What is Pentesting?

What is Pentesting/Penetration Testing?
Pentesting is a robust security assessment and threat detection protocol that focuses on proactive testing to eliminate weaknesses or gaps within the architecture. Pentesting teams work with security heads and technical leads, to prepare comprehensive penetration tests that uncover hidden vulnerabilities.
Pentesting is a key component of the greater Vulnerability Assessment and Penetration Testing (VAPT) practice that every enterprise should engage in. While vulnerability assessment approaches cybersecurity from an assessment standpoint, pentesting focuses on actively discovering weaknesses from the point of view of a hacking entity.
Pentesting Definition/Meaning
Pentesting stands for penetration testing, which is an active breach assessment methodology to find weaknesses within the infrastructure. DevSecOps teams can perform pentests on several applications, systems, or networks to find vulnerabilities that need to be addressed. As pentesting is a simulation exercise, it’s important to replicate real-life situations, which are highly targeted and goal-oriented.
Penetration testing also enables firms to become more agile when it comes to cybersecurity measures. It enables them to focus on advanced hacking strategies, breaches, and how to stay abreast of the dynamic technology landscape. Additionally, it showcases weaknesses within the enterprise infrastructure that can be exploited by the right hacking methodology.
Why Penetration Testing?
Cybercrime may cost the global economy upwards of $6 Trillion a year by 2021, owing to the extent of deep-fakes, data breaches, AI-powered attacks, quantum hacking, and IoT breaches. While global initiatives may dictate best practices, it’s up to individual enterprises to secure their networks holistically.
Enterprises that regularly engage with penetration testing companies in India are more secure and are better prepared to respond to a security breach. Additionally, they’re in a better position to protect their reputation and comply with industry regulations & cybersecurity protocols. With over 38% of leaked data containing private security credentials, according to industry estimates, it’s critical to protect enterprises from large-scale breaches.
Leverages Cutting-Edge Hacking Methods
Small to mid-size enterprises are especially vulnerable to hackers that may perform advanced hacking tactics to gain access to their information. By working with penetration testing companies in India, companies can stay one step ahead of their industries, while protecting themselves against unauthorized breaches.
Protection Against Financial/Reputation Loss
Penetration testing companies in India helps enterprises protect sensitive information, both internal and consumer data, thereby dissuading hackers from attempting to breach. When companies actively scout for vulnerabilities within their systems, they’re better prepared to respond to an actual breach when it happens.
Saves Against System Downtime
Hacking attempts, breaches, and system failures bring the network architecture down for a significant period. It’s important to maintain consistent uptime, especially as enterprises scale up. Pentesting ensures that all processes continue to leverage the enterprise architecture, and breaches are quarantined from critical-use networks.
Aids In Ensuring Compliance
Several compliance measures are established by governing bodies, industry associations and consumer groups to protect against data loss and privacy leaks. By pentesting regularly, enterprises can ensure that they’re following the pre-requisites outlined within their specific industry.
Empowers Technical Managers
After several rounds of pentesting, technical managers and key decision-makers are more empowered about taking the right steps to prevent future attacks. They’re able to formulate better architectures and can develop a robust plan to tackle potential breaches.
Penetration Testing Tools
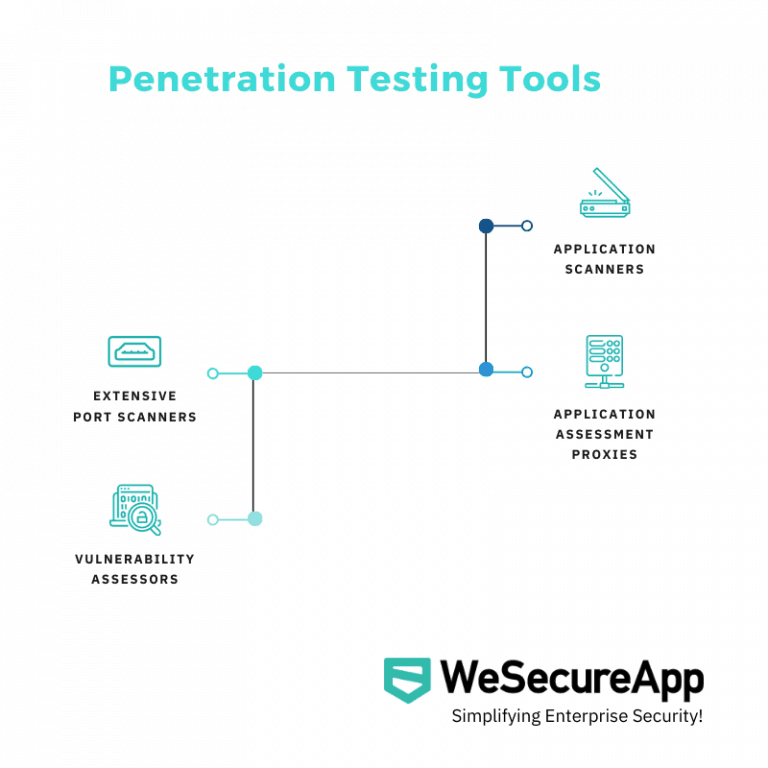
Several pentesting tools may be leveraged when developing a holistic cybersecurity plan. Global research suggests that close to 19.8% of all user computers were attacked by malware sometime last year. Enterprises need to use sophisticated pentesting tools to ensure that all devices and users are protected across the network.
