- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
How Not To Pay A Ransom: 3 Tips For Enterprise Security Pros
How is Ransomware Ransacking Enterprise Revenues?
At the beginning of each year, we are ushered into the concept of what the new “new” is: Fifty is the new 40, red is the new blue and so on. Ransomware is a malware which has been rapidly gaining attention. It is typically introduced into a corporate network through an employee. From there it spreads quickly and executes a crypto virology attack, affecting systems adversely. Subsequently, hackers demand a ransom to restore the data, and the malware has inflicted unprecedented damage and the threat of it intensifying looms large over the cyber world.
Colonial Pipeline had to pay a $4.4 million ransom to get its oil operations back up and running after a group of hackers shut it down in 2021. The highest-ever ransom demand came from REvil at the beginning of July of last year: $70 million. Despite the fact that government and homeland security organisations advise businesses against trying to pay ransoms, the Veeam 2022 Ransomware Trends Report found that 76% of firms admit to paying ransomware attackers, with a third being unable to recover their data.
The highest average ransom payments were in manufacturing at $2.04 million, as well as energy and utilities at $2.03 million. The lowest average ransom payments were in healthcare at $197,000 and state/local governments at $214,000.
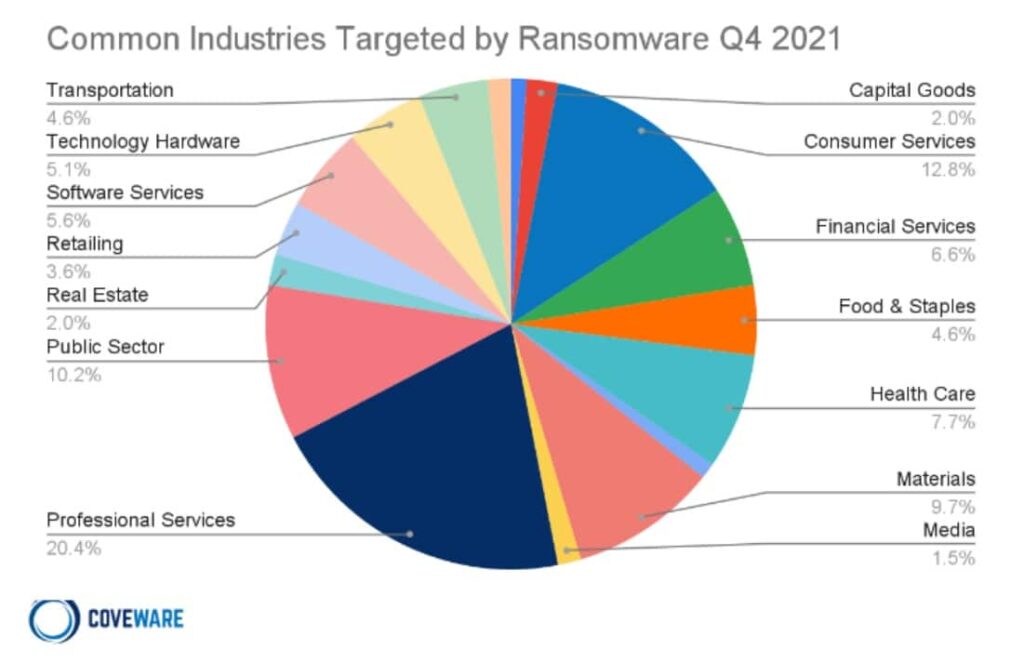
Industry experts feel that this is only the beginning for ransomware
Most organizations are moving towards a distributed enterprise system which requires connecting several enterprises to corporate networks. The arrival of the Internet of Things is also expected to make the corporate networks extremely vulnerable to ransomware attacks.
The question which arises now, is how do we deal with such a problem? How can an organization secure sensitive information?
Every business should have a thorough understanding of its data and various access points. If this information is gathered diligently, it would lay a rational basis for better information management. Governance policies also play a key role in reducing the impact of ransomware attacks.
Let us now look at some of the ways of dealing with ransomware threat:
TIP 1: Have a Thorough Understanding of Data as well as its Organization
An enterprise needs to be thoroughly prepared and informed about a probable ransomware attack. Five groups—Conti, LockBit, Pysa, REvil, and Maze/Egregor—were responsible for more than half of all ransomware attacks over the past two years, it is predicted that advanced variants of these groups will surface with newer stealth functionalities.
For example, newer versions may begin encrypting information silently. These encrypted files could be backed up, but hackers would be capable of stealing both files on the systems and in the backup.
Sounds pretty scary, yes?
