Reinforcing Cybersecurity: Top Frameworks for Safeguarding Your Digital Assets
Introduction
Security has emerged as a top concern for businesses of all sizes and in all sectors as technology continues to develop and the threat landscape becomes more complex. The need for organizations to have a strong cybersecurity strategy in place to safeguard their digital assets and reduce risks is greater than ever due to the rise in cyber attacks. Using cybersecurity frameworks is a vital component of a successful cybersecurity strategy. For enterprises to evaluate, put into action, and manage cybersecurity controls and procedures, these frameworks serve as recognized standards and best practices. Using these frameworks will enable businesses to effectively defend their networks, systems, and data against cyber threats.
The top cybersecurity frameworks that are widely used and acknowledged by businesses worldwide will be covered in detail in this blog post. Organizations seeking to improve their cybersecurity posture and stay ahead of emerging cyber threats must comprehend these frameworks.
Define Security Framework
Security frameworks are methodical, organized approaches or models that offer recommendations, best practices, and benchmarks for putting in place successful security controls and controlling cybersecurity risks within an organization. These frameworks provide a methodical approach to tackling numerous cybersecurity issues, including risk assessment, risk management, incident response, vulnerability management, access controls, and data protection, among others. Security frameworks often provide an organization with a set of guidelines for establishing a strong security posture and defending its digital assets and sensitive data against online attacks.
Where to start when adopting security is one of the difficulties businesses have. Nothing needs to be created from scratch. If you had to investigate every facet of your company’s security, consider the time and resources that would be required. Security frameworks serve as the foundation for your security journey, and how quickly you adapt them is essential. They inform you of the procedures you need to follow in order to build up the initial lines of defense.
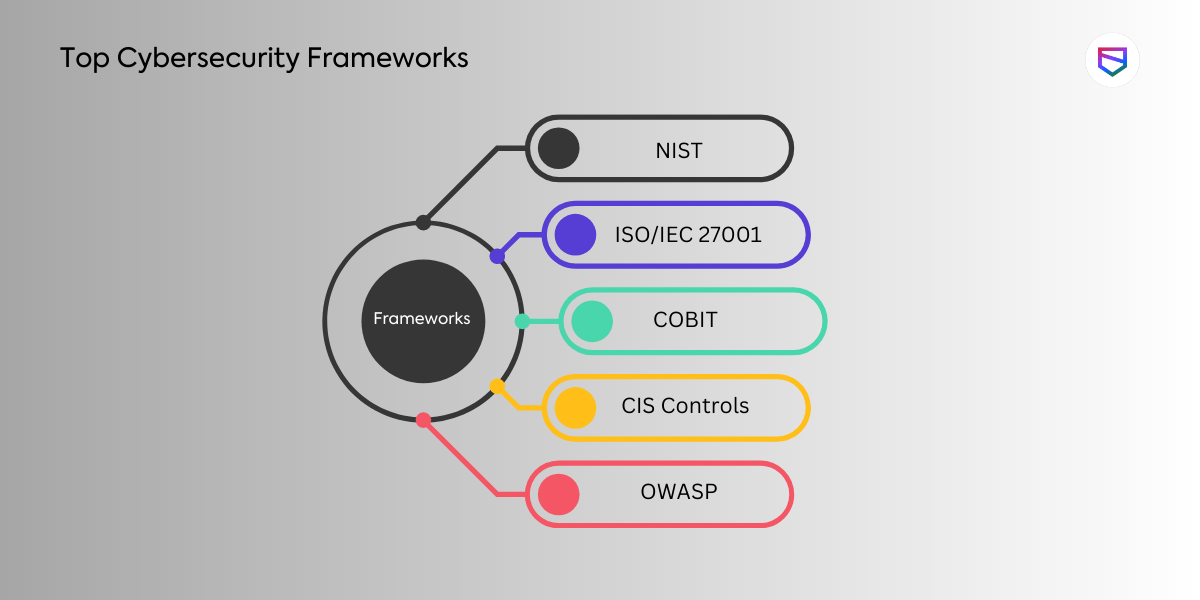
Top Cybersecurity Frameworks for Safeguarding Your Digital Assets
-
NIST Cybersecurity Framework:
A popular approach for safeguarding crucial infrastructure and digital assets is the NIST Cybersecurity Framework. It is a set of principles and best practices for managing and lowering cybersecurity risk in enterprises. The framework has five main components: identity, protect, detect, respond, and recover.
-
ISO/IEC 27001:
ISO/IEC 27001 is a well-recognized standard for information security management. It offers a methodical methodology for handling and safeguarding sensitive data and assets. The standard specifies a set of security controls that businesses can use to reduce security risks and protect their digital assets.
-
COBIT:
ISACA (Information Systems Audit and Control Association) created the COBIT (Control Objectives for Information and Associated Technologies) framework for IT governance and management. It offers a set of regulations for controlling and managing information and connected technological assets. COBIT is made to make sure that technology is used effectively to assist business operations and to align IT with organizational goals.
-
CIS Controls:
The Center for Internet Security (CIS) Controls are a series of recommendations for protecting networks and IT systems. It is a prioritized collection of best practices and security measures for thwarting frequent online threats. The controls are categorized into three groups: fundamental, organizational, and foundational, and they offer enterprises a road map for enhancing their security posture.
-
OWASP:
Dedicated to enhancing software security, the Open Web Application Security Project (OWASP) is a community-driven organization. The 10 most serious security concerns for online applications are listed in the OWASP Top 10. It provides a platform for developers and organizations to find and address vulnerabilities in their software.
Conclusion
In today’s environment, when cyber dangers are always changing, protecting your digital assets is of the utmost significance. WeSecureApp, a top cybersecurity solution, recognizes the need for businesses to protect their digital assets and offers a full range of capabilities to help them do so.
Protecting your digital assets is one of the key components of cybersecurity. By implementing the appropriate frameworks and best practices, organizations can protect their sensitive data and assets from cyber threats. There are many more frameworks beyond the ones we’ve highlighted in this blog that can help organizations protect their digital assets. It is essential to choose the right framework based on the particular demands and specifications of your company.
By integrating with these frameworks, WeSecureApp offers businesses a single platform to manage their cybersecurity posture. Your digital assets will continue to be safeguarded thanks to our platform’s capabilities for continuous monitoring, vulnerability assessment, threat intelligence, and incident response.
Protecting your digital assets necessitates a proactive strategy that includes the adoption of the appropriate frameworks, tools, and practices. Businesses may make sure they are safeguarded against the always-changing cybersecurity risks by working with WeSecureApp.
Recommended Reading
Cyber Security Maturity Assessment for NBFCs: WeSecureApp’s Approach
Smart Strategies for Streamlining Your Cybersecurity Budgets in FY 2023-24
Assumed Breach Assessment Case Study: Uncovering WeSecureApp’s Approach