- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
How to Conduct SOC 2 Assessment?
As defined by the American Institute of Certified Public Accountants (AICPA), SOC is the name of a suite of reports produced during an audit. It is proposed for use by service organizations (organizations that provide information systems as a service to other organizations) to issue validated and reviewed reports of internal controls over the information systems to the users of the services. The reports of SOC2 mainly focus on controls grouped into five categories named Trust Service Principles. The AICPA auditing standard Statement on Standards for Attestation Engagements no. 18 (SSAE 18), section 320, “Reporting on an Examination of Controls at a Service Organization Relevant to User Entities’ Internal Control Over Financial Reporting”, defines two levels of reporting, type 1 and type 2. Additional AICPA guidance materials specify three types of reporting: SOC 1, SOC 2, and SOC 3.
Complying with the Service Organization Control SOC2 assessment is of the essence for any service-based alliance or conglomerate. For achieving success in auditing, it is best to conduct a SOC 2 readiness assessment.
The Summation of SOC 2 Report
Being able to understand SOC 2 report is half of the battle won. An organization undergoing audit is expected to implement SOC2 controls. As you are ready for assessment you must concentrate on all its required details to succeed.
In SOC 2 report, firms are expected to provide documentation that provides and showcases transparency about the presence of internal controls of a service organization when the question related to information security arises. The ultimate aim is to give assurance to various internal & external stakeholders of a service organization, like clients, investors, and even auditors.
A SOC 2 report that clears the principal etiquettes with flying colors points that the service-based organization is managed adequately and has necessary controls in place for data protection and information security.
Let us take a look towards various aspects of a service organization that falls under information security:
- Software
- Personnel
- Digital infrastructure
- Data storage
- Data processing
Laws with aspects of Data and Information Security are becoming more severe when it comes to the implementation of controls and investigating security incidents. A first-rate SOC 2 report will be a clear reflection of the steps taken by a service organization in regards to protecting clients’ private information and third-party partners.
What is SOC 2 Type 1?
The Type 1 report of SOC2 details the suitability of the design controls to the service organization’s system. It provides the details of a system at a point in time particularly in its scope, and the board of the enterprise briefing the system, its components, and the available controls in place.
It depicts the availability of controls at a particular point of time as this report is an ‘as of date’ report. The auditor will draft his or her report basis the description of the present controls and review of policies and standards around these controls.
There are multiple benefits that a service entity can achieve by this report. This report can be presented as proof of compliance to the AICPA auditing procedure, as the Type 1 report demonstrates that a SaaS firm has implemented best practices in its place.
What is SOC 2 Type 2?
SOC2 Type 2 can be said that it gives leverage to a higher level of assurance in comparison to SOC 2 Type 1. In order to comply with the requirement, an entity has to pass a thorough assessment/audit of its internal control policies and how the organization follows practices mentioned over a particular period of time by an auditor.
Compliance with SOC 2 Type 2 report, a service enterprise can send an influential message to its potential clients that they are compliant with the best practices on data security and control systems.
Meeting the Trust Services Principles
The primary criteria of SOC 2 reports are catering and keeping it intact its five pillars also known as the Trust Service Principles (TSP).
Generally, the SOC2 assessment will rotate around these five functionalities as it connects the dots of information security. These 5 pillars are called:
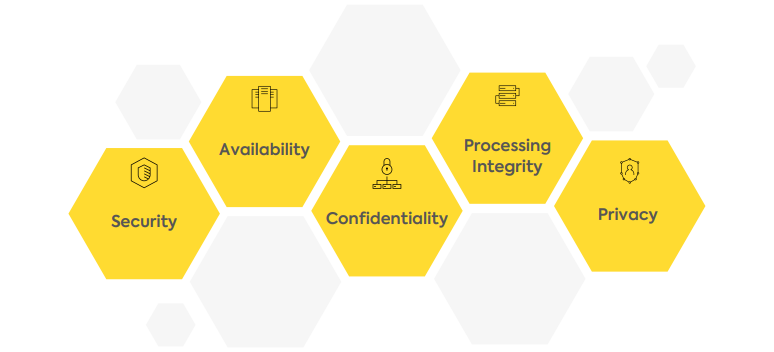
The TSPs avails the criteria that a service-based company must implement in order to achieve the same, which makes the SOC 2 report the go-to methodology. But post-implementation of controls as per TSP’s, full-fledge SOC 2 self-assessment is just because, at any given point in audit, some assessors are very subjective about what they looking for.