Hence, it is important for businesses to preemptively prepare for an attack by categorizing and assigning information by the relative value, sensitivity, and risk. This categorization of data would lead to proper record management and information governance, thereby ensuring greater security. Such an organization of data would help the firm recover ransomware-affected files without paying a ransom.
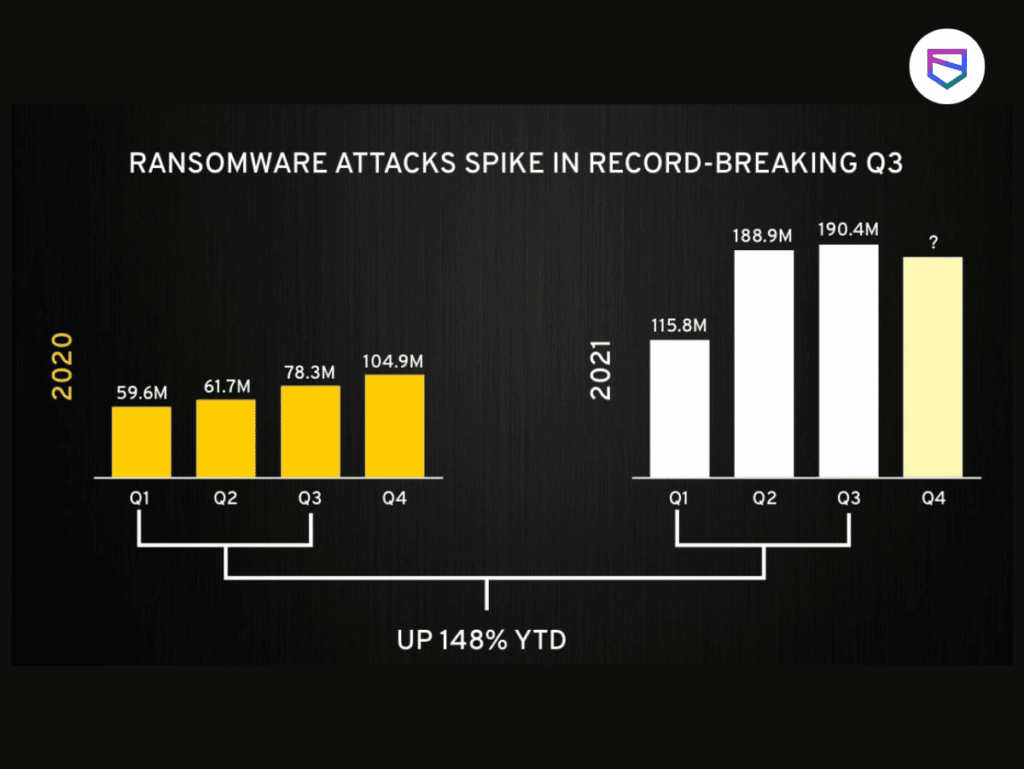
TIP 2: Have a Stable Backup Strategy in Place
Traditional backup practices may not provide an organization with ample security. An effective enterprise security strategy should entail quick backup and recovery solutions. Storing recently revised files and isolating the backup should be a critical component of the backup strategy. This ensures that the malware cannot access backup data.
A while ago, Hollywood Presbyterian hospital in California had to pay its attackers $17,000 in bitcoins. They fell prey to the ransomware attack primarily because they were not sure whether infected systems containing sensitive data or not. Had they followed cogent record-keeping methods, they wouldn’t have had to be in the position of putting their information in jeopardy.
TIP 3: Adopt Multi-layered Defense and Anti-Ransom Tools
The nature of Malware is dynamic, and hackers are always finding new ways to intrude into a corporate network. Thus, it is imperative to have a paid anti-virus software with an automatic update feature and a real-time scanner.
Enterprises should introduce training to its employees to help them understand ransomware, and how they can work towards securing their company’s environment. Backing up data is a safe move, but not a winning solution. As a part of the multi-layered defense, it is essential to secure from endpoints to networks and servers.
Ransomware attacks are typically caused by employees opening spam emails. Companies must focus their efforts to recognize and block ransomware-related emails.
All suspicious attachments should be pruned promptly and not allowed to reach enterprise servers – no matter where they are – whether virtual, physical or on the cloud. A colossal scale of ransomware can be blocked at web and email-levels.
With upcoming new variants and the triumph of the “ransomware-as-a-service” business model, it is predicted that the rise of ransomware will continue. Hence, it is important to build a strategy to reinforce cybersecurity and protect your enterprise from ransomware attacks. Ransomware has proven to be an extremely effective tool for cybercriminals. The loss of access to their data has motivated many organizations to pay large ransoms to retrieve it.
Finding the right cybersecurity partner can help you in understanding, detecting, and defending yourself from a potential ransomware attack.








