- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
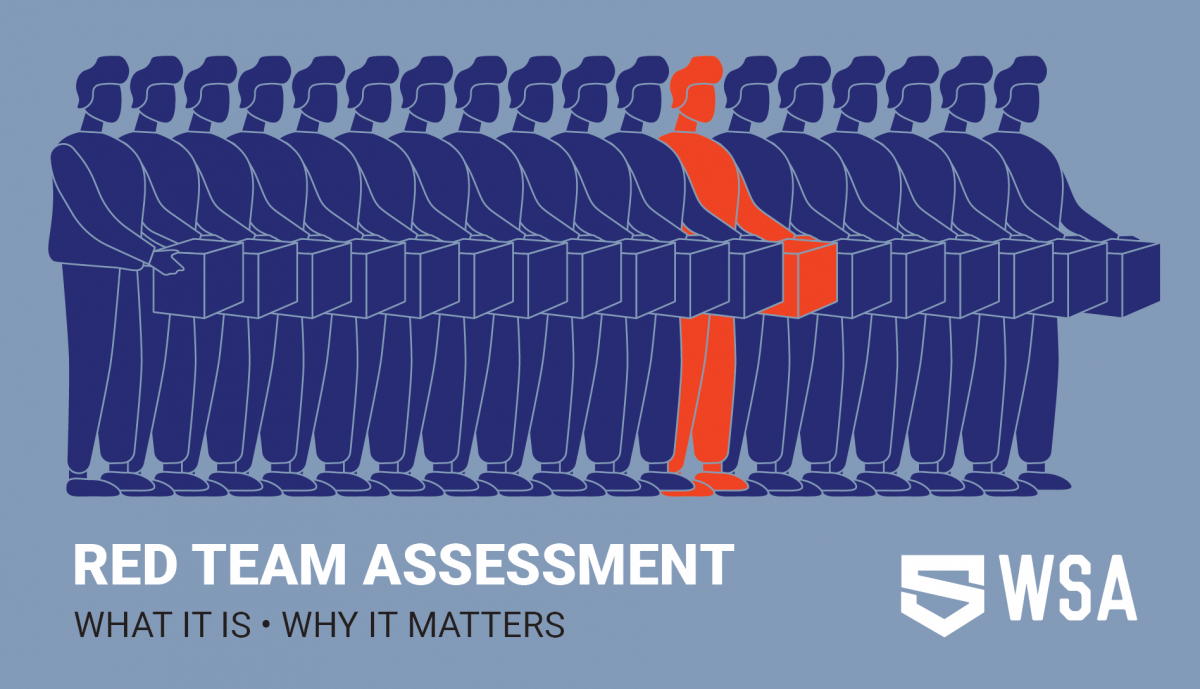
What is Red Team Assessment?
In the world of constantly monitored computer systems, it is often people and not technology that is most vulnerable to cybercriminals. The cost of an attack due to malicious insiders — defined as employees, temporary staff, contractors and business partners, increased to $1.6 million per company, on average. Phishing attacks and social engineering cost $1.4M per company, on average. Together these constitute $3M per company on average. And still, the cost of a breach increases day by day. The best defense for your organization is to develop a thorough defense strategy via Red Team experts.
What is Red Team Assessment:
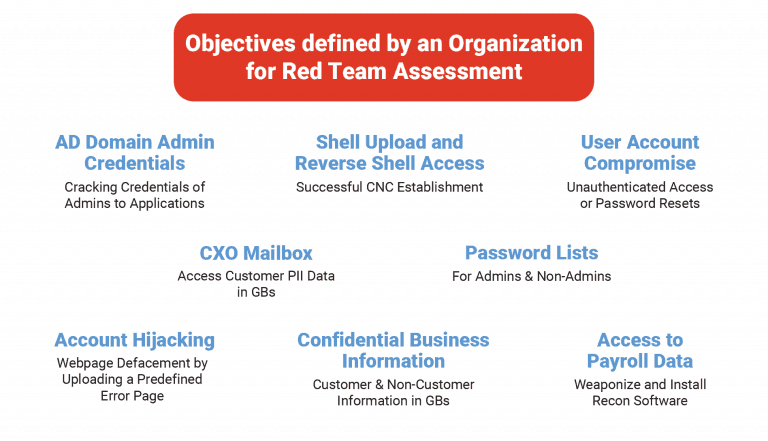 Red Team Assessment Services is an offensive operation with the aim of compromising the target (an organization or its assets) through any possible entry point. The goal of this exercise is to assess how strongly your organization can hold up to a prominent security attack. The result of this assessment helps you in judging the wellness of your incident response team and evaluate existing defense mechanism controls. In Red Team Activity, the hackers will find vulnerabilities in the client’s people, processes and technology further exploit those vulnerabilities further to achieve the desired goals of the organization. There are many activities that are performed in a Red Team Assessment such as
Red Team Assessment Services is an offensive operation with the aim of compromising the target (an organization or its assets) through any possible entry point. The goal of this exercise is to assess how strongly your organization can hold up to a prominent security attack. The result of this assessment helps you in judging the wellness of your incident response team and evaluate existing defense mechanism controls. In Red Team Activity, the hackers will find vulnerabilities in the client’s people, processes and technology further exploit those vulnerabilities further to achieve the desired goals of the organization. There are many activities that are performed in a Red Team Assessment such as
- Application Penetration Testing
- Network & Infrastructure Penetration testing
- Physical Penetration Testing
- Social Engineering
Reconnaissance: The purpose of this activity is to explore the attack surface of your enterprise. With the use of advanced tools and proprietary techniques, all the digital assets exposed online are gathered by our red team experts. After this, they will be enumerated for even more information. This helps us discover various entry points, and evaluate various services which give a great hold on your online presence. The intent of this is to figure out business critical assets on which the predefined objectives are assessed.
