World’s Worst Passwords: Is it time to change yours?
The awareness of Password Sanitization is very less among people. As per ISO and NIST standards, you must have an 8 characters password with features like an Alphanumeric password having 1 Uppercase, 1 Lowercase, 1 Number, and 1 symbol. This password should be changed quarterly and in the case of a 12-character password, there is no need to change the password periodically. With the whooping rise in data breaches, looking after your passwords is as necessary as ever. One of the key elements of a strong password is its uniqueness.
The easiest password to be hacked.
Cybernews published the Worst Passwords of the Year list: an introduction to the most relatively easy-to-guess and used passwords. The list is defined after evaluating more than 5 million passwords that were leaked on the internet (passwords relating to hacks of adult sites are not included!).
It is reckoned that 10 percent of internet users are at fault for having at least one of the top 25 most popular passwords and 3 percent of people use the weak password similar to ‘123456’ or “abcde”.
Exceptionally lazy numerical and common keyboard patterns feature heavily in the list (e.g. ‘qwerty’ and ‘abc123’). Obvious phrases are popular too; prominent examples of this include ‘password’ and ‘iloveyou’.
Celebrity or City names have always been a popular go-to source of passwords for many unfortunate users. Combining this with a little bit of social profiling and you’ve got a problem: (tip: LionelMessi10 is never a good choice; London123 is not goto password for doubly so if your Facebook page is full of Barca-related posts or Working in that city).
Here’s the 2023 list of the 10 weakest passwords :
- 123456
- 123456789
- Qwerty
- Password
- 12345
- Qwerty123
- 1q2w3e
- 12345678
- 111111
- 1234567890
What are the consequences of a bad password?
The main reason to put up a password is to put in place extra security between a criminal and the network, system, device, program, or account for which you don’t want to publicize the data. So the more prominent/ famous the password, the weaker that hurdle. Here’s a closer look at how you’re in danger…
When it comes to system intrusion, you are not simply dealing with an intruder trying to hack manually using different password permutations and combinations. You are highly likely to encounter a brute-force hacking attempt. With this type of intrusive attack, the hacker uses a tool to work through various combinations of usernames and passwords until a correct combination is found.
There are several common methods of brute force attack (all of which are made a lot easier where the type of password listed above is used!):
Dictionary attack: In this type of attack, hackers make efforts to identify from a long list of possible passwords and use them all. You can strain this quite significantly by making certain guesses about the type of user you are targeting.
Credential recycling: The hacker gets hold of Intel on passwords and usernames from other breaches and uses this data as a basis for a fresh attack of their own. It can often yield results because many of us are guilty of recycling login details for multiple accounts.
Reverse brute force attack: Let’s say that the attacker wants to intrude on a big company. Of all the users on the network, they take a chance that few of the network or host users will be dumb or lazy enough to have the likes of ‘123456’ as their password. Extracting information from sites like LinkedIn, they attempt to match possible user id to this popular password.
Let’s discuss some statistics for password weakness:
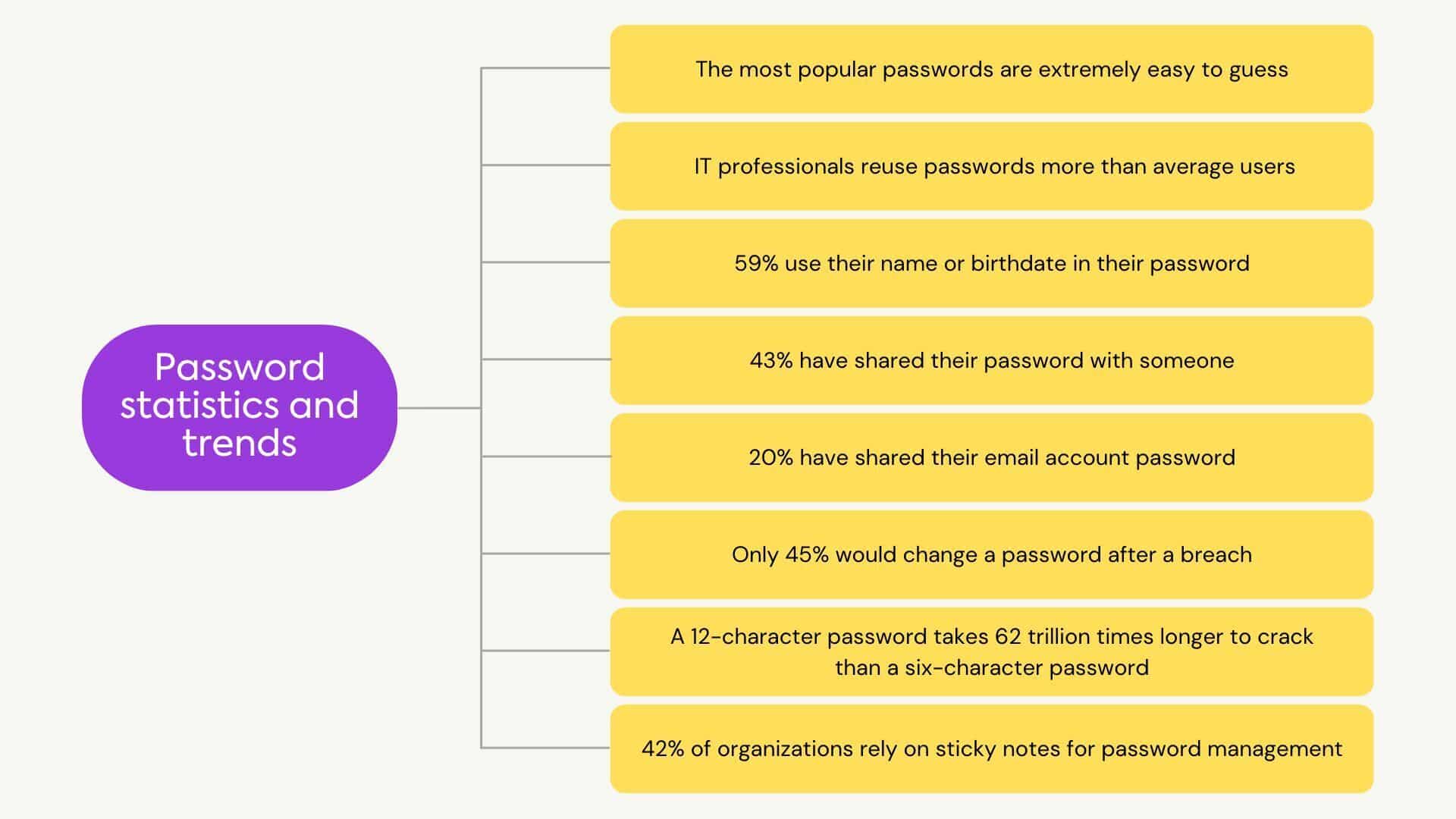
One of the most interesting things is when we looked at which years from 1900-2020 were the most used by people when they made passwords.
