VoIP Uncovered: A Guide to Services, Infrastructure Setup, and Reconnaissance
Voice over Internet Protocol (VoIP) has revolutionized voice communication by enabling calls over the Internet. It offers cost-effective solutions and is widely used in customer care services. In this first part of our VoIP series, we delve into the world of VoIP, exploring its services, toolkit setups, reconnaissance techniques, and common security test cases and exploitations. We will discuss VoIP protocols, the SIP connection structure, setting up VoIP infrastructure, essential components, and the importance of reconnaissance in penetration testing. So let’s get started on our journey to understand the fundamentals of VoIP.
VoIP, enables voice communication over the Internet. It’s popular in customer care services. By using softphone software, businesses can make cost-effective calls. This VoIP series of articles explores the VoIP services, toolkit setups, reconnaissance, common VoIP security test cases and exploitations.
VoIP Protocols:
- SIP (Session Initiation Protocol): Establishes multimedia sessions for voice, video, and messaging.
- SIPS (SIP Secure): Encrypts signaling messages to ensure secure communication.
- RTP (Real-time Transport Protocol): Transmits real-time media, such as voice and video.
- SRTP (Secure RTP): Enhances RTP security with encryption and authentication mechanisms.
SIP Connection Structure
A typical SIP interoperability structure consists of the following elements also shown in the image below:
- Sender initiates INVITE request
- Recipient answers 100 (try calling)
- The sender starts calling by sending a 180 response (Ring)
- Receiver picks up the phone and sends 200 successful responses (OK)
- ACK sent by the initiator
- The call starts using RTP
- A BYE request is sent to end the call
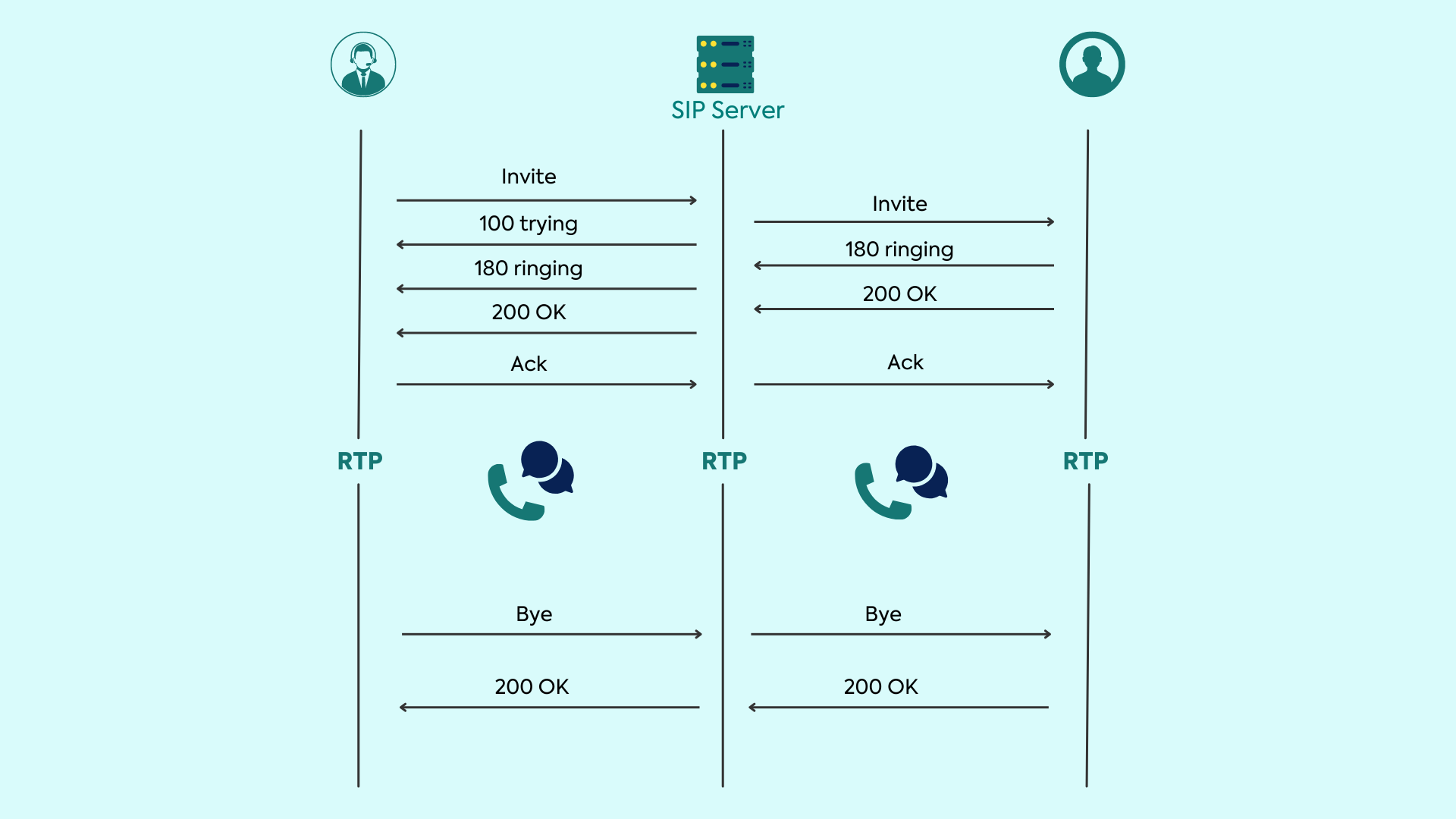
In a typical call initiation:
- Caller sends an Invite Packet to the callee.
