- Home
- Services
- Solutions
- Compliance
- RBI Cyber Security Framework For Banks
- SEBI Cyber Security & Cyber Resilience Framework
- UIDAI – AUA KUA Compliance Security
- RBI Guidelines for Payment Aggregators & Payment Gateways
- RBI Cyber Security Framework For Urban Cooperative Banks
- RBI Guidelines for cyber security in the NBFC Sector
- SAR Audit
- ISO27001
- PCI DSS
- GDPR
- Hipaa Audit
- SOC2 Assessment
- Resources
- Company
- Contact
The Rise of Cybercrime – An Overview
Cybercrimes are more rampant in the year 2022. The rate of cybercrimes is increasing every year, and it is expected to reach its highest next year. It is said that cybercrime affects the security of more than 80% of businesses throughout the world today. It is mainly due to the limited capabilities of authorities on monitoring cyberattacks because this type of crime is performed using the virtual world.
According to the cybersecurity stats, more than half of cyberattacks are done through ransomware attacks. The statistics further stated that healthcare databases are the most targeted because of their importance to businesses. Social media websites are also abused to spread malware and viruses or compromise sensitive information.

Source : Parachute
This blog discusses cybercrimes’ significant trends and developments such as ransomware, online privacy, and security. So, let’s get started.
1. Ransomware: Rise in Number of Attacks
In recent years, ransomware has been a significant threat to businesses worldwide. Upon infection, this malware holds valuable files on a system hostage by encrypting them until a certain ransom is paid in the form of bitcoins, transfers, or any other form of digital currency.
There are currently three types of ransomware:
- Crypto-ransomware, which encrypts files on a system.
- Locker ransomware locks a device’s screen until the money is paid.
- Wiper ransomware deletes files from a hard drive.
Experts believe that ransomware will become the easiest form of cybercrime next year due to the increasing trend for cryptocurrencies. It is expected to affect more than 8 million users or 10% of all internet users in 2022.
2. Online Privacy: Threats to Anonymity
The internet has provided different ways to communicate and express oneself. However, this freedom is abused by cybercriminals to violate the rights of individuals. Anonymity is one of their reasons for doing so since it provides them with an opportunity to remain undetected after performing illegal activities online.
Online privacy will be threatened next year due to the following reasons:
i). Around 43% of all data breaches involve small and medium-sized businesses. The numbers are increasing day by day. In 2021 alone, there have been 1,862 data breaches reported worldwide. It surpassed both 2020’s total of 1,108 and the previous record of 1,506 set in 2017.
ii). The top five most targeted platforms are popular social media sites, with Facebook coming first at more than 1 billion records breached.
iii). Cybercriminals rely on existing data breaches to target organizations because it is cost-effective for them to use stolen usernames and passwords in the process of login credential stuffing.
iv). Stolen information can also be sold online in the form of data breach marketplaces. Hackers can use social engineering to target individuals for cyberattacks because many users are still using the same passwords across different platforms.
3. Security: Numerous Threats Through IoT Devices
IoT refers to smart technology in appliances such as home appliances, watches, and other devices that perform various functions that can be controlled using a smartphone. The recent report indicates that there were around 35.82 billion IoT devices installed worldwide and by 2025 it will reach 75.44 billion. It will achieve numerous tasks at home or in the workplace. The most important feature of this technology is connecting different devices to let them work together.
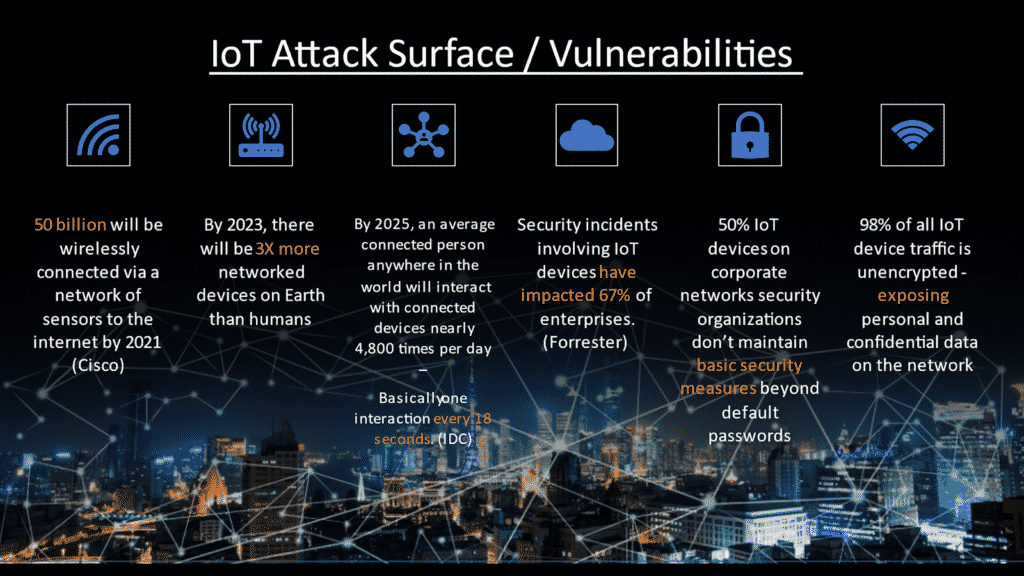
Source: Chuck Brooks
However, these IoT appliances are also a significant threat to individuals’ privacy and security. Two types of IoT-embedded devices can control other electronic features within a home, and wearable devices are worn on the body.
