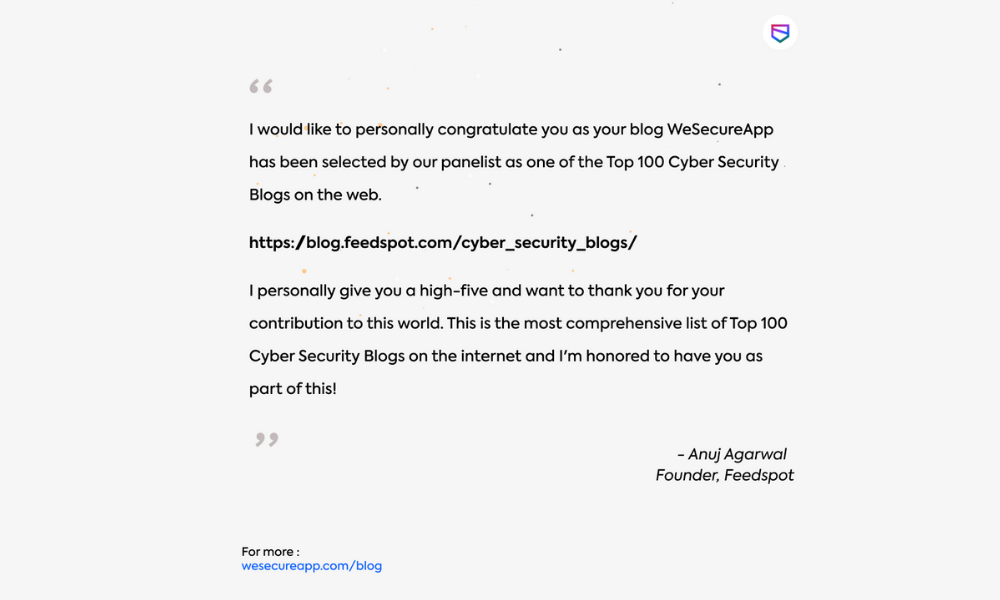
WeSecureApp’s Blog Is Now Among Top 100 Cybersecurity Blogs
WeSecureApp is privileged to be on the list of Top 100 Cybersecurity Blogs, a ranking by Feedspot. Feedspot’s expert editorial team reviews and adds pertinent blogs to a relevant category list. The ranking is based on relevancy, blog post frequency(freshness), social metrics, domain authority, traffic, and many other parameters.
WeSecureApp’s blog is a leading information sharing platform in the information security space focusing mainly on Cyber Security, Red Team Assessment, Vulnerability Assessment & Penetration Testing, Write up’s on the latest phishing and ransomware, Compliance and audits, and many more.
The blog posts on the WeSecureApp platform share the latest information in the cyber security space and emerging security technologies with research-based opinions on their advantages and disadvantages. The blog posts written by cyber security experts are a one-stop-shop for all news related to cyber attacks, data security and vulnerabilities, and many more.
Today, the security of data in the digital world is the most crucial task. At WeSecureApp, we understand how important data security is to every client, and so we offer equally reliable services. Your data and information stay safe with us and it is not at the risk of being misused in any sense. With readership growing aggressively, we hope to bring the best ideas, information, and latest on cybersecurity issues.
Every task carried out by our team is done so with full honesty, efficiency, and integrity. We take ownership of every project and work on it like it is our own, which enables us to offer correct advice, deliver the right information, work with ethics, and never compromise user information.
About WeSecureApp:
WeSecureApp is helping organizations in minimizing the threat landscape which gets inherited with industry and business domains. Having attained industry expertise, WeSecureApp addresses the challenges with the use of unique technology and managed solutions that are designed and developed internally.
Read more
Red Team Assessment versus Penetration Testing
Recent Cyber Attacks & Data Breaches in 2022
Ransomware as a Service – The Trending Business Model for Attacks









