How do Red Team Exercises help CISO to Validate the Security Controls Effectively?
Red Team Exercises are one of the best ways for CISOs to validate the security controls effectively. By simulating a real-world attack, Red Team exercises help organizations identify their vulnerabilities and determine how well their security controls stand up against a malicious actor.
Today 82% of companies conduct Red Team exercises as part of their overall security program, and of those, 71% believe that Red Team exercises have improved their security posture.
So, what do you think about the Red Team? How do their exercises help CISOs to validate the security controls effectively? Are you looking for more information about the Red Team? If yes, continue reading.
In this blog, we’ll discuss:
- Differences between Red Teaming and Penetration Testing
- How Red Team Works
- How Red Teaming Validates Blue Team’s Work
- Benefits of Red Teaming
- Better Choice Between in-house red team and outsource Red Team
Differences between Red Teaming and Penetration Testing
First, let’s take a look at the differences between Red Teaming and Penetration Testing.
Penetration testing is designed to identify vulnerabilities in an information system that could be exploited by an unauthorized user. It attempts to simulate the actions of a malicious attacker who is trying to gain access to the system’s resources.
On the other hand, Red Teaming is designed to help organizations identify their vulnerabilities and determine how well their security controls stand up against a malicious actor. Red Teams are often composed of experienced professionals who have a deep understanding of how to exploit vulnerabilities and bypass security controls.
Therefore, Red Teaming is more focused on identifying the organization’s vulnerabilities, while Penetration Testing is more focused on identifying vulnerabilities that could be exploited by an unauthorized user.
How does the Red Team Work?
Now that we have a basic understanding of the differences between Red Teaming and Penetration Testing, let’s take a closer look at how Red Teams work.
Red Team exercises are typically conducted in three phases:
Planning Phase – In this phase, the Red Team develops a plan of attack and determines how they will attempt to exploit the organization’s vulnerabilities.
Execution Phase – In this phase, the Red Team executes the plan and attempts to exploit the organization’s vulnerabilities.
Evaluation Phase – In this phase, the Red Team evaluates their success and provides feedback to the organization.
How Red Teaming Validates Blue Team’s Work
One of the primary purposes of Red Teaming is to validate the work of the Blue Team. The Blue Team is responsible for defending the organization against attacks, so it’s important to ensure that their efforts are effective.
Let’s understand how Red Teaming validates the work of the Blue Team with an example.
Suppose the Blue Team has implemented a security control that is designed to prevent attackers from accessing sensitive data. The Red Team can test this security control by attempting to access the data without using the approved methods. If they are successful, then the security control is not effective and needs to be improved.
Therefore, Red Teaming helps to identify the vulnerabilities that are being exploited by attackers, as well as the security controls that are not effective. This information can be used to improve the organization’s security posture.
Benefits of Red Teaming:
Now that we understand how Red Team Exercises help CISOs validate the security controls effectively, let’s take a look at the benefits of Red Teaming.
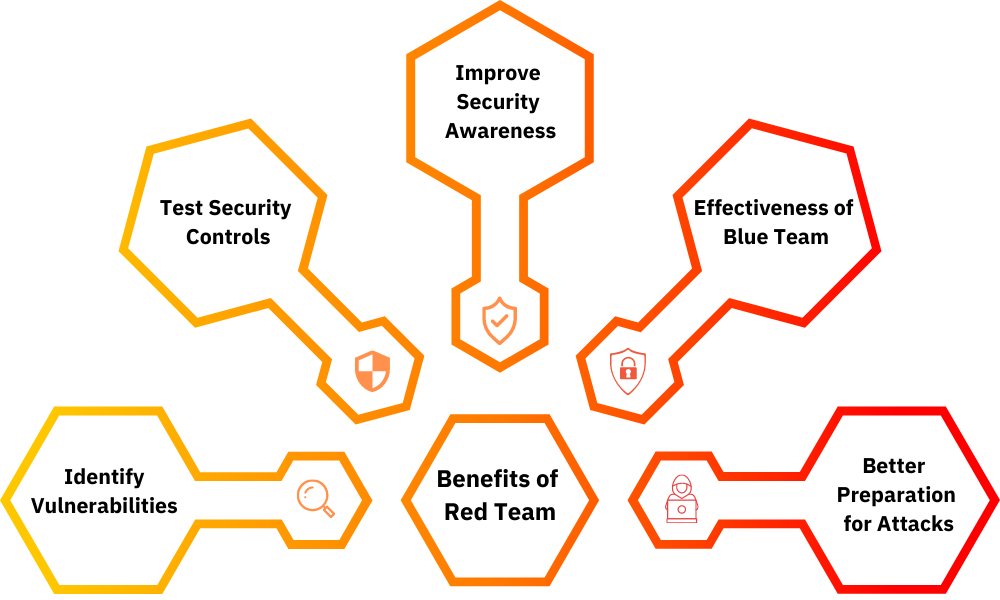
Identify Vulnerabilities – The primary benefit of Red Teaming is that it helps organizations identify their vulnerabilities. By understanding how attackers can exploit their vulnerabilities, organizations can take steps to address these weaknesses and improve their security posture.