It’s critical to leverage the right tools for the job to obtain insightful results. Whether red team testing or black box penetrating, all tests must be conducted within a comprehensive dashboard that showcases the relevant results with an executive summary.
Extensive Port Scanners
Port scanners may be used to gather information about a specific target. Several probing activities may be performed by port scanners to provide more information to the pentester performing the exercise. A detailed assessment can be made about the user, application or system, through which weaknesses can be highlighted.
Vulnerability Assessors
Pentesters can also leverage vulnerability scanning tools to find weaknesses within the target network or application. Both network-based and host-based vulnerability scanners may be leveraged to find critical weaknesses within the target. Back-door vulnerabilities, source code errors, and device exploits can be detected using these scanners.
Application Scanners
Application scanners can help discover security weak-points within applications that enterprises may be running. They’re the preliminary tool that many pentesters use to find gaps within the application’s cybersecurity measures. Memory overruns, SQLis, XSS exploits, and cookie manipulations can be leveraged to gain access to an application.
Application Assessment Proxies
Proxies may be used to track the data flow between the target web server, thereby gaining access via direct exploits. Pentesters can then read information flowing within the enterprise, as the proxy becomes the middleman between critical networks. By leveraging open-source and private proxy tools, pentesters can perform a range of direct attacks on the system.
Pentesting Training
Enterprises can work with the leading penetration testing companies in the pentesting space to learn more about penetration testing training. Through the technology, talent and tools provided, companies can understand the approach of pentesting from a holistic standpoint.
Testing protocols can also be initiated for employees that may be engaging in active pentesting. Enterprises can train internal staff members to run localized pentests to regularly scout for vulnerabilities that may exist. Additionally, staff members may be added to the team that come with extensive pentesting experience.
Penetration Testing Companies
The leading pentesting companies in India work with mid to large-size firms and protect their systems from hackers. While it’s important to perform robust pentests on systems, it’s even more so important to hire the right team to execute tests. The right team can transform incumbent practices, making organizations industry leaders in the space of cybersecurity.
That’s why decision-makers need to consult with the leaders in the space of cybersecurity, such as WeSecureApp – one of top penetration testing companies, to develop a comprehensive pentesting protocol. The leading firms in the space of auditing, assessment and protection work with technical teams to empower them with the right tools and strategic approach to reinforce systems.
Penetration Testing Methodology

Enterprises can work with key penetration testing methodologies to execute regular tests to enhance existing systems. Based on the critical testing methodology, a range of pentests can be executed to obtain insightful results. What’s important here is to work with a framework that fits well with the enterprise architecture adopted.
OSSTMM
The Open Source Security Testing Methodology Manual provides critical guidelines for pentesters to follow when conducting the appropriate tests. It’s a widely used standard that many enterprises leverage to strengthen their security systems. Network development teams also leverage the framework to develop firewalls and IT infrastructures.
OWASP
The Open Web Application Security Project is a cutting-edge methodology and framework for pentesters to adopt. With more than 66 controls within the architecture, the methodology allows pentesters to highlight specific issues in detail.
NIST
The National Institute of Standards and Technology (NIST) has a comprehensive guide for pentesting, which is widely used across banking, finance and technology. Pentesters work with network port/service identification and vulnerability scanning to find gaps within an enterprises’ infrastructure.
PTES
The Penetration Testing Methodologies and Standards guideline allows pentesters to get acquainted with the enterprise and their associated network. Testers can also perform post-exploitation testing to better prepare the enterprise from potential threats.
