Impact of the Russian-Ukraine Conflict on Cybersecurity
24th February 2022 will be remembered as a watershed moment in Russia and Ukraine. On that day, following a series of escalations in the Donbas region of eastern Ukraine, Russian troops began a full-scale invasion of their neighbor. The Ukrainian army was quickly overwhelmed, and within two weeks, the Russians had taken control of Crimea and were rapidly advancing westwards.
Unfortunately, the invasion didn’t stop with the land. Russian hackers took control of Ukraine’s electrical grid, water supply, and military command and control systems in a coordinated cyberattack. The aim was to cripple Ukraine’s infrastructure and bring the country to its knees.
The impact of this invasion is far-reaching. For cybersecurity professionals around the world, it has served as a stark reminder that cyber warfare poses just as significant a threat to our societies and way of life as conventional warfare. And while there are no easy solutions, we must continue to work together to protect ourselves from these threats.
So, getting back again to the cyber front of Ukraine. Let’s see what happened exactly in the country’s cyberspace, what could be the consequences of this, and how other states should react to it.
Ransomware groups involved in the Russian-Ukraine conflict
There is evidence that several well-known ransomware groups were involved in the Russia-Ukraine war. These groups include LockBit, CoomingProject, and Conti, Stormous. The main motivation for these groups was financial gain, as they targeted critical infrastructure in order to extract ransoms from Ukrainian companies and organizations.
They also targeted individuals, with the aim of extorting money or stealing personal data. Overall, these attacks had a significant impact on cybersecurity in Ukraine and raised serious concerns about the growing threat of state-sponsored hacking.
Conti’s statement of support for the Russian government
On February 25, 2022, the Conti ransomware group announced both its “full support” of the Russian government and its intention to strike back at anyone who organizes cyberattacks or war activities against Russia. This message was posted on the Conti News leak website.
A few hours after posting this statement, the group softened its stance, though it is unclear why. Conti is one of the most professional groups among the criminal organized crime gangs (OCGs), and it has dedicated subgroups akin to departments in a traditional business. It is, therefore, possible that some members did not resonate with the group’s initial statement and pushed back.
#Conti #ransomware just changed the phrasing of their statement regarding Russia’s support. Claiming that they do not ally with any government and condemn the war.@VK_Intel @malwrhunterteam pic.twitter.com/JaLYPlDjwb
— Yelisey Boguslavskiy (@y_advintel) February 25, 2022
Stormous gang supports Russia
We are seeing some encouraging malicious deeds against both Ukrainians and Russians, but some groups do choose to stand behind only one. The Stormous ransomware gang, known for website defacement and information theft, represents itself as a group of Arabic-speaking hackers. The group has been active since 2021, and recently it officially announced its support for the Russian government and its intention to target Ukrainian government institutions such as the Ukrainian foreign ministry.
#stormous #ransomware gang has hit the #ukraine ministry of foreign affairs.
They have not formally declared a side, but this is the second Ukraine network in 2 days… will wait for their comment.#cybersecurity #infosec #threatintelligence #UkraineRussiaWar #cyberattacks pic.twitter.com/tgFKvTFa9I— CyberKnow (@Cyberknow20) February 28, 2022
Attacks during the Russian-Ukraine conflict
During the Russian-Ukraine conflict, a series of cyberattacks were carried out against Ukrainian targets. These attacks included:
- Taking control of Ukraine’s electrical grid-which caused widespread blackouts across the country.
- Infecting Ukraine’s water supply system with malware-which disrupted the delivery of clean drinking water to millions of citizens.
- Interrupting Ukraine’s military command and control systems, allowing Russian troops to advance quickly on the ground.
- In a coordinated cyber campaign, Russian hackers also targeted critical infrastructure in other countries, including the US, UK, and Canada.
- Phishing scams and malware infections were used to gain access to critical systems in Ukraine. They are also believed to have been used in attacks against other countries.
Reports from outside Trend Micro have provided valuable insights into the alleged cyberattacks.
