Stay HIPAA Compliant in this Work from Home Scenario
Have we wondered how much data we share whenever we walk to the doctor or a private hospital? This set of information is quite important and private to every individual. He / She doesn’t want to disclose this information as all the information or part of the information that one share with the doctor is private and shouldn’t want to be disclosed to anyone. This information is called e-PHI (electronic Personal Health Information).
What is HIPAA?
In the USA, HIPAA is a law to protect the privacy and security of individuals’ information, which lays down strict rules. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law that required the creation of national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge. The US Department of Health and Human Services (HHS) issued the HIPAA Privacy Rule and HIPAA Security Rule to implement the requirements of HIPAA.
Is HIPAA compliance a concern as Working from home is the new normal and will be for many healthcare employees for a while?
The COVID-19 pandemic has led most healthcare organizations to change their operating procedures and workflows to ensure critical business continuity. Among those efforts is a massive shift to remote work and care. The move, however, has made HIPAA compliance much more difficult. Protected health information must be managed properly whether the employee is in the healthcare facility or at home.
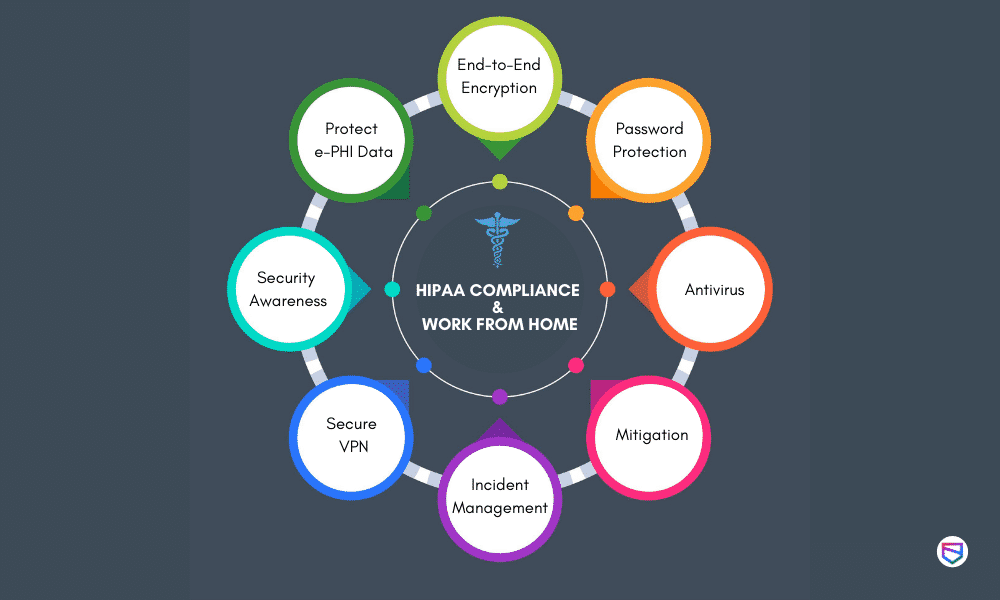
How to ensure that you remain HIPAA compliant in this new normal?
HIPAA compliance in the ‘Work from Home’ environment is a big task for every Healthcare business. Below are some of the tips which we at WeSecureApp feel should be addressed to remain compliant with HIPAA:
-
Ensure access to e-PHI data is properly managed and as per the roles and responsibilities
As HIPAA addresses concerns of protecting e-PHI data, the first step to securing it is to have proper access management controls to restrict any unauthorized user from gaining access to personal health information. Businesses should ensure that proper review of access rights is conducted for all the individuals handling the health information.
-
Security Awareness Programs to all employees
As employees are considered the weakest link and vulnerable to most of the social engineering attacks, there is always a need to have proper security Awareness programs to educate them towards recent attack vectors and threats. Employees should be made aware of different phishing attacks to prevent any compromise of health information. Also, employees should be made aware of proper work from home hygiene and security policies to be followed.
-
Address home network concerns
Ensure that employees using the home network are the only system administrator for the home network and all devices that connect to it. Next, ask employees to change the router’s password to a sentence or phrase rather than a single word. Lastly, home routers typically have two networks; put a work laptop on one and all other devices on the other.
The Hospital IT management team should make sure there exists a secure VPN tunnel with the latest software patches installed to enable the employees to access the hospital network. Confirm that IT security teams monitor and test VPN limits to prepare for an increase in the number of users and implement any modifications for users with higher bandwidth needs.
Implement multifactor authentication on all VPN connections (if MFA isn’t possible, ensure that remote staff is using strong passwords).
-
Establish robust incident management procedures
IT security team should ensure that there is a well-established Security Operations Centre to monitor daily incidents and attacks to address an increase in the need for security-related tasks — log review, attack detection and incident response and recovery ramping up due to sudden change in remote work culture.
-
Mitigate software-associated risks
Deploy the appropriate security software on all your devices. Manage the updates for all the applications and perform patching as per the schedules or immediately in case of emergency. Track the entire software inventory and restrict users from downloading and installing any unauthorized software. Perform periodic Vulnerability scans to detect any vulnerabilities in the application and network.
-
Have an Antivirus and data loss protection solution in place
Antivirus software is an important tool to help prevent malware attacks and detect major intrusions. But it is not restricted to only malware prevention only it detects all the infiltration and some may have recovery options as well which can recover data encrypted after the attack.
Also, the IT security team should make sure that the Data Loss Prevention tool is installed on all the systems to detect any data leakage incidents. Regular monitoring of the antivirus and DLP should be done to detect these incidents in time.
-
Everyone should follow video conferencing etiquettes
Set a password for every Zoom meeting. If sensitive material must be discussed in a meeting, ensure that the meeting name doesn’t suggest that it’s top-secret, thus making it a more attractive target for potential eavesdroppers. Restrict the sharing of sensitive files to the approved file-sharing technologies, not as a part of the meeting itself.
-
Ensure security practices are followed during Telehealth sessions
As pandemic has brought new technologies handy to all the users there is significant migration to telehealth software/applications. As remote work and care become even more common, tools such as these will become ever more critical to maintaining HIPAA compliance. End-to-end encrypted software communication would restrict the malicious attacker to eavesdrop on someone’s personal health information.
One should only collect data as required and refrain from collecting extra unnecessary data on these platforms.
While HIPAA compliance may seem apprehensive, a step-by-step approach can get you there efficiently. One should work with an experienced HIPAA compliance partner to make sure all the items on their HIPAA checklist — from understanding HIPAA to implementation and maintenance — are checked off properly.
WeSecureApp compliance team provides a one-stop solution for all your compliance needs and supports you throughout your HIPAA compliance journey – Talk to Our Delivery Head