ISSAF
The Information System Security Assessment Framework contains the recommended guidelines to perform highly structured tests for large enterprises. It’s also a comprehensive standard to leverage when working with multiple processes, teams and specializations.
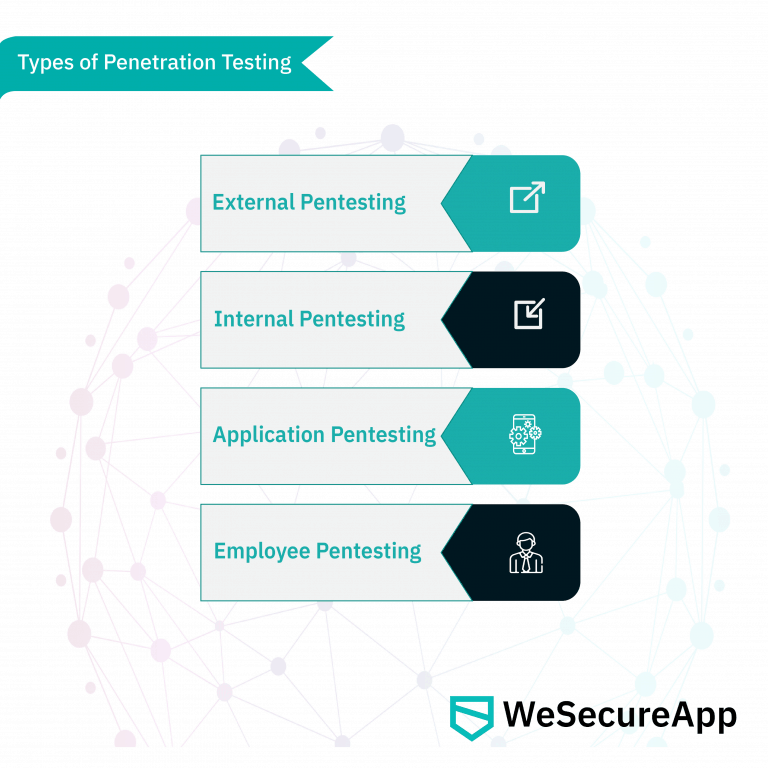
Types of Penetration Testing
Several pentesting methodologies may be executed individually or simultaneously, depending on the results required for the enterprise’s infrastructure. Based on the results acquired, the appropriate corrective strategies can be enforced, and the systems architecture can be upgraded.
External Pentesting
Enterprises may opt for an initial external pentest, which aims to hack into systems off-site. This simulates real-life approaches that hackers may use to gain access to a network or system. Using black-box methods and unique pentesting tools, teams can attack various components of the enterprise infrastructure to gain control.
Internal Pentesting
Generally, white box pentesting measures are implemented to carry out internal pentest exercises successfully. They simulate an internal attack, performed by an employee, or an external breach that leads to internal access & exploitation. Additionally, internal pentests uncover often neglected sections of cybersecurity measures, which is why they’re critical to perform regularly.
Application Testing
Specific applications may also be tested, prior to launch, to test various vulnerabilities that may be present. Application testing may extend to finding bugs within the source code, attempting database hacks, or stealing information via keystroke capturing. Application testing is critical when enterprises are highly product-focused.
Employee Testing
Social engineering, phishing and email hacking are some of the more common pentesting methods used to discover vulnerabilities. These tests may be issued to find gaps within training effectiveness, technological firewalls, and end-point safety. Employees may be a critical source of security weakness, especially as they have access to a range of critical databases and systems.
