Implementing Security for Applications in the Era of Microservices
In the world of advanced technologies and highly secured areas, the use of the microservices model is growing on a large scale for designing and deploying application systems in cloud-based, as well as enterprise infrastructures. The result of an application system consists of relatively small, loosely paired entities or components called microservices that communicate with each other through synchronous remote procedure calls or an asynchronous messaging system. Each microservice is a mini-application that has its business logic and various adapters for carrying out functions such as database access and messaging.
Encouragement of designing and deploying a microservices-based application system includes:
(a) agility in development due to relatively small and less complex codebases since each one typically implements a single business function;
(b) liberty to each team member in the development process to draft the codes due to no dependencies because of the loosely coupled nature of microservices; and
(c) easy connection to operational tools that provide infrastructure services such as authentication, access control, service discovery and Communication, and load balancing.
Inspite of several facilitating technologies, there have been lots of challenges to be addressed in the development and deployment of a microservices-based application. Network security, reliability, and latency are critical factors since every transaction implemented using this type of system will involve the transmission of messages across a network. Hence, the presence of one security lag in a microservices development phase exposes the whole application to the risk of a data breach.
The acceptance quotient of new technologies by Business House.
Businesses House seem to be very familiar with these. As part of their digital transformation, the introduction of new models requires a free mind and budget too, when it comes to new solutions. And they’re taking efforts and/or acquiring additional security measures with regards to keeping their environment secure.
For consideration, 67% of reviewed businesses run microservices/containers, of which 53% already have some sort of container security technology. 43% use a customized solution to secure their serverless functions during runtime so there are no breakdown and no data breaches.
While this may sound promising, it feels like businesses are taking the trial & error approach by stacking up multiple technologies, but not in the correct mindset which is necessarily optimizing their interoperability. Rather, they hope that having multiple solutions in place will do the job of operations & microservices security within their business function.
Best Practices of Microservices Security
-
Identity and access management.
Since microservices are packaged as APIs, the initial form of authentication to microservices involves the use of API keys (cryptographic). For authorization, a centralized architecture for provisioning and enforcement of access policies governing access to all microservices is required due to the sheer number of services, the implementation of services using APIs, and the need for service composition to support real-world business transactions (e.g., customer order processing and shipping). A standardized, platform-neutral method for conveying authorization decisions through a standardized token
-
Profiling of API as per deployment zones.
Malicious software and bugs often aim to uncover the competence of the service to a larger number of users than required. To be precise, only authorized personnel should have access to them. To avoid unwanted exploration, developers can define the roles of all the APIs in use based on which the users should be able to access them.
The API topology goes as follows:
Corporate Zone – traffic limited to organization employee;
Hybrid Zone – traffic limited to people with a common interest, deployments can be recorded at the data center;
DMZ – Demilitarized zone is a zone for filtering traffic originating from the Internet;
Ethernet – The application is exposed/available for everyone.
Access authorization to microservices APIs that have access to restricted data should not be accomplished simply by using API keys. Access to such APIs should require Multi-Factor authentication, tokens generating Pseudo-Random numbers that have either been digitally signed (e.g., client credentials grant) or are verified with an authoritative source. Additionally, some services may require either single-use tokens or short-lived tokens (tokens that expire after a short period) to limit the damage a compromised token can cause.
There is also a process called network segmentation. A segmented network allows developers to perform the distribution of traffic and illustrate different content to different user segments.
-
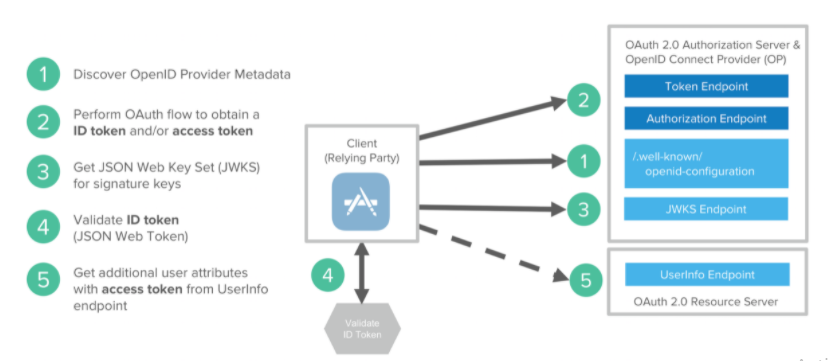
Use of Open ID or Oauth 2.0
The main task of these tools is to allow a developer to process user passcodes. OAuth 2.0 protocol significantly simplifies the process of securing microservices, even though it remains a highly challenging task.
