- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
Social Engineering Attacks – Manipulating your thoughts to fall in trap
Social Engineering Attacks: The people using Emails and smartphones would be able to easily connect with this.
“YOU HAVE WON 1,00,000.00 Pounds or Dollars, We have to send an ATM which has a Balance of 5,000,000.00 EUROS to your address. Business Opportunity for investing 1,000,000.00 Dollars in your city. Your Number has been picked up for the lottery and you have won the whooping amount of 10,000,000.00 INR. and If you do not claim any of this then that amount will be given out as a Donation.”
You haven’t enrolled for any of this but still, you have won so much, in this fashion they manipulate your thoughts, and in the form of conversion, transmission, and transfer cost they loot you with thousands. Sometimes just to make this sound genuine, they even use the name of government offices like the Central Bank of the country, WHO, UNESCO, IMF, etc. So if you receive any message, email, or text with such a huge amount to be put in your hand, don’t be greedy, and ask them to donate the fund, as you don’t require them to fall into the trap.
These sorts of phishing emails, spear phishing, baiting, scareware type of attacks are called Social Engineering Attacks. In this, they manipulate your thoughts with extreme happiness, grief, or fear and try to influence you to pay them, share banking details and private information, and then they loot funds from your account, sometimes knowingly and mostly unknowingly.
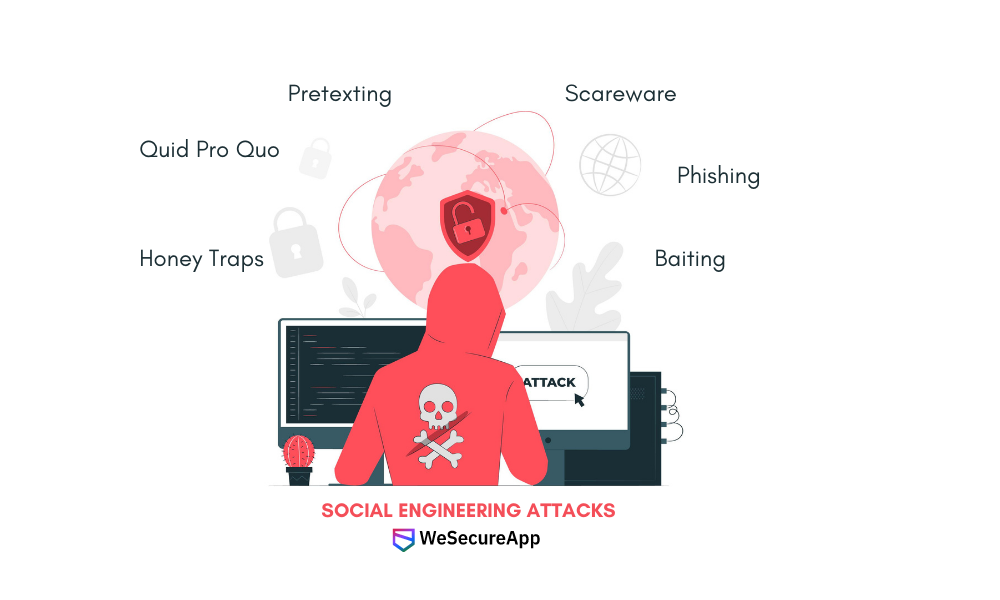
Let us learn about a few types of social engineering attacks:
-
Phishing
Phishing is one of the most common types of social engineering attacks that appears recently. Let us understand what it is exactly. In general phishing scams targets to accomplish three things:
Firstly they acquire personal information like names, addresses, and Social Security Numbers.
Secondly, they use shortened or misleading links that port users to malicious websites that host phishing landing pages just to capture data.
Lastly, they engulf threats, fear, and a sense of urgency in an attempt to maneuver the user into quick reverts.
Some basic ways to identify phishing attacks are known to us as poorly crafted to the extent that their messages suffer from spelling and grammar errors. Always sounds like a sense of urgency. But the ultimate goal of this mail is generally the same as using false websites or clear forms to collect users’ login credentials and other personal data.
-
Baiting
As the name sounds, baiting attacks are a bundle of false promises to exasperate a sufferer’s cupidity or curiosity. They lure victims into their jaws and collect their personal data or in other ways, they intrude into their systems with malware to do the same.
The most common and vastly used form of baiting attacks is the use of physical media to amplify the spread of malware. The cons keep their CD/DVD/USB sticks with labels like confidential data, payroll list, etc in bathrooms, elevators, parking lot, etc, so that victims get lured and use that media in the system and the whole network is infected.
Baiting scams are not limited to the physical world. Online formats of baiting consist of attractive ads that lead to malicious sites or that make users download a malware-infected application.
-
Scareware
This form of attack is just to scare the users. While browsing some data on the browser, scareware appears as a bombarding attack that raises false alarms and Imaginary threats. Users are forced to believe that their device is infected with some virus, and keep proposing that they install applications just for the purpose of benefiting the host and not the user.
Scareware is also dispersed via spam email that showcases false warnings or makes offers to users to update the software, buy worthless/harmful services which are not useful.
-
Pretexting
Pretexting is one such type of social engineering attack where bad actors draft very attractive and alluring past stories to attract the victims and make them believe that the story is true. Then they take advantage of the beliefs of the victim and make them spit out all their personal information.
As we see, phishing attacks target victims via the sense of fear and urgency to their benefits, while pretexting attacks are based on building false trust and exploiting victims via the same trustworthiness.
-
Quid Pro Quo (Something for Something)
As we see in baiting they use greed, Similarly in quid pro quo attacks the attackers promise a reward in exchange for information. These rewards usually come in the form of a service, on the other hand, baiting usually takes advantage in the form of goods.
It is necessary to note that attackers can use quid pro quo offers that are far less sophisticated than SSA-themed uses. In the past, this has been proven that people working in offices are willing to share their passwords for some cheap gifts or even a cup of coffee.
-
Honey Traps
In this, attackers usually target the person who likes to get involved romantically or sexually with someone online. Attackers pretend to be interested and probe that they won’t be able to talk without any fees. If you wish to talk with them you need to pay fees, and sometimes once fees are paid, they do not begin any video or chat, and the transaction shows as failed and no refunds are issued.
How to be safe from such attacks:
Do not trust communication from untrusted sources – When you receive such emails or SMS, never click on links mentioned in those communication channels.
Do not accept offers from strangers – If someone offers something that is impossible to accept from strangers, please switch your senses on, because nobody pays a huge amount for free to strangers
Being Vigilant – If you receive any media devices outside your company premises, first check with a particular department if they have missed any media device. On Non-confirmation, share those devices with your IT department to test and securely open the content of those media.
Keep your Antivirus updated – Always keep your devices loaded with anti-virus, and keep updating the same regularly so that whatever recent Viruses, trojans, malware, and Spyware are there in the market are away from your systems.
Draft Company Policies – Draft, Approve, and Train your employees with current Privacy & Information Security Policies of your organization so that people are aware of immediate actions in such cases, and try to avoid falling for such traps in case they identify being targeted.
For a complete understanding of social engineering services, drafting company policies, upgrading your systems to be capable of such attacks, contact WeSecureApp. We are experts in managing such attacks and keeping your people aware, conducting tests in the organization, and identifying whether people have understood whatever is coming their way.
We detect and prevent attacks by Social Engineering Services – Talk to Our Delivery Head