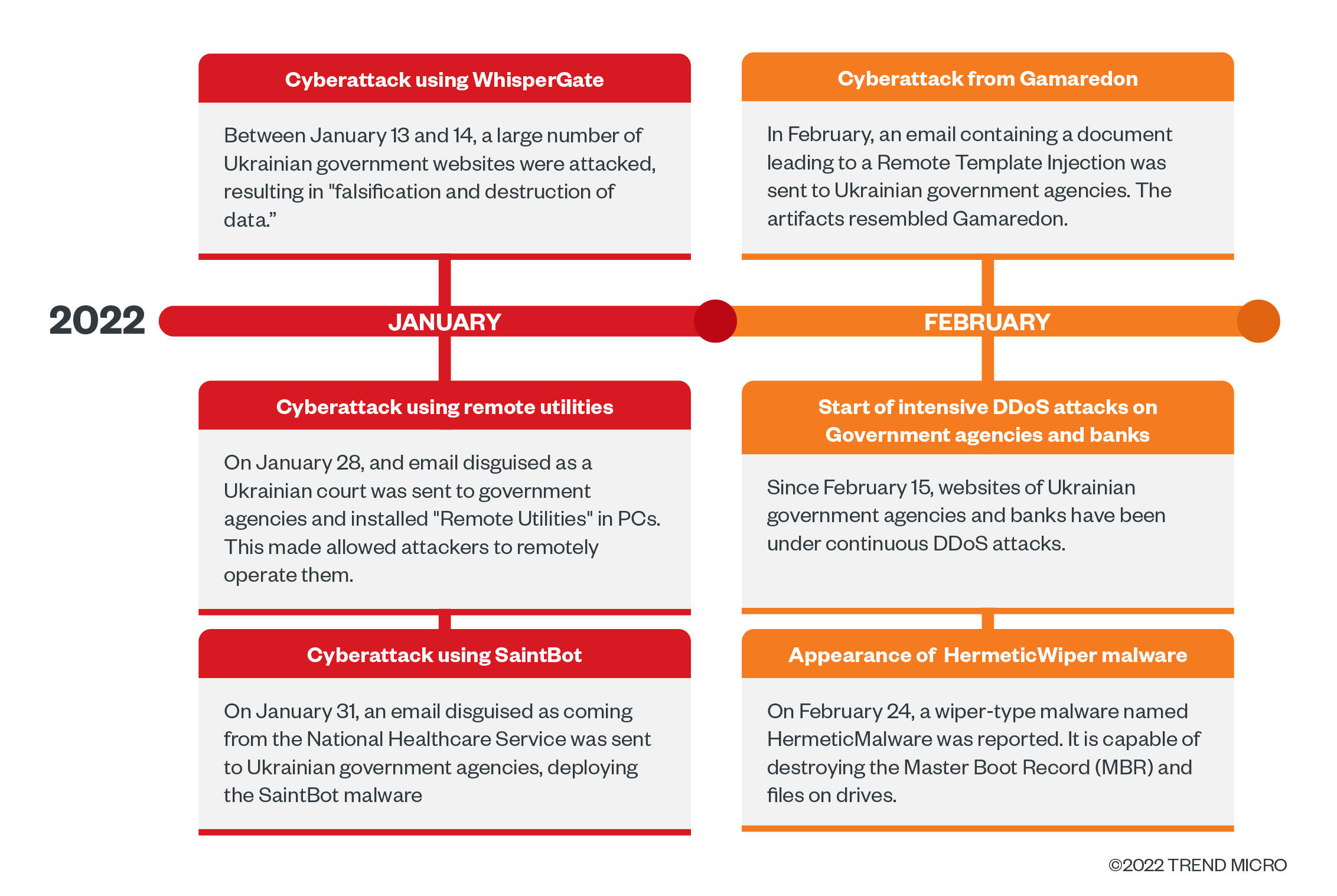
Security incidents in Ukraine reported from January 2022 onward
Russia’s Attack on Ukraine’s Cyberspace
Well, this is not the first time Russia has attacked Ukraine in the cybersphere. In 2015 and 2016, Russia launched a series of attacks on Ukrainian banks, energy companies, and government agencies. These attacks were far less sophisticated than those we saw in 2017, but they still caused significant damage.
After the initial invasion in 2014, Ukraine worked hard to improve its cybersecurity. The country has partnered with the US and NATO to develop new tools and strategies and has implemented many new cybersecurity laws.
Luckily, Ukraine was better prepared this time, and while the attacks caused some disruption, they were not nearly as devastating as they could have been. However, despite this success, it is clear that Russia will continue to target Ukraine in cyberspace. As long as the conflict in eastern Ukraine continues, we can expect to see more cyberattacks from Russian hackers.
However, experts agree that Ukraine remains vulnerable to future cyberattacks from Russia. They also warn that other states are likely to follow in Russia’s footsteps and begin launching their attacks on critical infrastructures worldwide.
President Joe Biden urged U.S. companies to make sure their digital doors are locked tight because of “evolving intelligence” that Russia is considering launching cyberattacks against critical infrastructure targets as the war in Ukraine continues. He passed back-to-back statements warning the Russian government about potential cyber-attacks.
I’ve previously warned about the potential that Russia could conduct malicious cyber activity against the U.S. Today, I’m reiterating those warnings based on evolving intelligence that the Russian Government is exploring options for potential cyberattacks. https://t.co/wO2jJgg5SJ
— President Biden (@POTUS) March 21, 2022
The federal government is doing its part to get ready for potential Russian cyberattacks.
We are prepared to help private sector companies with tools and expertise, but it is your decision as to the steps you’ll take and your responsibility to take them.
— President Biden (@POTUS) March 22, 2022
Closing Thoughts
So, what can we do to protect ourselves from these threats? WeSecureApp lists the following steps to protect against cyberattacks.
- Mandate the use of multi-factor authentication on your systems to make it harder for attackers to get onto your system;
- Deploy modern security tools on your computers and devices to continuously look for and mitigate threats;
- Check with your cybersecurity professionals to make sure that your systems are patched and protected against all known vulnerabilities, and change passwords across your networks so that previously stolen credentials are useless to malicious actors;
- Back up your data and ensure you have offline backups beyond the reach of malicious actors;
- Run exercises and drill your emergency plans so that you are prepared to respond quickly to minimize the impact of any attack;
- Encrypt your data so it cannot be used if it is stolen;
- Educate your employees about common tactics that attackers will use over email or through websites, and encourage them to report if their computers or phones have shown unusual behavior, such as unusual crashes or operating very slowly.
Talk to WeSecureApp today to find out how we can help you secure your network and prevent cyber attacks.