Making a rough assumption, people may generally use years in their passwords to mark:
- their birth year
- the year in which the password was created
- a special year
From an analysis, we see that the most popular year was 2010, with nearly 10 million versions of this year used in passwords. The second-most popular used year was 1987 at 8.4 million, and the third was 1991 at nearly 8.3 million.
The most favorite name in the password is Eva, after that was Anna and the least favorite was Darcie. The NBA’s Phoenix Suns, followed by the superior Miami Heat\. Third up is the MLB’s Cincinnati Reds.
The world’s most favorite sport and team used as a combination in password were the NBA’s Phoenix Suns, followed by the superior Miami Heat (full disclosure: I’m from Miami). Third up is the MLB’s Cincinnati Reds. European soccer clubs also appeared 3 times as Liverpool, Chelsea, and Arsenal.
People were interested in mentioning cities like birthplace, favorite spots, etc for their password combination. Abu was ranked 1st, followed by Rome, Lima, Hong Kong, Milan, London, Liverpool, Austin, Antonio & New York.
The favorite food for password was Ice-cream, tea, Pie, Nut & Fish as the top five.
As an organization, How you can safeguard your system from hacking:
1. Implementation of Password Policy
- 8-12 characters in length
- Alphanumeric
- Uppercase
- Lowercase
- Number
- Symbol
- It should be changed every quarter
2. Network configured for alerting and blocking Sync flood
3. User accounts to be blocked after 3-10 wrong attempts basis Industry standard
4. No use of password history 3-12 months
5. No use of dictionary words, names, etc
Conclusion
Strong passwords and password management are crucial for protecting our online accounts from potential security breaches. It is important to create unique, complex passwords and use password management tools to securely store and manage them.
While biometric authentication and other authentication methods offer an additional layer of security, they also have their own risks and limitations. As technology continues to evolve, it is important to stay informed and adapt to new security measures to protect our online identities and personal information.
FAQs
1. Is it safe to use the same password for multiple accounts?
No, it is not safe to use the same password for multiple accounts as it increases the risk of a security breach. If a hacker gains access to one account, they can potentially gain access to multiple accounts if the same password is used.
2. What are some common mistakes people make when creating passwords?
Common mistakes include using easily guessable passwords such as “password” or “123456”, using personal information such as birthdates or names, and using the same password for multiple accounts.
3. How often should I change my passwords?
It is recommended to change passwords every 90 days, or sooner if there is reason to believe that the account has been compromised.
4. Can hackers crack complex passwords?
While complex passwords are more difficult to crack than simple ones, they are not foolproof. Hackers can still use various methods such as brute force attacks to crack complex passwords.
5. Are there any alternatives to passwords for online security?
Yes, there are alternatives to passwords such as biometric authentication and temporary codes sent to a user’s device. However, these alternatives also have their own risks and limitations, and it is important to stay informed and adapt to new security measures as technology evolves.
Recommended Reading:
OWASP Penetration Testing: Your Ultimate Guide!
Reinforcing Cybersecurity: Top Frameworks for Safeguarding Your Digital Assets
Cyber Security Maturity Assessment for NBFCs: WeSecureApp’s Approach
Smart Strategies for Streamlining Your Cybersecurity Budgets in FY 2023-24