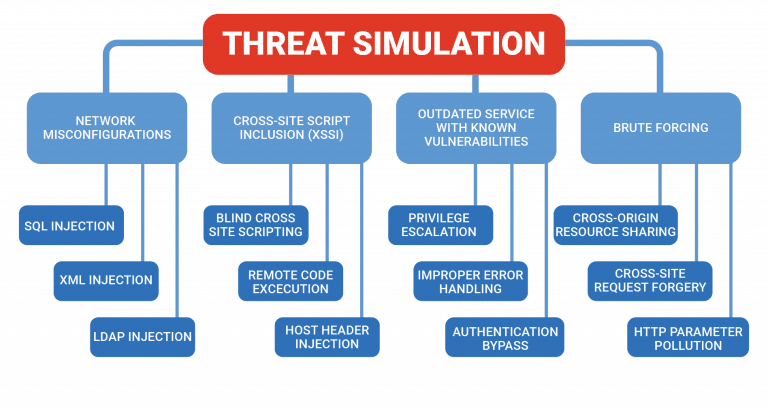
Threat Simulation: After discovering business-critical assets and evaluating their services, they will be assessed for various attack cases with which the pre-defined objectives can be accomplished. Upon completion of the threat simulation, a large number of vulnerabilities will be identified. The red team’s job is to exploit each and every vulnerability, chain those vulnerabilities to extract optimum information, and escalating these vulnerabilities to gain access to root servers and AD domain access.
Social Engineering: This plays a pivotal role in Red Team Assessment. Social engineering is an activity of psychological manipulation, tricking employees or unsuspected users to reveal confidential or sensitive information. The reason why Social engineering is so common is that you don’t need any technical skills to find one person who, in a moment of weakness, opens up an attachment that contains malicious content. The most common attack in social engineering is a phishing attack. This involves spear phishing or email phishing. Imagine you receive an email from a Director or C-level person from your company requesting you to wire transfer money for a confidential deal. Or perhaps you receive an email from a “prince” saying he left his fortune of billion dollars and all he needs is your account details and address to send you the money. Hackers target the employees, stakeholders, or vendors of an organization and perform the following:
- email phishing
- spear phishing
- “vishing” or voice phishing
- In-person meetings
- Spoofing/Identity impersonation.
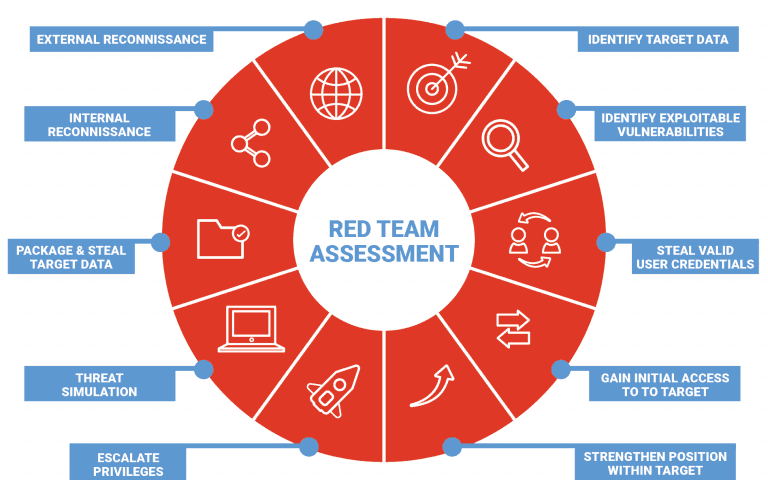
Based on the activities and attacks in Red Team Assessments, you will be able to identify a real-time security breach and evaluate whether your internal team is actually addressing the threats effectively. It will directly help you improve the security posture of your organization and most importantly, you will understand the weak links in terms of people, processes, and technologies and how to improve it.
Improve your organization’s security posture by Red Team Assessment Services: Talk to Our Delivery Head