For example, an organization discovers that its systems are vulnerable to a specific type of attack. They can then take steps to protect their systems from that attack.
Test Security Controls – Red Team exercises help to test the effectiveness of security controls. If a security control is not effective, then the organization can take steps to improve it.
For example, if a security control is not able to prevent an attacker from accessing sensitive data, then the organization can improve the security control or find a different solution.
Improve Security Awareness – Red Team exercises also help to improve security awareness within an organization. By exposing employees to real-world attack scenarios, employees are more likely to be aware of the risks and take steps to protect themselves. For example, an organization conducts a Red Team exercise in which employees are tricked into downloading a malicious file. Employees who participate in the exercise will be more likely to avoid downloading files from untrusted sources in the future.
Increase the Effectiveness of Blue Team – Red Teaming also helps to increase the effectiveness of the Blue Team. By identifying the vulnerabilities that are being exploited by attackers, the Blue Team can focus its efforts on protecting the organization from those attacks.
Better Preparation for Attacks – Finally, Red Team exercises can help organizations to better prepare for attacks. By understanding how an attacker would attempt to exploit their vulnerabilities, organizations can be better prepared to defend against those attacks.
A better choice between the in-house red team and outsourced red team:
There are several factors to consider when making the decision between in-house and outsourced Red Team.
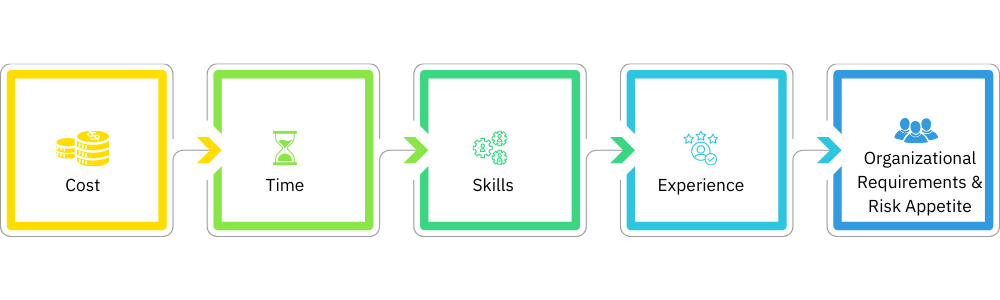
Cost – The first factor is cost. In-house Red Teams are typically more expensive than outsourced Red Teams because they require dedicated resources (e.g. employees, tools, etc.). Whereas, outsourced Red Teams are typically less expensive because they leverage the resources of the service provider.
Time – The second factor is time. In-house Red Teams require more time to set up and manage than outsourced Red Teams. Outsourced Red Teams are ready to go right away and do not require any additional setup time.
Skills – The third factor is skills. In-house Red Teams require employees who have the necessary skills to carry out a Red Team exercise. Outsourced Red Teams typically have employees who are skilled in penetration testing and red teaming.
Experience – The fourth factor is experience. In-house Red Teams typically have more experience than outsourced Red Teams. This is because outsourced Red Teams are typically composed of employees from multiple organizations.
Organizational Requirements – The fifth factor is organizational requirements. In-house Red Teams are typically better suited for organizations that have the necessary resources (e.g. employees, tools, etc.). Outsourced Red Teams are typically better suited for organizations that do not have the necessary resources.
Organizational Risk Appetite– The In-house Red Teams are better suited for organizations that are willing to take on more risk. Whereas the outsource Red Teams are better suited for organizations that want to mitigate their risk.
Therefore, the right choice is to outsource Red Team if the company has a lack of resources and wants to mitigate its risk. However, if the company is willing to take on more risk, then the right choice is the in-house Red Team.
Conclusion
Red teaming is an important process for organizations that want to improve their security posture. By identifying and exploiting vulnerabilities, red teams help organizations to better understand their security risks and take steps to mitigate them.
There are several factors to consider when making the decision between in-house and outsourced Red Teams, such as cost, time, skills, experience, and organizational requirements. In the end, the right choice for an organization depends on its specific needs and risk appetite.
Let us help you find and validate your vulnerabilities – Explore Our Services
Scale up your Vulnerability Management by single platform – Strobes