you curb this? How do you protect yourself? As a company, you have to take a holistic approach to security. We at WeSecureApp can provide you with managed solutions for all your security needs. With our flagship offering like Managed Security Solutions, we would help you in understanding your security posture, review your application development cycle by applying an innovative approach and custom test cases that are relevant to your services.
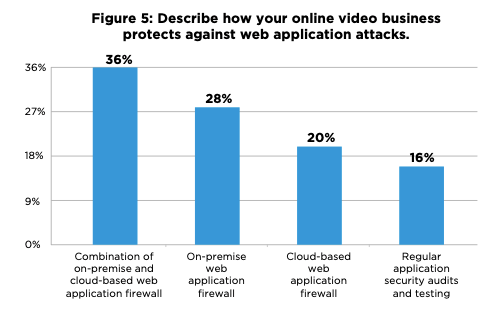
We also offer managed DevSecOps services where we help you in integrating security into your current development lifecycle. With this, you can push newer services and technologies a lot quicker, more safely and most importantly with lesser bugs. This service can be seamlessly added to your existing environment and with the added benefit of developers being trained in security practices.








