- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
What is DevSecOps and its Role in DevOps Architecture
The world of technology is growing at an unprecedented rate. As technologies mature and advance, businesses try to cope up and leverage them. With the pace of developments in the technology space, organizations are having to find new methods of developing and deploying software rapidly, one eye toward security.
Getting ahead in a market of fierce competition isn’t a cakewalk. Therefore, enterprises are now using methods such as DevOps to rapidly plug gaps in their software systems, make upgrades, and reduce time-to-market.
With new tools and a tech-rich philosophy, businesses are now achieving Continuous Delivery (CD) and Constant Integration (CI) to reduce the software development lifecycle.
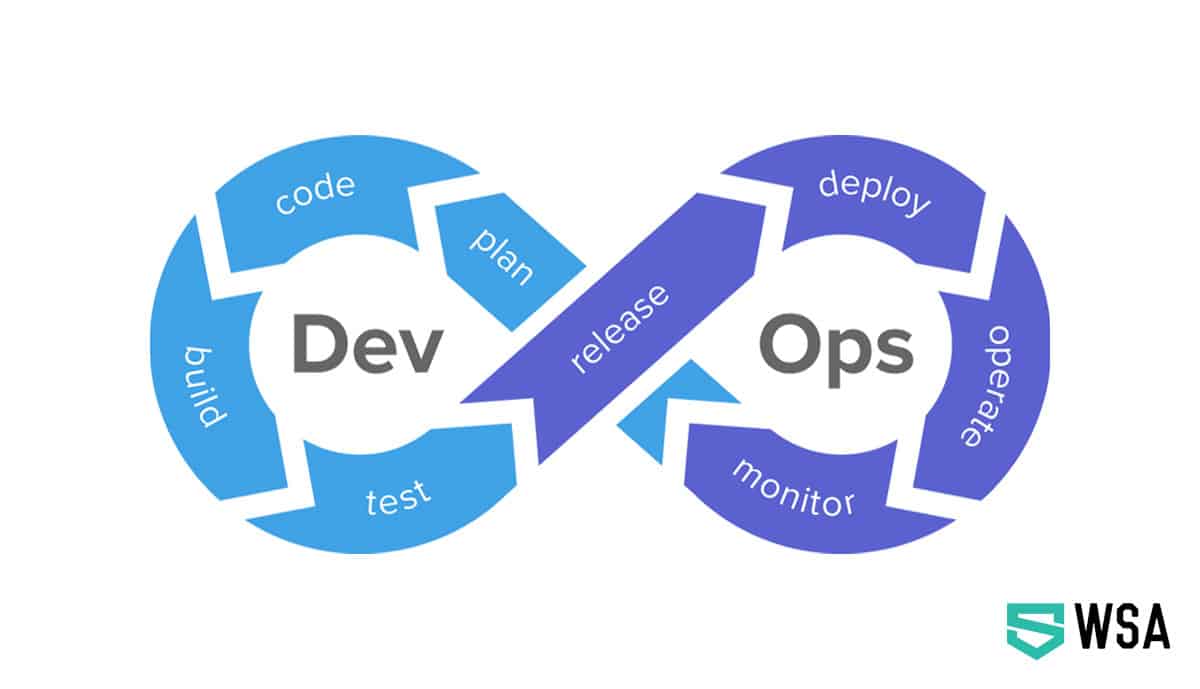
Understanding DevOps
The popularity of CI/CD structures highlights the need to accelerate development cycles and integrate deployment systems within them. This is what gave birth to DevOps- a solution to maintain a stream of service updates that positively impact the customer experience and lead to stable software releases.
The DevOps practice merges the previously disparate functions of development and operations into one cohesive unit that leverages their cross-disciplinary backgrounds to enhance the success of the team.
DevOps supports the collaboration and collection of tools and technologies that sync with each other to form better teams and streamline the development, upgrades, and deployment of software for an IT-driven enterprise.
DevOps highlights the need for tools that enhance transparency and collaboration. As businesses have embraced Software-as-a-service across the enterprise and customer-facing features, they have primarily reduced the time spent on manual handling of tasks.
However, this new technology has unveiled an array of security threats that risk the very foundation of any business.
An Overview of SecOps
SecOps acknowledges the growing need for businesses to take their software security seriously. SecOps is a seamless collaboration of IT operations. IT security teams to work together to manage cybersecurity risks and remediate vulnerabilities.
Again, this is a collaboration of teams that once performed their operations in total solitary of each other. By bringing together these teams, businesses can focus on one common goal- ensuring the security of their IT infrastructure and software.
SecOps teams primarily pursue security and compliance as they look for the most efficient ways to guard servers, cloud environment, and networks. SecOps holds a vital space in multi-cloud environments where security issues get more complicated, and systems expand to meet new needs.
SecOps teams also utilize automation to remediate vulnerabilities and surface them in the first place quickly. Their intense focus on system security can render SecOps teams to stall the development and deployment of a solution but provides a high level of security necessary in today’s’ high-risk landscape.
Combining DevOps and SecOps in DevSecOps
You might have noticed that both DevOps and SecOps emphasize the need for collaboration between the IT and operations teams. Both principles promote the use of cross-disciplinary teams to facilitate a more in-depth understanding of the system. The result of this collaboration is that teams enjoy a meaningful insight into the underlying software instead of knowing about only that part of it which concerns them.
This renewed perspective allows teams to focus on their tasks while also considering how any change they make might impact the overall system.
DevSecOps merges the methodologies of DevOps and SecOps to increase the rate of software deployment while also ensuring high-security arrangements within it. In essence, DevSecOps helps you leverage the best of both worlds.
DevSecOps makes security the responsibility of each member in a project so that the function is not concentrated on a handful of people. With this approach, security teams are in a better position to understand where vulnerabilities might exist as they have a better understanding of the product.
This shared responsibility is built into the culture of collaboration in a DevSecOps practice. Developers learn to adopt and practice high-security coding, while operations teams learn about compliances and gain a fuller view of the system.
This way, businesses can deliver systems that are highly secure right out of the gate. Also, modifications and updates can be readily made if security concerns prop up. DevSecOps combines the speed and stability of DevOps and the security and compliance of SecOps, creating a perfect remedy for software enterprise success.
Is DevSecOps the Right Approach for You?
DevSecOps can be a good fit for your organization if you are constantly battling with the idea of faster time-to-market and necessary security and compliance while balancing the prospect of updates and revisions in the software.
If you are ready to implement DevSecOps within your organization, WeSecureApp’s managed DevSecOps services will help you. We add continuous application security to your CI/CD pipeline, helping you transform operations from DevOps to DevSecOps in three swift steps — planning, automation, and penetration testing.
With a well-rounded DevSecOps implementation, you can gain a competitive edge by accelerating product launch, fixes, updates, and revisions.
Schedule a demo with the best DevSecOps Company in India – Talk to Our Delivery Head