- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
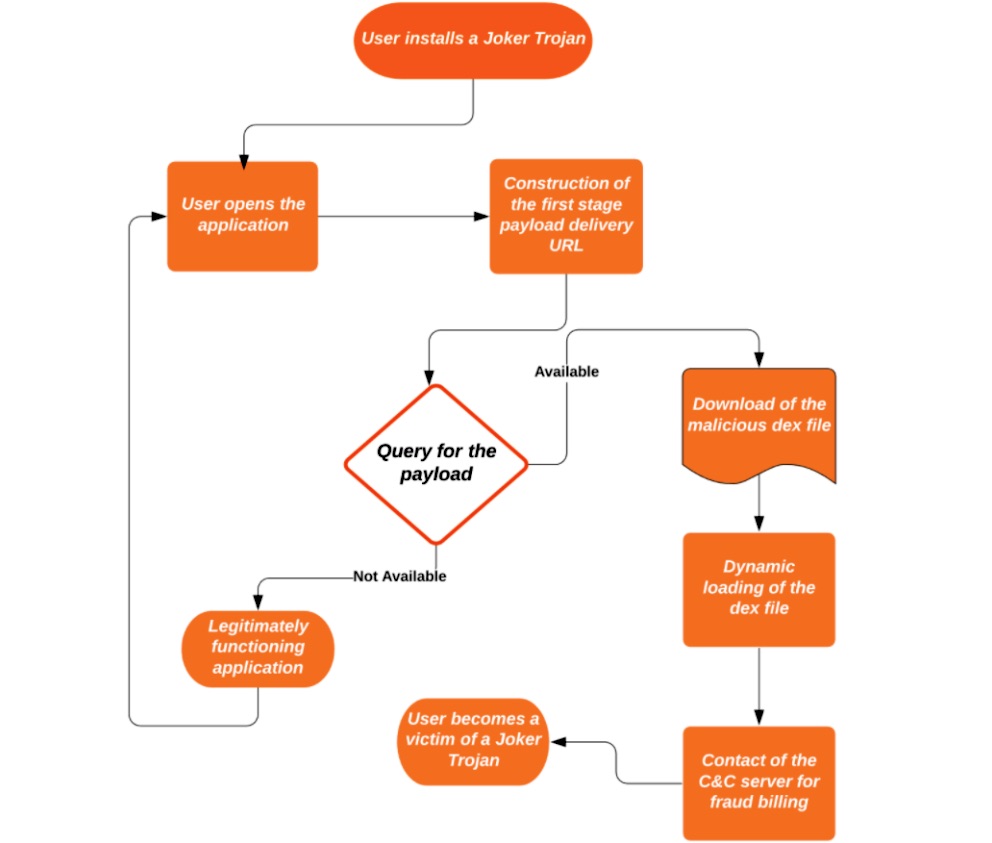
The Return of Joker Malware into Google Play Store
Joker – In cards, it makes you win.. In hosts, it makes you lose
Joker has always been a card in demand, which matches with every other color of the card and makes you Win. This card has got the power to fit himself at any missing card and turn the winning table in your favor. But if it comes as malware in your host/endpoint/mobile devices, then this will make you lose.
Joker is a Trojan malware that is popular to steal your Device Information, SMS, Contact data, and Money also. It comes with infected applications on the Google Play Store (these apps are removed from the play store as of now) and subscribes you for paid services without your consent and it even authenticates the payments by reading OTP from your messages.
How does Joker Malware work
Once you have a malicious application installed on your phone, the Joker malware promptly starts snooping into your contacts, messages, and device information, it steals them and sends them to scammers & fraudsters. Later it starts reading notifications at the backend, without even bringing it to your notice, subscribes the victim to premium service without even knowledge of the user.
So, let us take an example of how this Malware works
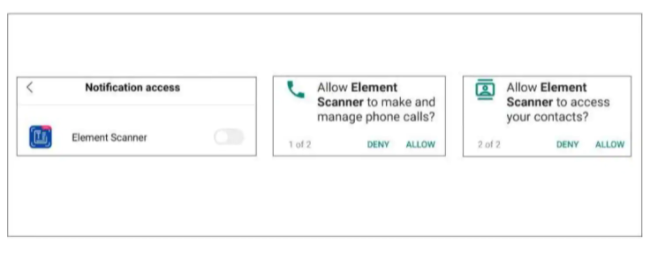
- When the installation is complete it will ask for permission to access your Contact List, SMS, and Notification (Notification is usually used to read your OTP and PIN’s). After receiving permission it will act as a general application for the purpose you have installed it.
- At Background the application starts snooping your device data, and It downloads supporting Payloads, which support the application to hack your device. These payloads are what we call Joker malware.
- These payloads hack your SMS data i.e OTP for a transaction, card data from applications for payments to subscribe premium services and they flush the money out of your account.
- Sometimes they also check for the SIM service provider and subscribe to premium service accordingly.
Here are the eight apps that were recently spotted. If you are a smartphone user, you should immediately check your phone to identify if you have any of the infected apps installed:
- Auxiliary Message
- Fast Magic SMS
- Free CamScanner
- Super Message
- Element Scanner
- Go Messages
- Travel Wallpapers
- Super SMS
If you are using any of these apps, you are at high risk of being defrauded – you must uninstall it immediately.
How to be safe from Joker Malware?
The Joker has been coded and embedded in the apps with so much expertise that it is extremely difficult for Google to catch it, So this is the reason these dangerous apps have been uploaded to the Play Store without even a second thought. The Google security team has identified and removed these apps as quickly as they have discovered, but there are some gestures you can perform to protect yourself from such apps.
- Firstly, always have a reputed organization’s antimalware/antivirus installed on your smartphone and make sure you regularly scan your device for infections.
- Secondly, be vigilant while installing any app on your smartphone, whenever you install anything on your device pay closer attention to what the application exactly does on your phone. This can be done when you launch an app for the first time post-installation, your OS Android, Apple, etc will alert you to what the app is trying to do. The app may request access to your camera, address book, SMS messages, etc.
As and when you see such dialogue or notifications pop up on your screen asking yourself – “Does this application really require access to your SMS or Contact list?” The application may claim that access to SMS is required to share your photos for instance – but in this case, you can always save photos to the built-in Google Photos app or Gallery and send from there.
And why do you need a “special” messaging app? other than your built-in Messages application. SMS, WhatsApp, Facebook Messenger, Telegram are safe and pretty popular – and they are not contaminated with malware too.
Always spare a few seconds to read alerts and Messages while installing apps as they often reveal something fishy – and unwanted – may be happening. If you are in a dilemma, or you have any doubts at all, simply deny the request and delete the app entirely.
Joker is an ultimately smart malware that has affected lots of victims. However, by following the tips mentioned above, there are chances that you can be safe from JOKER.
How can organizations defend themselves from such malware?
To protect themselves against malware like Joker, organizations need to create comprehensive vulnerability management programs and keep all the mobile devices up to date. Also, security teams should educate the rest of the workforce by conducting security awareness programs.
WeSecureApp acts as the first line of defense for organizations
Going forward, organizations should consider using advanced security solutions that ensure the mobile application is released faster without compromising security. If you are looking for mobile application security, you should consider getting in touch with the WeSecureApp team as they utilize thorough manual penetration testing approaches that ensure manual testing of every aspect from the perspective of a real-time attacker.
Get in touch – [email protected]