The Five Stages of the Red Team Methodology
What is Red Teaming?
Red Teaming is a multi-layered cyberattack simulation designed to test the efficiency of an organization’s security controls. This includes applications, networks, physical safeguards, and employees. It allows organizations to understand how repellent they are to real-world hacking challengers.
The intent of red teaming is similar to that of ethical hacking — actors don’t actually harm the system, but rather exploit vulnerabilities to improve its defenses. According to red teaming, it is impossible to truly assess a company’s system security until it has been attacked. Instead of running the risk of real-world damage from a malicious attack, simulating one first using a red team will uncover an organization’s vulnerabilities and enable them to be addressed before damage is done.
What’s a Red team exercise?
Preparing for a red-team exercise is the key to getting the most out of it. This includes knowing what and who will be involved. The processes and systems used by each organization are different, and a high-quality red team exercise needs to be specially customized towards finding susceptibilities in your systems. Hence, it is crucial to understand several factors.
Understand your system
First, it’s critical to know which processes and systems you want to test. For instance, you very well know you want to test a web application. However, you don’t have a sense of what a web application is, and which other systems are integrated with it. It’s vital to thoroughly understand your systems before you begin your red-team exercise.
Understand your network
You will be able to perform more accurate and specific red-teaming exercises if you quantify your testing environment. To maximize the value and effectiveness of your post-analysis, you should also know the technical specifications of your network.
Understand your budget
Red teaming can be done at different levels of severity, and a full spectrum simulated attack on your network can be expensive because it requires physical entry and social engineering for a thorough exercise. Hence, it’s crucial to know how much you are willing to invest in your red team exercise and adjust your scope accordingly.
Understand your risk level
Some organizations endure a high level of risk as part of their standard business procedures. Others, especially those in industries with comprehensive and complex compliance requirements, need a much lower risk tolerance. Red team exercises should focus on risks that can have a significant impact on your business.
The Benefits of Red Team Methodology
Following are the key benefits of executing the Red Team Methodology in an organization:
- A vulnerability assessment evaluates the organization’s defense system under several cyberattacks and helps it identify how secure its policies are.
- A Red Team Methodology helps to classify all assets according to their risk level.
- It helps to detect and expose all security vulnerabilities and loopholes in a system.
- Additionally, it maximizes the return on investment made in security. The red team evaluates how well the security system of your organization works when attacked.
The five stages of the red team methodology
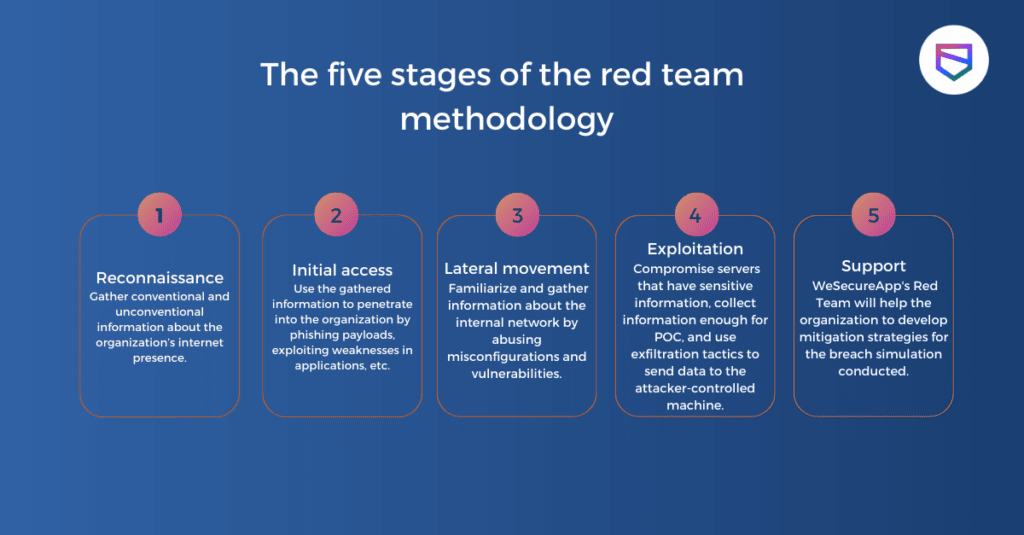
- Reconnaissance: Once the Red team is clear about their goals, they will start mapping systems to be targeted, including physical spaces, networks, employee portals, and web applications. Efficient attack planning involves the formulation of the operation that is specific to the target. This generally includes creating an initial plan of attack, threat modeling, identification of pretexts, crafting custom malicious file payloads, outlining potential alternative plans, prepping RFID cloners and badges, acquiring social engineering costumes, configuring hardware trojans, determining whether command and control will be in scope, creating falsified personas/companies, and much more.
- Initial access: The first stage in a Red Team operation is to determine the rules of engagement with the client to lay out the objectives and types of social engineering, physical, and cyber-attacks that are permitted to be carried out. This process will help the security team to identify all goals to be achieved. Whether that is to gain access to HR’s sensitive data or to obtain physical access to the server room. Once the goals are mapped, the Red Team will begin the engagement.
- Lateral Movement: Actions on objectives occur through lateral movement throughout the physical facilities and the cyber environment. Pivoting from compromised systems and violating security controls all along through capturing audio, video, and photographic evidence to support each of the discovered findings. Red teams try to move inside your system to attain their primary goal and verify if there are additional susceptibilities to exploit. Red teams will escalate continuously till the target is achieved.
- Exploitation: At this stage, the actual action in Red Teaming exercises really begins. The red team will aggressively work to accomplish the assigned goal to “break-in” or compromise servers/apps/networks, bypass physical controls (i.e., gates, fences, locks, radar, motion detection, cameras), and exploit the targeted staff face-to-face, through social engineering, phone phishing, email phishing, or SMS. Red Team will analyze cybersecurity susceptibilities and implant hardware trojans for remote network diligence. As soon as access is established, Red Team security’s ethical hackers will work to acquire physical or cyber persistence. This is done through privilege escalation on compromised shells, servers, locked-picked doors, usage of physical key impressions, and malicious file payload installation.
- Support: Once the assessment is done, Red Team security consultants will start compiling the information collected from all the stages of the engagement to deliver a comprehensive report outlining where your defensive team performed and where they were unsuccessful. They will also highlight the vulnerabilities that need to be addressed and will also offer recommendations to enhance the company’s security posture.
Conclusion
Skilled Red Teams use wide-ranging techniques to execute each of these steps. The most important thing to remember while evaluating the attack is that small susceptibilities in single systems can build into disastrous failures when chained together. Real-world hackers are greedy and always exploit more data and techniques than they originally intended. WeSecureApp has chosen a hybrid strategy in which we implement the OWASP methodology while creating unique red team vs. blue team test cases based on the application’s business logic. To provide complete end-to-end security, these use cases differ from client to client.
Want a Quick Red Team Assessment? – Get in Touch