-
Encryption of Sensitive data
Clear text is easy to read and copy by people and machines. While working on securing the data like Firm Confidential, Restricted data, Employee or Client PII – personally-identifying information – Application Drafting team needs to make sure that it is not being displayed as a plain text. All the passwords and usernames should be masked/hashed/encrypted during their storage in logs or records, so they are not readable to the person who reviews/monitors them.
However, extra encryption apart from TLS/HTTPS doesn’t add protection for traffic traveling through the wire. It can only help a little bit at the point where TLS terminates, so it can protect the packet that is carrying sensitive data (such as passwords or credit card numbers) from unintentional dumping into a request log.
Extra encryption might help you secure data against those attacks that target accessing the log files. But it will not help those who try accessing the memory of the application servers or the main data storage.
-
Implementing MFA
MFA means a need for additional verification information other than the password associated with the user id. One of the most common MFA that users encounter is one-time passwords (OTP). OTPs are the ones with 4-8 digit codes that are usually received via email, SMS, tokens, or some sort of mobile app. With OTPs a new code is replaced with another one after stipulated time or each time a user submits the request. The pseudo-random number is available based upon an intrinsic value that is assigned to the user when they first register and some other factor which could simply be a counter that is incremented or a time value.
-
Prevention from DOS Attack
It’s not a rare situation for applications to get sabotaged by DoS attacks. Those are attempts of sending an overwhelming number of service messages to cause website failure. Such attacks can showcase themselves in many different forms. They can target part of the application, or the entire platform and all levels of the network. Most of the DoS attacks concentrate on volumetric flooding of the network pipe.
There is a way to prevent huge numbers of API requests from causing the denial-of-service attack or other problems with API services. You need to set a limit on how many requests in a given duration of time can be sent to each API.
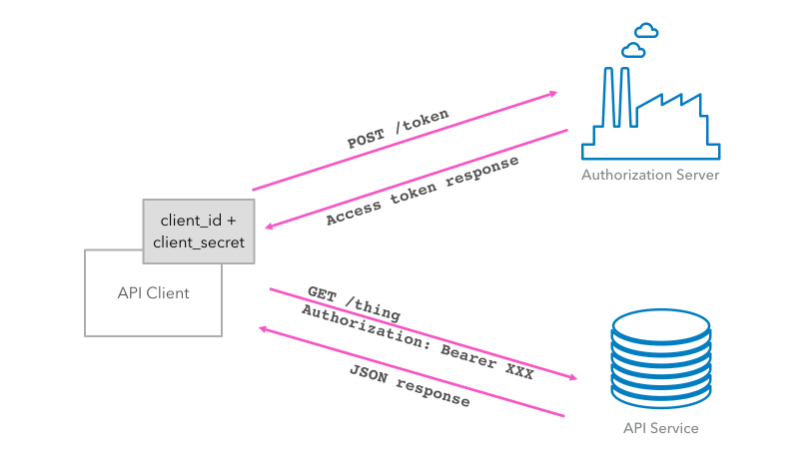
If in case the number of attempts reaches or exceeds the set limit, you can block the access from a particular API, at least for some reasonable interval. Meanwhile, look after to review the payload for threats. The limit for incoming calls from a particular gateway API should also be rate-limited.
-
Use Encryption Before determining the Data
We’ve already discussed additional encryption of sensitive data instead of showing it anywhere as plain text. As per the market standard, it is highly recommended that you encrypt the user data before creating and storing it in your database.
It is recommended to go for some strong cryptographic algorithms such as AES, RSA 2048+, or Blowfish. They make data transmission much safer. We should always be sure that the encryption algorithms are compliant with industry security standards.
Conclusion
As we discuss different processes of Microservices in the current digital environment, it’s security requirements are unconventional and require customized and business-specific solutions. We at WeSecureApp help you to provide the best security practices to protect your cloud & enterprise infrastructure in an ever-changing and dynamic technological world. We are always there to listen to your problems and serve you with the best and advanced security products as per your operations.