- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
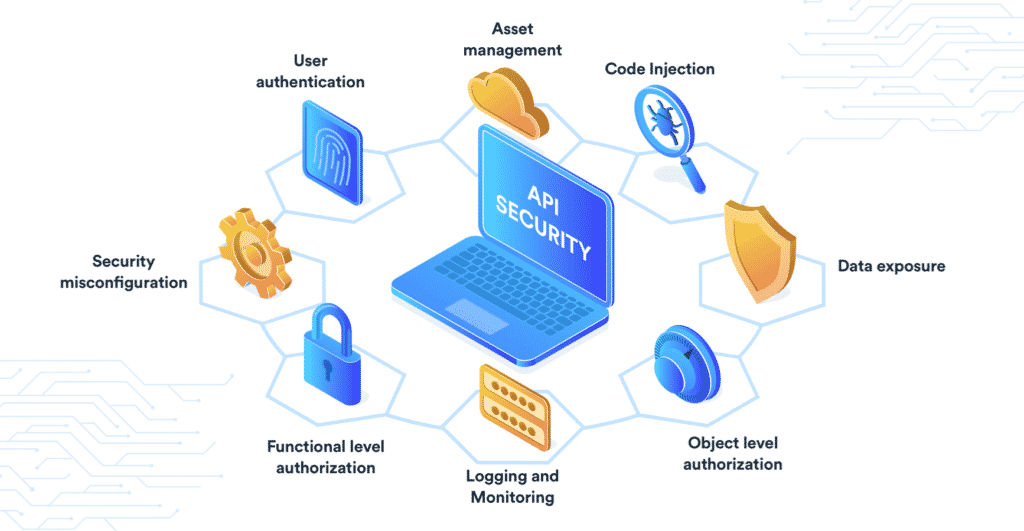
API Security: Top 5 Best Practices to Follow
Digital advancements have transformed human lives in the past few years. There is a complete change out of all the recognition among us. Technology geeks have done their best to give life a new definition, and now we live in a digital world. But this digitization has its own set of threats? Yes, data breaches, cyber crimes have become a major problem now, and particularly the rise of IoT has given it significant momentum. Every day every second, necessary data exchange occurs between the users. API and the application are the modes of interaction.
Using an insecure API will be risky; hackers can access it and steal your database and network. Attackers may seek to exploit vulnerable information-sharing programs, such as MITM or DDoS.
For this, We have listed out the best API security practices that you can follow and protect your network. So, let’s dive in.
-
Encryption
Encryption protects your data and communications from outsiders. To ensure messages are unreadable by unauthorized people, use one-way encryption (TLS) with TLS being the successor to SSL for internal transactions or two-way encryptions if you’re a business that deals in external exchanges.
We should use the latest version of TLS since it blocks weak cipher suites, resulting in uncovered information leaks about clients’ details like their email addresses, phone numbers, bank account passwords, and more.
-
Authentication
Authentication is important to protect against hackers. It’s very common for people and companies alike in today’s digital world, but there are a few ways you can make sure that it doesn’t happen as easily.
The first thing being the person who tries to hack your account should know they’re talking with someone else if their API key or basic access authentication (user/password) isn’t enabled on your system – which will raise the difficulty of hacking into this information from 0-10% up to 100%.
-
OAuth & OpenID Connect
The OAuth protocol is a magical loophole that completely relieves you of the burden of having to remember ten thousand passwords. Through this magic, instead of creating an account on every website and password combination imaginable, all your logins are provided by another provider’s credentials (for example, Facebook or Google).
It’s been reported as one way for users’ accounts to be stolen even with strong security measures in place. So it might be wise to go ahead and delegate responsibility for authorizing these connections.
Tokens are a type of key that an API provider and consumer share to identify the individual. It is advantageous for both parties. It saves time on authentication, does not reveal any credentials, and only receives tokens from third-party servers instead of sensitive data like usernames/passwords or credit card numbers.
The OAuth protocol is in high demand for delegating permissions, but what if you want to go the extra mile and add an identity layer? Open Id Connect does just that by extending 2.0 with ID tokens to secure your APIs even further.
-
Call Security Experts
Install an Antivirus system or ICAP (Internet Content Adaptation Protocol) server; it will help to protect your computer from malware attacks.
-
Share as Little as Possible
Be wary and be vigilant. Lock down your every account, interface, and password as much as possible to make sure that sensitive information is not leaked anywhere it shouldn’t go or seen by anyone who doesn’t need to see the content.
Ensure all of this vital security work stays between just a few people, so no accidental leakages happen because one person left their laptop open on accident in the office break room (yikes!).
Final Thoughts
A public API is a program interface that enables outside developers to create applications and web services. APIs have preferred methods for developing advanced applications. Still, organizations may not realize how these changes impact their data security measures against hackers or other malicious actors in today’s world, where technology evolves quickly.
Many of the tips mentioned above are likely quite familiar to experienced security professionals. If you’re not sure where to start, make your way down from the top and work on them one at a time! No matter how many APIs that an organization shares publicly, its ultimate goal should be to establish solid API policies and manage them proactively over time.
At WeSecureApp, we work hand-in-hand with you to develop and integrate various custom APIs and 3rd party APIs for custom software, web apps, and mobile applications. Our API integration projects aim to save you a ton of money by reducing development time and cutting costs.
Have more questions? Get in touch with our experts