Pentesting Steps
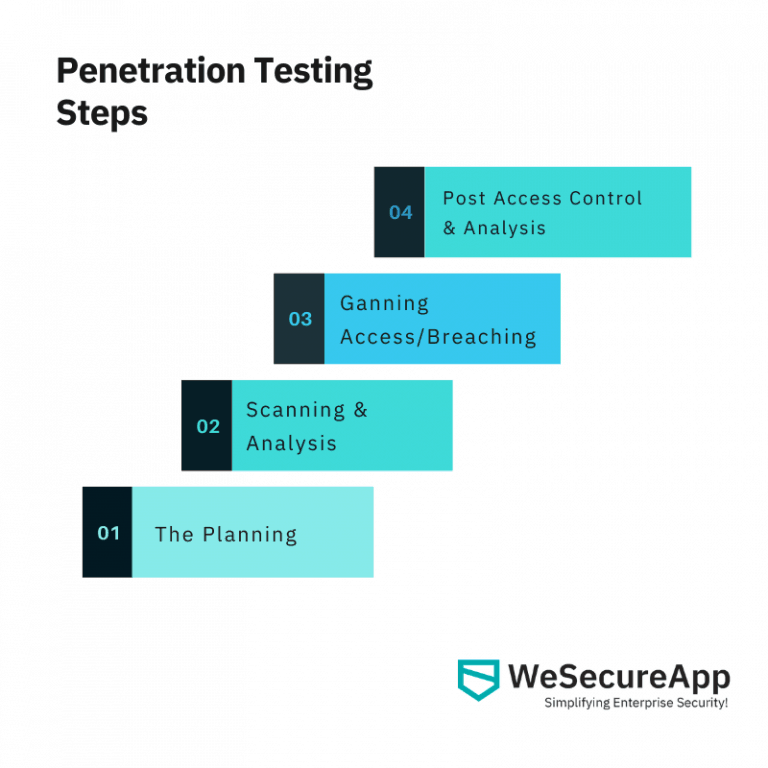
There are several phases through which pentesting is executed, which is why enterprises should work with the experts within the domain. While the planning stage is the most critical one, firms need to work through all stages in a focused manner.
The Planning stage
Enterprises can plan the scope of pentesting, whether enterprise-wide or locally focused, to obtain the necessary insights. Enterprises can also select whether they want to perform network service tests, web application tests, client-side breaches, etc. Additionally, black, white or grey pentesting methods are also implemented.
Scanning and Analysis
Testers can then start scanning targeted applications to find vulnerabilities that may be present. By leveraging static and dynamic scanning, an application or network can be targeted accordingly. Weak points can be discovered when they’re in a running or static state.
Gaining Access/Breaching
Based on the assessment performed, pentesters may proceed to gain access to databases, applications, systems or servers. By executing remote, client-side, server-side, or local exploits, testers can gain access to the system. They can then perform vertical privilege escalation to gain access to more secure zones.
Post-Access Control & Analysis
After the initial exploitation, pentesters try to maintain access control and perform several other internal breaches. This should provide enough information for final analysis, thereby showcasing multiple pathways to gain access to sensitive information.
Differences between Vulnerability Assessment and Penetration Testing
While a vulnerability assessment may incorporate a scan of the enterprise’s network and systems, a pentest is an active simulation of a cyberattack aimed to find vulnerabilities within the architecture. Both VA and PT are critical to performing regularly, to ensure that enterprises are protected long-term.
Technical managers must also perform a vulnerability assessment when onboarding new clients or working with new vendors. It’s also important to perform a vulnerability assessment when stakeholders are receiving access to databases under the enterprise’s cloud network.
Vulnerability assessments also must comply with standards and testing protocols that are outlined by the industry in which the firm is operating in. Common standards, such as ISO 27002 / ISO 27001, PCI DSS, SOX – Sarbanes-Oxley Act, & HIPAA – Health Insurance Portability and Accountability Act, outline protocols that all VAPT processes must adhere to.
When Is The Right Time to Get Pentesting Done?
The right time to have a complete pentest performed is prior to launching a new product into the market space. Additionally, it’s critical to perform regular pentests to ensure that your system architecture complies with best practices. Based on the evolving nature of your industry, it’s also important to update your pentest protocols so that you can remain protected.
With advanced hacking strategies, such as blockchain/AI based breaches, ransomware, end-point hacking, and remote-work phishing, enterprises need to upgrade pentesting protocols regularly. Companies growing into new markets, geographies and sectors, must also perform pentesting to ensure that all systems, devices, applications and networks are free of vulnerabilities.
Can Pentesting Be Done Remotely?
Pentesting may be performed by remote teams, through scheduled assessments, analysis and reporting. Technology firms also regularly work with remote testers, to receive new insights on their system architecture. While not all red team and purple team engagements can be done remotely, a large portion of pentesting may be performed off-site.
Enterprises can also remote test applications and IoT devices, to find vulnerabilities within these connected networks. End-point devices can also be tested from across remote locations, by the experts in the domain of pentesting. Additionally, firms that leverage cloud networks and systems can also perform remote pentesting.
Schedule a Demo with one of the top Penetration Testing Companies in India – Talk to Our Delivery Head