The following are some of the reasons why security will be threatened due to these devices next year:
i). Lack of security protocols in most IoT devices- Most manufacturers that produce IoT devices do not attach security protocols to their appliances due to the lack of knowledge on how it works. It means that these devices are more vulnerable to hackers, which will cause numerous problems in maintaining online privacy next year.
ii). Lack of transparency- Companies are known to make use of different technologies without providing users with an option to opt-out or know what information is being collected about them. It will lead to cases of data breaches, which may make individuals’ personal information vulnerable to cyber criminals next year.
iii). Hackers are expected to continue targeting IoT devices that use unsecured or outdated software systems- Hardware manufacturers need to consider embedding security protocols into their products before it is too late. This will make it more difficult for hackers to break into IoT devices and maintain the security of an individual’s data next year.
4. Online Attacks: Rise of cybercriminal activities
Online attacks will continue to pose a threat next year due to the following reasons:
i). The use of advanced technology in performing online attacks- Cybercriminals have been using new methods to perform illegal operations online, which has made it difficult for law enforcement agencies to track them down and learn about their activities.
ii). The use of IoT-connected devices in performing online attacks will increase next year due to the limited security protocols attached to these devices.
iii). The use of Artificial Intelligence (AI) in performing online attacks will be on the rise next year. Hackers are expected to use this technology to disrupt organizations’ computer systems, take control over other users’ devices, and steal sensitive data from their servers.
5. Social Media Platforms: Continuation of Privacy Issues
The following are the top social media platforms and how they will be used next year to threaten individuals’ privacy:
i). Facebook- This platform poses a threat to the online safety of its users because it collects information from third parties that support advertising campaigns on this website. The company then uses the collected data for targeted ads, making its members vulnerable to online scams and other cybercriminal activities.
ii). Instagram- This photo-sharing app collects users’ personal information and sells this data to third parties. It poses a significant threat to individuals’ privacy because cybercriminals can easily use the information collected for malicious purposes next year.
iii). Twitter- Cybercriminals may use the direct messaging feature of this platform to target specific individuals due to its lack of privacy measures.
iv). Snapchat- Hacked third-party apps allow cybercriminals to collect images and videos of individuals without their consent. This makes it easy for them to target the messages of specific users next year on this platform.
v). Google’s Android app store- Cybercriminals may use fake banking apps, game titles, crypto miners, and malware on this store next year due to its lax security protocols.
vi). Google Chrome- This browser collects information from individuals’ browsing activities and sells them to third parties, making it easier for hackers to steal data from specific users.
vii). YouTube- More cyber attacks will be launched against this platform next year due to the limited security protocols attached to its content. Hackers might use malware and phishing techniques from this website to access individuals’ data that they then sell illegally for profit.
viii). WhatsApp- Cybercriminals may use this messaging app to trick users into opening malicious links due to the limited security measures it uses when processing messages received by users.
6. Cybercriminal Markets: Continued Development of Dark Web-based markets
The following are the top dark web-based markets and how they will be used next year to threaten individuals’ privacy:
i). Dream Market- This is one of the most popular marketplaces on the dark web, allowing cybercriminals to sell various illegal products and services.
ii). Tochka- Cybercriminals use this Russian-based marketplace to sell illegal products and services on the dark web.
iii). Hansa Market- Cybercriminals use this market to sell leaked information next year due to its lax security protocols.
iv). The Pirate Market- This is a famous dark web market that allows cybercriminals to trade various illegal goods and services. Hackers may use this website to purchase malware next year to launch targeted attacks against specific individuals.
Conclusion
As we have seen, cybercriminal markets and social media platforms will pose a significant threat to users’ privacy next year. These platforms should take advantage of the latest security measures to protect themselves from online scams and other cybercriminal activities.
Related Articles:
Red Team Assessment versus Penetration Testing
Social Engineering – Manipulating your thoughts to fall in trap
Secure Code Review – A New Pace in Cybersecurity