Pegasus – The Threatening Spyware Installed on Mobile Phones
In recent times when everything is digital, you have Alexa, Siri & Google to switch off and on your devices, IoT is trending, CCTV is everywhere for surveillance, even your GPS always gives your Geolocation to network service providers, and Cookies help you view whatever you search. In similar terms this technology is harmful also as if you download any corrupt software, your privacy is compromised, any virus in your phone and your data is lost, spyware or ransomware in your mobile devices and your data is leaked and someone else has control over it.
Today we are discussing the world’s strongest spyware of cyber-espionage “Pegasus”, developed by the NSO group of Israel. The spyware is strong that if it is downloaded on your phone, then the spyware can record audio through the mic, it can even get into your camera to snap pictures. It can share the GPS and push out the Geolocation Coordinates, giving your live location to the bad actor.

The spyware has multi-functionality that It can record and grab the screen image of whatever content is being displayed, It can enter in all the applications downloaded on your device and can read events, SMS’s, and messages of Instant Messengers. It doesn’t stop here, it can also read your mails, contact lists, dialing history, and record calls of specific contacts and get access to the same. It can also retrieve deleted files from devices and take a sneak peek of your browsing history from all browsers on your Phone! and above all this, you might think it takes records present on your phone then you might be shocked by knowing that Pegasus can turn into a key logger too. That means anything that you type and delete on the phone even before sending to anybody, like basic grammatical and spelling errors that are recorded, every touch, even the slightest tap on the screen, gets registered by the spyware and sent to the Bad Actor. Even the encryption on your phone can’t protect devices from the key logger, because they are directly viewing your screen as a user..
So Why is Pegasus taking so much acceleration?
As per Greek mythology, the name says Pegasus was a winged stallion, famous for the inspiration he gives to artists and the power he gives to heroes. He has enjoyed huge popularity since he first appeared in Greek mythology, and he continues to challenge our imaginations today., So in today’s world, Pegasus as spyware helps in cyber-espionage. Recent studies show that Pegasus is used as a monitoring tool and high-profile Government ministers, officers, human rights activists, reporters, opposition leaders, and even Heads of State are targeted. So Pegasus is designed to barge on target person device, collect all data of them, and transfer it to the source or Bad Actors via cryptographic routes. It is possible that Bad Actors are cybercriminals looking for monetary gains or a group of people backed by nation-states who are investigating loopholes and planned activities. The latter is known as Advanced Persistent Threats (APTs). APTs are storing a high level of sophistication, resources, and plans.
Governments of many countries, including Israel, India, Morocco, Hungary, Rwanda, Saudi Arabia, UAE, Azerbaijan, Bahrain, Kazakhstan, Spain, and Mexico, have been identified in the data leak by using Pegasus, whereas many other state governments are yet to give statements on these reports. Amnesty International has voiced that Pegasus was used against the family members of Jamal Khashoggi, the slain Saudi journalist, before and post his murder. An interdisciplinary laboratory based at the University of Toronto confirmed that Jamal’s phone was also targeted with Pegasus and was exploited to get information on his conversation and locations. Over that time Journalists of almost 20 countries have been identified as upcoming targets for spyware.
How does it work?
Pegasus exploits undiscovered vulnerabilities, and bugs, in devices OS, may that be Windows, Android, or iOS. This means a device could be contagious even if it has the latest security patch installed.
An older version of the spyware infected smartphones using a method called “spear-fishing”: A malicious link was passed via text messages or emails to the target. The spyware is used to get activated by clicking the link.
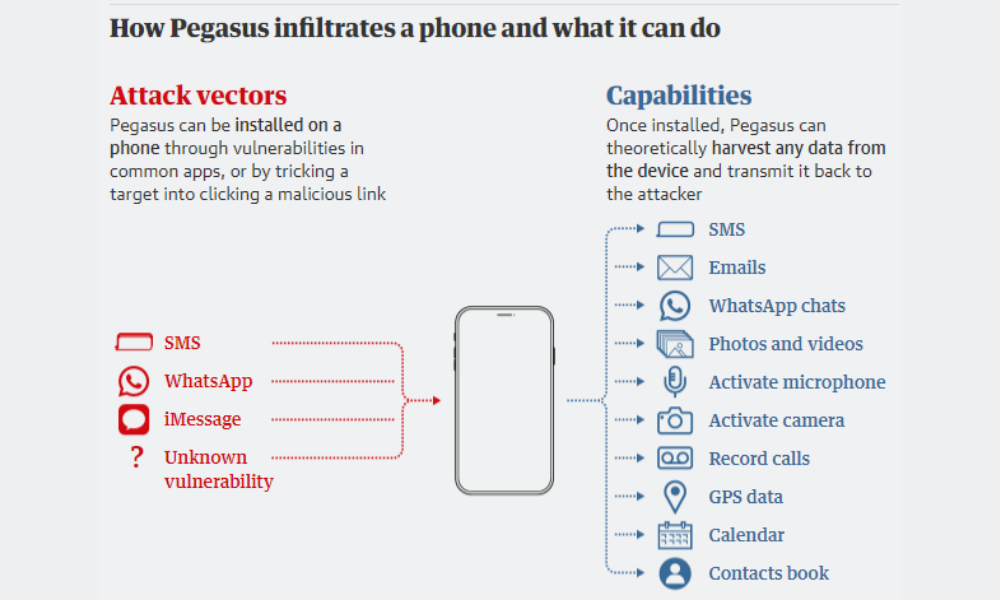
Source : https://www.theguardian.com/news/2021/jul/18/what-is-pegasus-spyware-and-how-does-it-hack-phones
In 2019, Pegasus could exploit the device with a missed call on WhatsApp and even clear the track record of the missed call, This makes it more dangerous by making it impossible for the user to understand that they have been targeted and their security is compromised. In May that year, WhatsApp confessed that Pegasus had intruded and exploited a bug in its application code which as a result infected more than 1,400 Android and Apple Smartphones in this fashion, this includes phones of government officials, journalists, and human rights activists. Post understanding Whatsapp soon fixed the bug.
Pegasus is known for exploiting bugs in iMessage, which gives it backdoor access to millions of iPhones. The spyware can also exploit your phone over a wireless transceiver (radio transmitter and receiver) available near a target.
Prevention & Mitigation
As we know it is challenging to detect the presence of Pegasus Spyware in your device, once it infects a system, But you can put in use the tools like the one stated by Amnesty International called the Mobile Verification Toolkit or MVT, that can decrypt your backups, process and parse records from systems, generate logs, amongst other things, to identify a potential infection and compromise and alert you for threat.
But as we all know prevention is the best defense. Here are a few actions to keep in mind to protect devices from Pegasus.
- You should open links only from trusted sources.
- If you need to check a link, please make sure you are using a reputed Search Engine like Google or MSN and follow the link mentioned in the search results.
- Keep security settings of your browser on as sometimes even browsers can detect malicious links and alert you.
- Disconnect your devices from the network, remove the sim card and switch the device off, to prevent further spread in case you identify the spyware being in your phone.
- Contact your IT support or device service center immediately if you spot something amiss in any of your devices.
- Keep your antivirus up-to-date and make sure it is from a reputed security organization for your device.
- Be vigilant of any new services, applications that have comes up on your device.
- Do not delay in updating your device with the latest version of the software patch released by the OEM (Original Equipment Manufacturer).
In case you are in doubt of a Pegasus or any Spyware attack, Amnesty has introduced the Indicators of Compromise (IOCs) on their GitHub page. A potential compromise on the phone can be easily identified through running applications like MVT and the STIX2 formatted IOCs.





