Identifying Security Misconfiguration in Enterprise Networks
In today’s digital landscape, where cyber threats continue to evolve, one of the critical aspects that often gets overlooked is security misconfiguration. It is an all-too-common vulnerability that can leave enterprises open to exploitation by malicious actors. In this article, we will explore the importance of identifying and addressing security misconfigurations in enterprise networks and discuss best practices for prevention. Let’s dive in!
What is Security Misconfiguration
A security misconfiguration is a common category of security issue in software and systems. It occurs when a system, application, or service is not properly configured, leaving it vulnerable to attacks or unauthorized access.
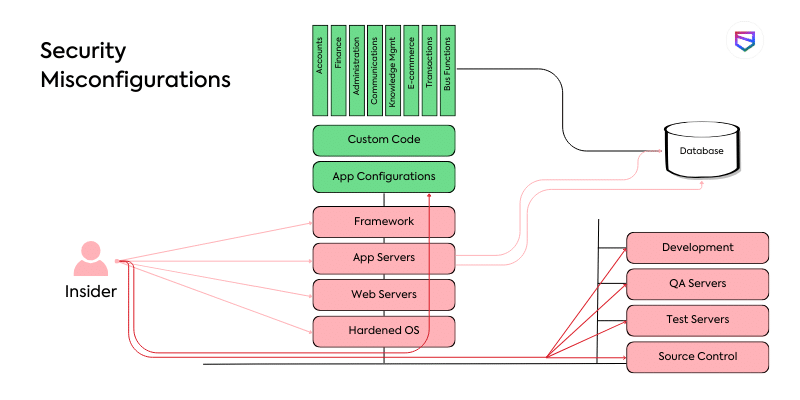
Common Security Misconfigurations in Enterprise Networks
1. Default Passwords and Usernames
One of the most prevalent security misconfigurations is the use of default or weak passwords and usernames. Many enterprises overlook the importance of changing default login credentials, making it easy for attackers to gain unauthorized access.
2. Unpatched Systems and Software
Failure to regularly update and patch systems and software is another significant security misconfiguration. Outdated systems can contain vulnerabilities that are easily exploited by attackers, putting sensitive data at risk.
3. Weak or Outdated Encryption Protocols
Using weak or outdated encryption protocols can compromise the confidentiality of data transmission. Enterprises need to ensure that robust encryption algorithms and protocols are implemented to maintain the integrity and privacy of their communications.
4. Improper Access Controls
Misconfigured access controls can grant unauthorized individuals more privileges than necessary. This can lead to data leaks, unauthorized modifications, and even complete system compromise.
5. Misconfigured Network Services
Incorrectly configured network services pose a significant threat to enterprise networks. Services such as firewalls, routers, and web servers should be properly configured and regularly audited to minimize vulnerabilities.
6. Lack of Logging and Monitoring
Without adequate logging and monitoring systems in place, enterprises may miss crucial indicators of suspicious activities. Monitoring network events and maintaining comprehensive logs is crucial for the early detection of security breaches.
Risks and Consequences of Security Misconfigurations
The risks and consequences of security misconfigurations can be severe, and enterprises must be aware of them. Here are some potential outcomes:
1. Unauthorized Access to Sensitive Data
Security misconfigurations can provide unauthorized individuals with access to sensitive data, such as customer information or intellectual property. This can lead to financial losses, legal consequences, and damage to an enterprise’s reputation.
2. Data Breaches and Loss of Customer Trust
Inadequate security measures can result in data breaches, exposing sensitive information to the prying eyes of cybercriminals. This breach of trust can cause customers to lose confidence in the enterprise’s ability to protect their data, leading to a loss of customers and damage to the brand’s reputation.
3. Financial Losses and Legal Consequences
The fallout from a security misconfiguration can be costly for an enterprise. In addition to potential fines and legal actions, there may be a need for incident response, forensic investigations, and recovery efforts, all of which can result in significant financial losses.
4. Damage to Brand Reputation
Word spreads quickly when a security breach occurs. News of a security misconfiguration could damage an enterprise’s brand reputation, making it difficult to regain the trust and loyalty of customers.
Techniques for Identifying Security Misconfigurations
To proactively identify security misconfigurations, enterprises should employ various techniques and strategies:
1. Regular Vulnerability Scanning
Conducting regular vulnerability scans helps identify potential security misconfigurations and vulnerabilities in the network. This allows enterprises to stay one step ahead of attackers by addressing these issues promptly.
2. Penetration Testing
Penetration testing, also known as ethical hacking, involves attempting to exploit vulnerabilities in a controlled manner. By simulating real-world attacks, enterprises can discover and address potential security misconfigurations before hackers exploit them.
3. Configuration Analysis Tools
Using configuration analysis tools can help enterprises identify potential security misconfigurations across their network devices and infrastructure. These tools scan configurations and provide insights on misconfigurations that need attention.
4. Security Audits and Assessments
Regular security audits and assessments play a crucial role in identifying security misconfigurations. These comprehensive evaluations help enterprises ensure that their networks adhere to industry standards and security best practices.
5. Monitoring and Alerting Systems
Implementing robust monitoring and alerting systems allows enterprises to detect and respond promptly to security misconfigurations. Real-time alerts enable the identification of suspicious activities and prompt action to mitigate potential risks.
Best Practices for Preventing and Addressing Security Misconfigurations
To prevent or address security misconfigurations effectively, enterprises should follow these best practices:
1. Regularly Update and Patch Systems
Staying up to date with the latest security patches is crucial in mitigating security misconfigurations. Regular system updates help address known vulnerabilities and minimize the risk of exploitation.
2. Implement Strong Access Controls and Password Policies
Enforcing strong access controls and password policies ensures that only authorized individuals can access critical systems and data. Enterprises should implement multi-factor authentication, role-based access controls, and regular password changes to enhance security.
3. Enable Logging and Monitoring of Network Activities
Comprehensive logging and monitoring of network activities enable enterprises to detect unusual or suspicious behavior promptly. This allows for timely response and mitigation of security misconfigurations before they can be exploited.
4. Encrypt Sensitive Data
Encrypting sensitive data both at rest and in transit adds an extra layer of protection against unauthorized access. Enterprises should implement robust encryption algorithms and protocols to safeguard their valuable data.
5. Follow Security Configuration Guidelines and Industry Best Practices
Adhering to security configuration guidelines and industry best practices is essential for preventing security misconfigurations. These guidelines provide a baseline for secure network configuration and help enterprises identify potential issues.
Recommended Reading
The Penetration Testing Guide for Compliance and Audits
Choose the Right VAPT Services Provider
How to Choose a Penetration Testing Vendor Wisely?