- Caller receives a 100 Trying message followed by a 180 Ringing message from the callee.
- Callee answers the call, and the caller receives a 200 OK response, indicating a successful connection.
- At the end of the conversation, a Bye packet is sent.
- A 200 OK response acknowledges the Bye packet, confirming the termination of the call.
Setting Up VoIP Infrastructure
To establish and initiate VoIP calls from our system, there are essential components and settings that need configuration. Primarily, we require an SIP domain and a softphone.
The SIP domain is typically provided by VoIP service providers, offering a server or domain where we can create our account. This account includes credits for making calls and customizable settings, such as:
- Selecting countries for call destinations
- Configuring a default audio clip to play at the beginning of each call
- Setting up a voice mailbox
- Enabling messaging options

For SIP server settings, adjust within the server. Choose from Zoiper (paid/free), PhonerLite(free), or LinPhone (free) for softphone options. After obtaining the server, creating an account, acquiring call credits, and setting up the softphones, we’re ready to make calls. Conduct testing calls to ensure connection stability. Once confirmed, proceed to Penetration Testing.
VoIP Test Cases
VoIP test cases are based on:
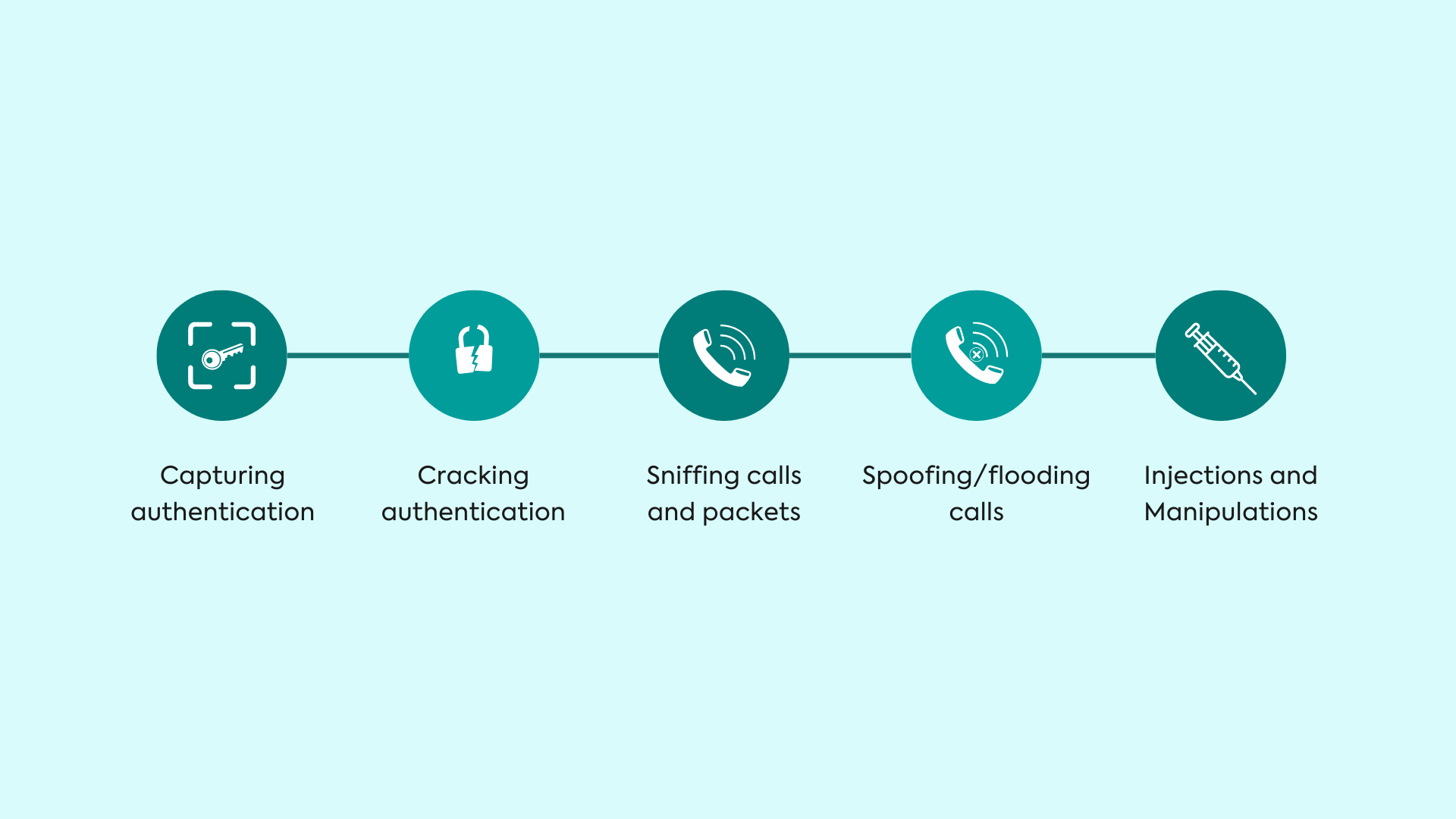
Some of these attacks are done on the SIP server itself and others are performed as MiTM (Man-in-the-Middle) attacks. Depending on the aspect of the project, we won’t be able to perform some of these attacks for example VLAN hopping. Until or unless the target infrastructure is using VLAN or not is a dependency at this point.
Tools Used
There are a lot of tools out there that are used in SIP testing. Here is a list of tools that are easy to use, their results are easy to understand and they are open-source:
Recon
During the initial phase of a penetration testing assignment, conducting reconnaissance (recon) is crucial. Reconnaissance involves gathering information about the target to gain a comprehensive understanding. In the case of SIP recon attacks, our main objective is to determine the SIP server being utilized.To accomplish this, various tools are available to assist in obtaining the required information. One particularly valuable tool is “sippts,” which offers a range of functionalities tailored for SIP testing.
Within this toolkit, there is a Python script named “sipping” that verifies the availability of the SIP server by sending pings. Additionally, we have “sipscan,” which enables us to scan a domain or IP address to extract SIP-related details.
NOTE:- we will using demo.sipvicious.pro as our target here