As for scope, it is not set in stone to collate the reports addressing all five TSPs. Some documentation includes all 5 aspects, while some have selected Trust Service Principles as it depends upon the applicability and size of the organization. With this uncertainty, it’s necessary for an organization to be ready for all the TSPs.
How WeSecureApp can help in SOC2 Assessments?
WeSecureApp will help you get SOC 2 Implementation and Attestation Support
As the team of professional consultants manages the overall procedure from scoping to assessment and final attestation, The experts will support identifying the applicable list of risks and controls that are required to attain SOC 2 attestation. WeSecureApp assures that the service organization has sufficient ‘internal controls’ over applicable security norms, to ensure any Certified Public Accountant (CPA) for attesting and issuing of SOC 2 reports. WeSecureApp also has contacts that can help the clients to find the correct CPA and get the attestation done.
WeSecureApp’s SOC2 Methodology
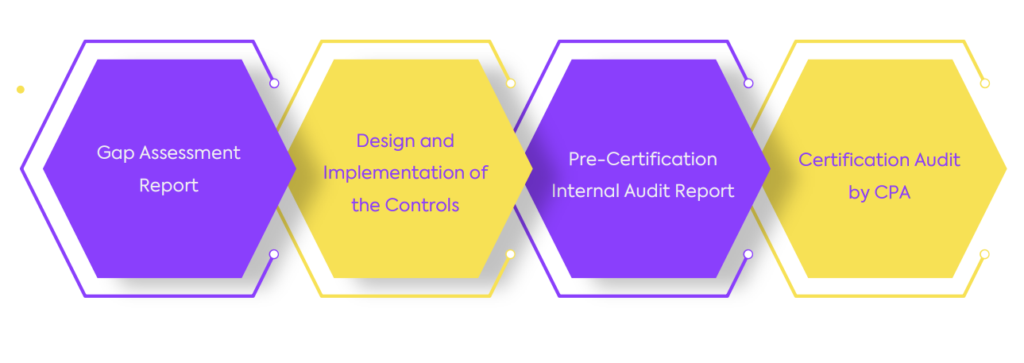
-
- Scoping and Applicability Check
- Coordinate with client to understand and define the assessment scope
- Collection of data related to Procedures, Process & Control Objectives
- Designing & Documentation of applicable controls
- Check portrayal of organization system against the scope and objectives assess for relevance to control design.
- Perform Gap analysis with the controls present in the current environment and reconcile them with the SOC2 applicable controls and risks.
- Assess, Analyse & Review Risks and Design controls to mitigate them by investigating, studying documentation, and observing.
- Determine implementation and validate all the testing procedures.
- Monitor and Track Performance
- This stage involves tracking of identified risks, recording and performing a self-compliance review on a regular interval until all mitigating & compensating controls are adequately implemented.
- Also, address the client with an overview about the performed changes in a given time regarding compliance and providing scores.
- Internal Assessment and verification
- In this phase, the customer has instigated the governance framework incompleteness.
- Team of auditors will perform an internal audit to check whether documented and executed controls are working smoothly in coordination so that they can enable the client to for final attestation.
- Attestation Report
- WeSecureApp team will help the client to find a verified CPA for SOC2 Attestation.
- Scoping and Applicability Check
As your trusted service partner, we are your one-stop shop for all your IT compliance and cybersecurity needs. Our tailored compliance solutions and efficient auditing methods allow your company to not only save on audit and compliance costs, but more importantly, reduces your internal level of effort and time your key personnel spend on annual compliance projects – Talk to Our Delivery Head