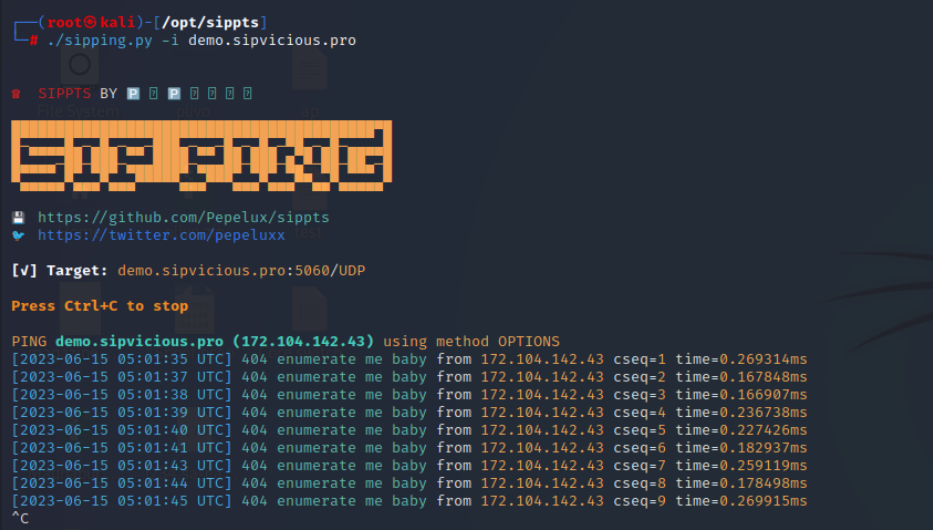
Figure 3: Pinging the SIP Server
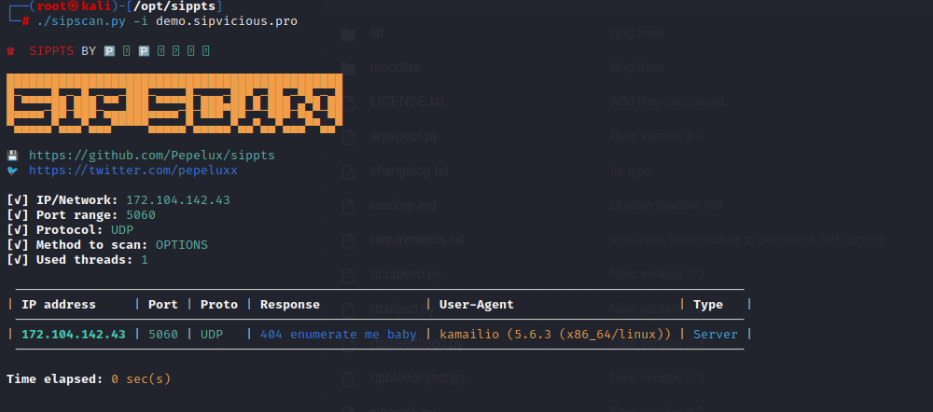
Figure 4: Scanning the SIP server
After conducting a thorough scan of the target, we have determined that the Kamailio server is being utilized. The SIP communication on this server is configured to use port 5060 with the UDP protocol. Now we would enumerate the extensions in use and try to harvest some numbers.
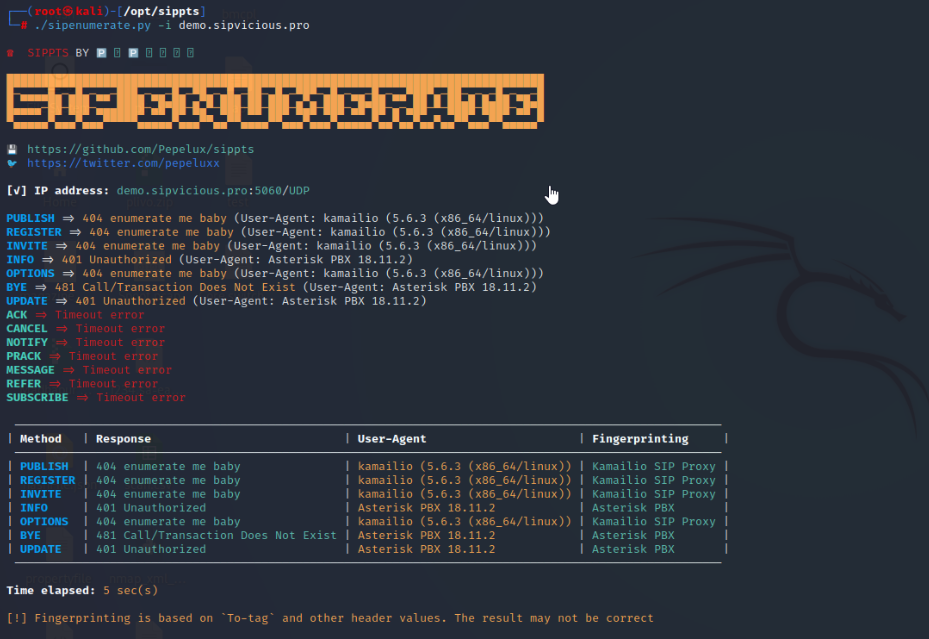
In this case we didn’t find any extension which is being used.
What does these tells us about the SIP server in use :-
- Is the server up and running or not?
- What SIP server is in use
- What are the allowed methods on this server
- What extensions are in use on this server.
All this information will help us in Auditing and exploiting the SIP server. We will talk about all the attack vectors and what those attacks can achieve in the next part of this article.
Stay tuned for part 2:
Now that we have understood about the VoIP service setup, test cases and recon methods, in the upcoming part 2 we shall explore the attacks and exploitation methods in detail.
Suggested Readings:
Securing the Future with Unparalleled Cybersecurity Solutions
A simple entry point can lead to Server Compromise
Cyber Security Maturity Assessment for NBFCs: WeSecureApp’s Approach